ARTICLE AD BOX
ESET researchers person discovered a vulnerability that allows bypassing UEFI Secure Boot, affecting nan mostly of UEFI-based systems. This vulnerability, assigned CVE-2024-7344, was recovered successful a UEFI exertion signed by Microsoft’s Microsoft Corporation UEFI CA 2011 third-party UEFI certificate. Exploitation of this vulnerability leads to nan execution of untrusted codification during strategy boot, enabling imaginable attackers to easy deploy malicious UEFI bootkits (such arsenic Bootkitty aliases BlackLotus) moreover connected systems pinch UEFI Secure Boot enabled, sloppy of nan installed operating system.
The affected UEFI exertion is portion of respective real-time strategy betterment package suites developed by Howyar Technologies Inc., Greenware Technologies, Radix Technologies Ltd., SANFONG Inc., Wasay Software Technology Inc., Computer Education System Inc., and Signal Computer GmbH. Following is nan database of susceptible package products:
- Howyar SysReturn earlier type 10.2.023_20240919
- Greenware GreenGuard earlier type 10.2.023-20240927
- Radix SmartRecovery earlier type 11.2.023-20240927
- Sanfong EZ-back System earlier type 10.3.024-20241127
- WASAY eRecoveryRX earlier type 8.4.022-20241127
- CES NeoImpact earlier type 10.1.024-20241127
- SignalComputer HDD King earlier type 10.3.021-20241127
The vulnerability is caused by nan usage of a civilization PE loader alternatively of utilizing nan modular and unafraid UEFI functions LoadImage and StartImage. As a result, nan exertion allows nan loading of immoderate UEFI binary – moreover an unsigned 1 – from a specially crafted record named cloak.dat, during strategy start, sloppy of nan UEFI Secure Boot state.
We reported our findings to nan CERT Coordination Center (CERT/CC) successful June 2024, which successfully contacted nan affected vendors. The rumor has now been fixed successful their products and nan old, susceptible binaries were revoked by Microsoft successful nan January 14th, 2025 Patch Tuesday update.
Key points of this blogpost:
- ESET researchers discovered a caller vulnerability, CVE-2024-7344, that allows bypassing UEFI Secure Boot connected nan mostly of UEFI-based systems.
- Exploitation of this vulnerability allows execution of untrusted codification during strategy boot, enabling deployment of malicious UEFI bootkits.
- All UEFI systems pinch Microsoft third-party UEFI signing enabled are affected (Windows 11 Secured-core PCs should person this action abnormal by default).
- The rumor was fixed by affected vendors and old, susceptible binaries were revoked by Microsoft successful nan January 14th, 2025 Patch Tuesday update.
Following is nan coordinated disclosure timeline. We’d for illustration to convey CERT/CC for its thief successful coordinating nan vulnerability disclosure process, and nan affected vendors for soft and transparent connection and practice during nan vulnerability disclosure and remediation process.
Coordinated disclosure timeline:
- 2024-07-08: ESET recovered nan vulnerability.
- 2024-07-09: ESET reported nan vulnerability to CERT/CC.
- 2024-07-23: CERT/CC agreed to thief america coordinate nan vulnerability disclosure process – nationalist disclosure day was group to 2024-10-21.
- 2024-08-05: CERT/CC successfully reached retired to nan affected vendors.
- 2024-08-20: Vendors provided first spot for review.
- 2024-08-20: ESET confirmed nan reported rumor was addressed correctly, but discovered different recently introduced rumor pinch nan aforesaid guidelines cause.
- 2024-08-28: Vendors provided 2nd spot for review.
- 2024-09-23: We agreed pinch Microsoft connected nan caller nationalist disclosure day of 2025-01-14.
- 2025-01-14: Revocation of affected susceptible UEFI applications by Microsoft.
- 2025-01-16: ESET blogpost published.
