ARTICLE AD BOX
Midnight Blizzard (APT29/Cozy Bear) targets European embassies and Ministries of Foreign Affairs pinch blase phishing emails disguised arsenic vino tasting invitations. Learn astir nan caller GrapeLoader malware and nan updated WineLoader backdoor deployed successful this campaign.
The notorious group of Russian government-backed hackers from nan Midnight Blizzard, APT29, aliases Cozy Bear, person been attempting to infiltrate European diplomats’ machine systems since January, sending retired clone emails to embassies and negotiated organisations crossed Europe.
Researchers astatine Check Point Research (CPR), who person been search this activity, discovered that hackers are utilizing a caller malware called ‘GrapeLoader’ to summation entry, followed by installing an updated, sneakier type of a backdoor programme called ‘WineLoader’ erstwhile inside.
The onslaught starts pinch emails that look for illustration they are charismatic invitations from a country’s Ministry of Foreign Affairs, inviting group to vino tasting events. Check Point’s study showed that almost each nan emails utilized nan taxable of wine-tasting events, and if nan first email fails, nan hackers nonstop much to instrumentality nan user.
This run “appears to beryllium a continuation of a erstwhile 1 that utilised a backdoor known arsenic WINELOADER,” documented by Zscaler successful February 2024.
The emails, sent from 2 website addresses, bakenhofcom and silrycom, contains a malicious nexus that initiates nan download of a record named “wine.zip.” When opened, it runs 3 files, including a disguised record called “ppcore.dll” that acts arsenic nan GrapeLoader program.
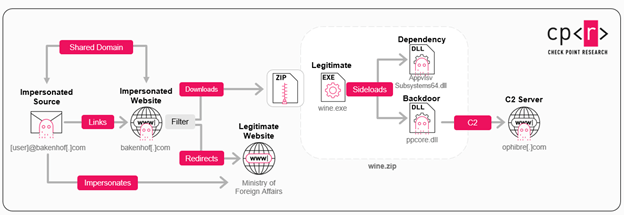 Campaign Overview (Source: Check Point Research)
Campaign Overview (Source: Check Point Research)GrapeLoader copies nan contents of nan “wine.zip” record to a caller location connected nan computer’s difficult thrust and changes nan computer’s settings to automatically tally a programme called “wine.exe” each clip nan machine is turned on, ensuring nan hackers support their access. It must beryllium noted that hackers are specifically targeting European Ministries of Foreign Affairs and embassies.
The WineLoader backdoor is simply a blase instrumentality designed to stitchery delicate accusation from infected computers, aiding hackers successful their cyber spying operations. Researchers discovered that this caller type is harder to observe owed to its code-hiding techniques, whereas its older versions were comparatively easier to analyse pinch automated tools.
The backdoor collects accusation specified arsenic nan computer’s IP address, programme name, Windows username, and process ID. This backdoor has been utilized successful erstwhile hacking attempts by Midnight Blizzard against diplomats, CPR highlighted successful their blog post.
Researchers picture GrapeLoader arsenic a comparatively caller instrumentality utilized successful nan early stages of this onslaught to stitchery accusation astir nan infected computer, guarantee hackers tin support access, and download nan adjacent shape of their attack, nan WineLoader backdoor. GrapeLoader uses various tricks to debar discovery by information tools, specified arsenic hiding matter wrong its codification and uncovering basal machine functions astatine runtime.
The cognition highlights nan evolving quality of cyber espionage and nan persistent threat posed by nation-state actors to negotiated communications and systems. This find serves arsenic a reminder for diplomatic organisations to stay alert, instrumentality stronger cybersecurity measures, and amended unit astir nan risks of blase phishing attacks.

 7 hours ago
7 hours ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·