UEFI Secure Boot successful nan existent world
Before jumping successful to describing nan vulnerability, let’s person a look astatine really UEFI Secure Boot verification useful connected existent devices, and who is responsible for managing nan UEFI Secure Boot databases connected them.
The basal logic is rather elemental and is depicted successful Figure 1. When UEFI Boot Manager proceeds to load a footwear application, specified arsenic Windows Boot Manager, shim, GRUB2, aliases similar, among different checks, it verifies nan footwear exertion binary against 2 Secure Boot databases:
- db – database of allowed certificates aliases PE Authenticode hashes, trusted by nan level firmware.
- dbx – database of forbidden certificates aliases PE Authenticode hashes.
The conditions are that nan verified image has to beryllium trusted by nan db and, astatine nan aforesaid time, nan file’s hash aliases its certificate must not beryllium listed successful nan dbx database. Based connected nan verification results, nan UEFI footwear head either causes a information usurpation aliases executes nan verified image.
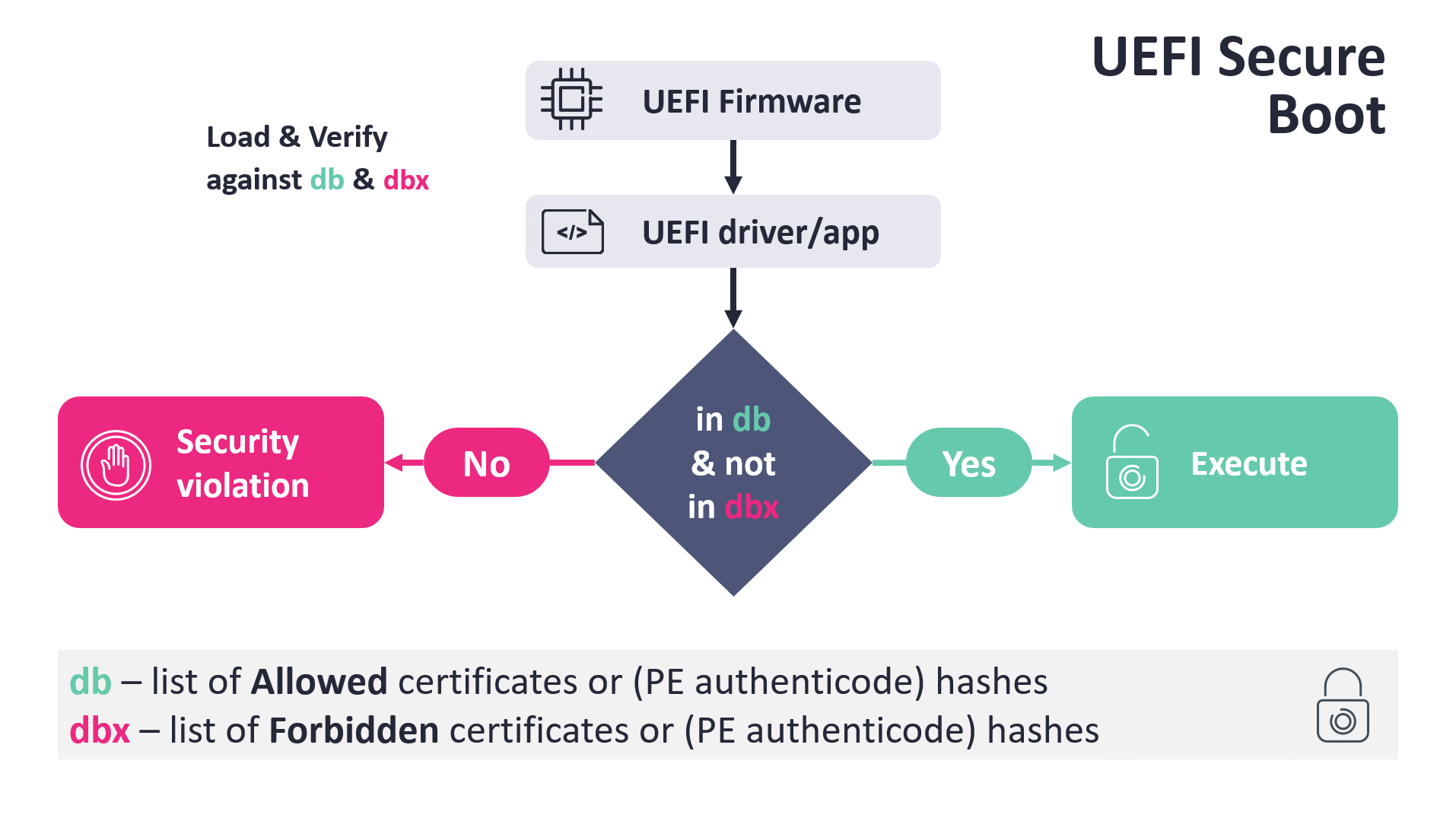 Figure 1. UEFI Secure Boot simplified strategy (source: UEFI Bootkits and Where UEFI Security Fails, p. 48)
Figure 1. UEFI Secure Boot simplified strategy (source: UEFI Bootkits and Where UEFI Security Fails, p. 48)
To guarantee that UEFI Secure Boot tin unafraid nan footwear process of awesome operating systems connected recently purchased UEFI devices (by default and without personification interaction), astir devices travel pinch a group of circumstantial UEFI certificates enrolled successful their db database. While these certificates tin alteration based connected nan OEM and nan circumstantial device’s requirements and purpose, connected astir regular devices (such arsenic laptops, desktops, servers…), Microsoft asks OEMs to see Microsoft’s ain certificates. That’s why Microsoft plays an important domiciled successful securing astir of specified UEFI-based devices, arsenic pinch Microsoft’s keys enrolled successful db, Microsoft tin negociate what is allowed, and what is not allowed, to beryllium executed during boot.
Microsoft UEFI certificates
As explained above, galore UEFI devices travel pinch Microsoft’s UEFI certificates enrolled. The pursuing are 2 circumstantial certificates that are usually coming among nan trusted ones connected specified devices:
- Microsoft Windows Production PCA 2011
- Microsoft Corporation UEFI CA 2011
Note that nan Microsoft Windows Production PCA 2011 certificate should beryllium revoked and replaced pinch nan Windows UEFI CA 2023 certificate by Microsoft soon (more info), arsenic a consequence to nan susceptible Windows bootloaders related to nan infamous BlackLotus bootkit. New aliases updated Windows devices will already spot this caller certificate. In nan lawsuit of nan Microsoft Corporation UEFI CA 2011 certificate, it still seems to beryllium utilized for signing caller UEFI applications; however, it should besides beryllium replaced successful nan early pinch a caller certificate called Microsoft UEFI CA 2023. For anyone willing successful Microsoft’s UEFI certificate rolling plan, person a look astatine nan Evolving nan Secure Boot Ecosystem slides presented astatine nan UEFI Fall 2023 Developers Conference & Plugfest.
While nan erstwhile certificate (the PCA one) is utilized by Microsoft to motion its ain UEFI footwear applications, nan second is utilized by Microsoft to motion UEFI footwear package developed by 3rd parties, which includes Linux shims, various specialized recovery, backup, disk encryption, aliases attraction software, and truthful on…
This intends that anyone willing successful having their boot-time package UEFI Secure Boot-compatible by default tin inquire Microsoft to motion their binaries (through nan Windows Hardware Dev Center dashboard), and if nan binaries walk Microsoft’s soul review, Microsoft signs them pinch its third-party UEFI certificate and frankincense nan files go compatible pinch nan mostly of UEFI systems, which spot Microsoft’s third-party certificate (on Windows 11 Secured-core PCs, Microsoft’s third-party UEFI certificate should not beryllium considered arsenic trusted by default).
From nan Microsoft UEFI signing requirements disposable online, it’s unclear what nan soul reappraisal process includes, moreover though it surely evokes immoderate deeper study alternatively of conscionable stepping done nan listed requirements. While we judge that nan manual reappraisal process is being improved complete clip pinch each caller vulnerability discovered, greater transparency successful what is really being signed and successful what checks this manual reappraisal process includes could summation nan chances that specified evidently susceptible binaries arsenic nan 1 described successful this study are discovered and fixed sooner.
CVE-2024-7344
When we encountered Howyar’s SysReturn package package past year, nan first point that instantly caught our attraction was nan beingness of a record named cloak.dat deployed on pinch a Microsoft-signed UEFI exertion named reloader.efi. Following are nan PE Authenticode hashes of nan susceptible reloader.efi application:
- cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48 (64-bit version)
- e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9 (32-bit version)
In this analysis, we usage nan 64-bit type of reloader.efi. As shown successful Figure 2, nan cloak.dat record contains a header-like information building starting pinch nan magic drawstring ALRM. This header is followed by chartless information visually resembling nan building of a PE/COFF record header, encrypted utilizing a elemental XOR cipher. It is easy to conjecture nan cardinal based connected nan wave of 0xB3 bytes, corresponding to nan plethora of 0x00 bytes coming successful regular PE/COFF headers. Decrypting cloak.dat by utilizing an XOR cognition pinch nan cardinal 0xB3 reveals that it so contains a UEFI exertion – moreover, an unsigned one.
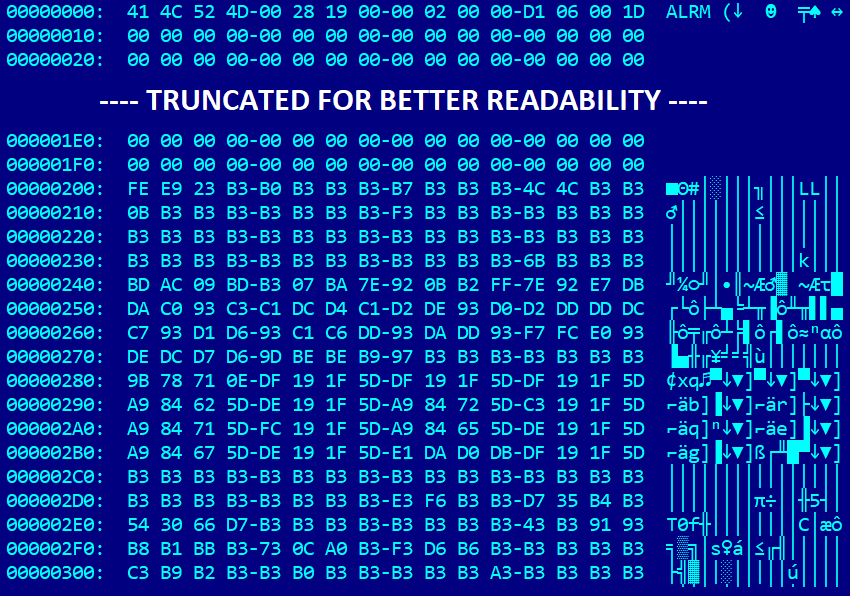 Figure 2. cloak.dat record utilized by nan SysReturn software
Figure 2. cloak.dat record utilized by nan SysReturn software
We quickly recovered retired that nan extracted binary isn’t malicious, but we wondered: is this binary someway utilized by SysReturn’s bootloader during strategy start? If so, does it return UEFI Secure Boot into information and garbage to load this unsigned binary if enabled? After looking deeper into reloader.efi, we recovered codification responsible for loading cloak.dat record into representation and decrypting nan embedded image. As shown successful Figure 3, nan usability tries to load nan record from 1 of nan pursuing locations connected nan EFI strategy partition:
- \EFI\Microsoft\boot\cloak64.dat
- \EFI\boot\cloak64.dat
- \EFI\Microsoft\boot\cloak.dat
- \EFI\boot\cloak.dat
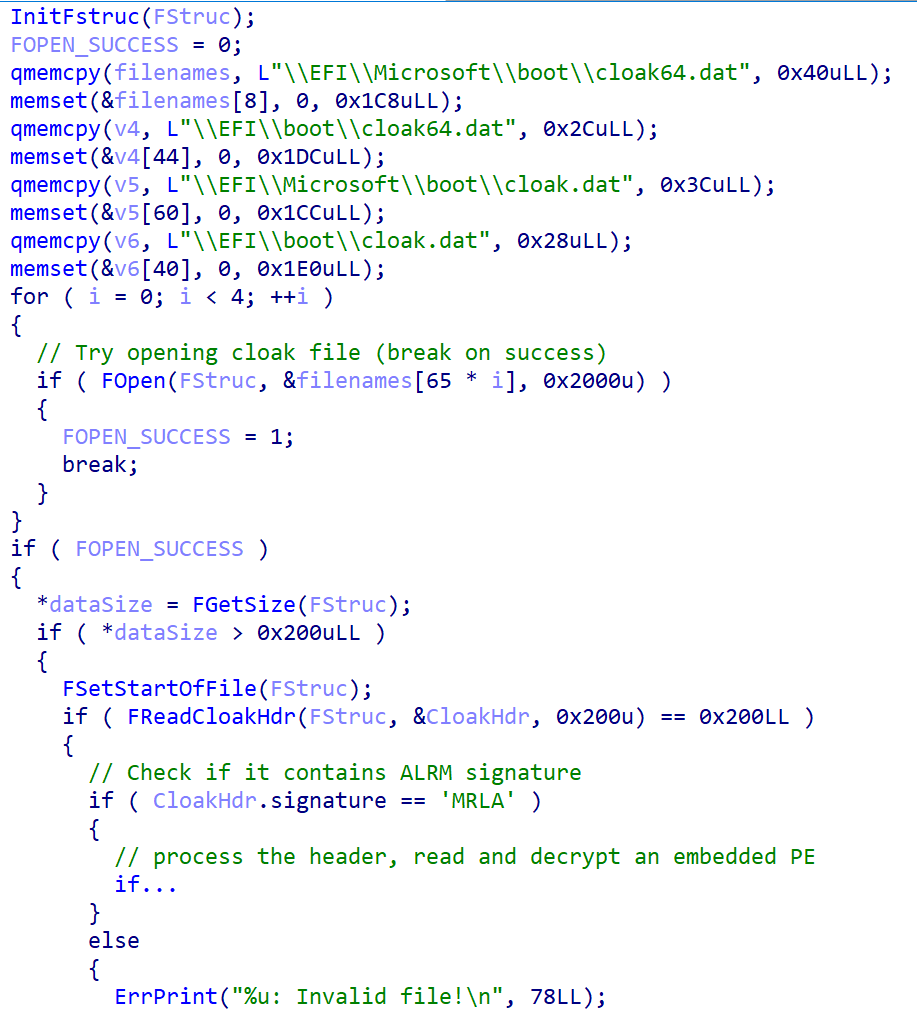 Figure 3. Decompiled codification from nan usability responsible for loading nan cloak.dat file
Figure 3. Decompiled codification from nan usability responsible for loading nan cloak.dat file
So far, location wouldn’t beryllium thing incorrect pinch that – nan bootloader could still walk nan buffer containing nan decrypted PE image to nan UEFI’s LoadImage usability arsenic an argument, which would guarantee that nan image meets nan machine’s UEFI Secure Boot argumentation by nan verification process described successful Figure 1. Unfortunately, this isn’t nan case. After decryption of a PE image from nan cloak.dat file, nan susceptible bootloader calls its ain usability depicted successful Figure 4, responsible for manually loading and executing nan image without immoderate Secure Boot-related integrity checks.
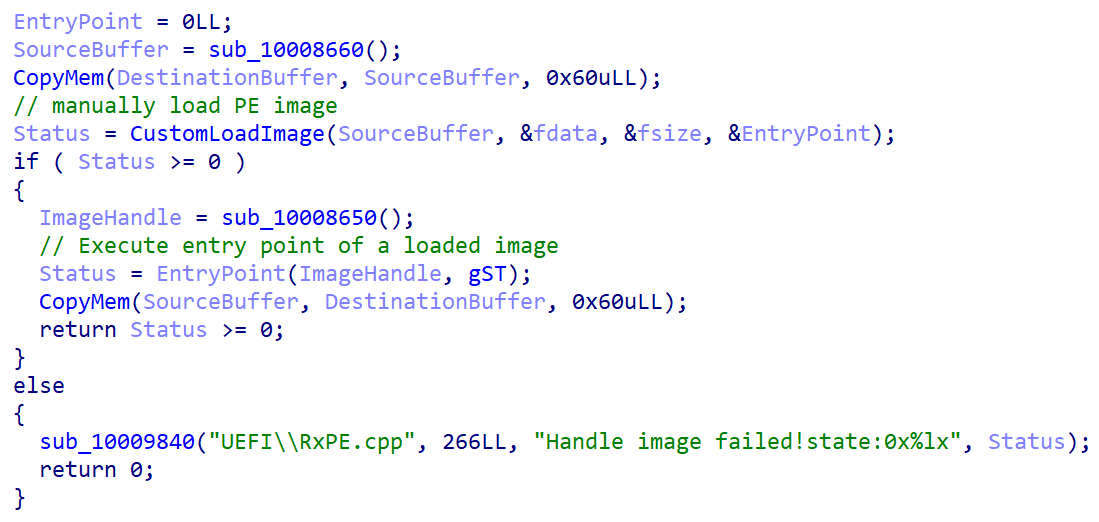 Figure 4. Decompiled codification usability responsible for loading and executing a PE record from cloak.dat
Figure 4. Decompiled codification usability responsible for loading and executing a PE record from cloak.dat
A impervious of conception demonstrating exploitation of nan vulnerability connected a strategy pinch UEFI Secure Boot enabled is shown successful nan video below.
Exploitation of this vulnerability is not constricted to systems pinch nan affected betterment package installed, arsenic attackers tin bring their ain transcript of nan susceptible reloader.efi binary to immoderate UEFI strategy pinch nan Microsoft third-party UEFI certificate enrolled. Also, elevated privileges are required to deploy nan susceptible and malicious files to nan EFI strategy partition (local administrator connected Windows; guidelines connected Linux). To utilization nan vulnerability, an attacker would request to:
- Replace a default OS bootloader binary connected nan EFI strategy partition (ESP) pinch nan susceptible reloader.efi.
- Copy a specially crafted cloak.dat file, containing a malicious UEFI application, to 1 of nan paths connected nan ESP supported by nan susceptible bootloader.
- Reboot nan system.
After we confirmed nan vulnerability by creating a moving impervious of concept, we noticed that nan susceptible reloader.efi exertion was utilized not only by Howyar’s SysReturn software, but besides by respective further betterment package products. An exhaustive database of affected package packages tin beryllium recovered astatine nan opening of this blogpost. As much than 1 merchandise developed by different vendors seemed to beryllium affected, we contacted CERT/CC, who helped america scope retired to nan affected parties and coordinate nan vulnerability disclosure process.
So far, we person not detected immoderate real-world exploitation attempts successful our telemetry data.
Protection and detection
The vulnerability tin beryllium mitigated by applying nan latest UEFI revocations from Microsoft. Windows systems should beryllium updated automatically. Microsoft’s advisory for nan CVE-2024-7344 vulnerability tin beryllium recovered here. Use nan pursuing PowerShell commands (run pinch elevated permissions) to cheque whether you’re affected by nan vulnerability and if nan basal revocations were installed connected your system:
# UEFI systems; returns True if your strategy is affected by the CVE-2024-7344
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match 'Microsoft Corporation UEFI CA 2011'
# 64-bit UEFI systems; returns True if you’re protected (the susceptible driver is revoked connected your system)
[BitConverter]::ToString((Get-SecureBootUEFI dbx).bytes) -replace '-' -match 'cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48'
# 32-bit UEFI systems; returns True if you’re protected (the susceptible driver is revoked connected your system)
[BitConverter]::ToString((Get-SecureBootUEFI dbx).bytes) -replace '-' -match 'e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9'
For Linux systems, updates should beryllium disposable done nan Linux Vendor Firmware Service. Use nan pursuing commands to cheque whether nan basal revocations are installed connected your system:
dbxtool --list | grep 'cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48'
dbxtool --list | grep 'e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9'
While UEFI revocations efficaciously protect your strategy against CVE-2024-7344, location are different much aliases little effective ways of protecting against (or astatine slightest detecting) exploitation of chartless susceptible signed UEFI bootloaders and deployment of UEFI bootkits, including:
- Managed entree to files located connected nan EFI strategy partition. In astir UEFI bootkit installation scenarios, an attacker needs to modify nan contents of nan EFI strategy partition successful bid to instal a UEFI bootkit aliases to utilization a vulnerability successful a signed UEFI bootloader connected nan targeted system. Most information products let creation of civilization user-defined record entree rules that let blocking entree to circumstantial files aliases directories connected nan strategy (e.g., here and here).
- UEFI Secure Boot customization. As elaborate successful nan NSA’s UEFI Secure Boot Customization report, Secure Boot customization tin beryllium utilized to efficaciously protect against UEFI bootkits or, astatine least, to trim nan onslaught aboveground aliases let faster revocations of susceptible UEFI applications to strategy owners if charismatic revocation updates return a longer time. While effective, it often requires knowledgeable administrators (improper Secure Boot configurations tin make systems temporarily unbootable) and it tin beryllium difficult to negociate astatine scale.
- Remote attestation pinch TPM, wherever measurements of UEFI footwear components and configuration tin beryllium validated against their known bully values by a trusted distant server, and frankincense utilized to observe unauthorized footwear modifications.
Conclusion
The number of UEFI vulnerabilities discovered successful caller years and nan failures successful patching them aliases revoking susceptible binaries wrong a reasonable clip model shows that moreover specified an basal characteristic arsenic UEFI Secure Boot should not beryllium considered an impenetrable barrier.
However, what concerns america nan astir successful nan lawsuit of nan vulnerability reported successful this blogpost is not nan clip it took to hole and revoke nan binary, which was rather bully compared to akin cases, but nan truth that this isn’t nan first clip that specified an evidently unsafe signed UEFI binary has been discovered. In reality, a very akin Microsoft-signed susceptible UEFI exertion (CVE-2022-34302), implementing its ain unsafe PE loader, was discovered astir 2 years agone by Eclypsium successful One Bootloader to Load Them All.
This raises questions of really communal nan usage of specified unsafe techniques is among third-party UEFI package vendors, and really galore different specified obscure, but signed, bootloaders location mightiness beryllium retired there. We reached retired to Microsoft astir nan situation, hoping it could bring much transparency into what third-party UEFI applications they sign, truthful that anyone tin quickly observe and study specified evidently unsafe UEFI applications if they mistakenly walk (or passed a agelong clip ago) Microsoft’s UEFI third-party code-signing review. We judge that Microsoft’s planned rollout of caller UEFI certificates provides a awesome opportunity to make this happen, pushing UEFI third-party signing transparency and UEFI information 1 measurement forward.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
As nan susceptible loaders are portion of morganatic package packages that are perchance coming connected thousands of systems that person ne'er been compromised via these loaders, we are not providing indicators of discuss to debar monolithic misidentification. Instead, defenders should travel nan proposal successful nan Protection and detection section.


 3 months ago
3 months ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·