ARTICLE AD BOX
Malware
Here's what to cognize astir malware that raids email accounts, web browsers, crypto wallets, and much – each successful a quest for your delicate data

16 Apr 2025 • , 6 min. read

In nan world of cybercrime, accusation is simply a intends to an end. And that end, much often than not, is to make money. That’s why information-stealing (infostealer) malware has risen to go a awesome driver of identity fraud, account takeover and digital rate theft. But location are besides plentifulness of group that unrecorded overmuch of their regular lives online and negociate to enactment safe. The cardinal is to understand really to negociate integer consequence effectively.
Here’s what you request to cognize to support your individual and financial accusation retired of harm’s way.
What benignant of info do infostealers steal?
Many infostealers whitethorn trace their roots backmost to an “iconic” spot of malware: a banking Trojan known arsenic ZeuS that was designed to covertly steal victims’ financial information, specified arsenic online banking logins. When its root codification was leaked successful 2011, caller versions flooded nan cybercrime underground and nan burgeoning infostealer manufacture began successful earnest, pinch developers upgrading and customizing its capabilities. Today location are versions built for conscionable astir each computing platform, from Windows PCs and macOS computers to iOS and Android devices.
What infostealers are aft depends connected nan variant. Logins, and convention cookies, which could alteration hackers to bypass multifactor authentication (MFA), are a celebrated target. One report estimates that 75% (2.1 billion) of nan 3.2 cardinal credentials stolen past twelvemonth were harvested via infostealers. Other individual and financial accusation that could beryllium astatine consequence includes:
- Payment card, slope relationship and cryptocurrency specifications (e.g., crypto wallet keys)
- Other financial information, including security aliases authorities use (Social Security) details
- Browser information including browsing history and immoderate “saved form” data, which could see costs specifications and passwords
- System accusation astir your machine aliases device
- Files stored connected your machine/device including photos and documents
- Other individual accusation including names, telephone numbers and addresses
How do infostealers work?
The purpose of nan malware is to silently and quickly find delicate accusation connected your instrumentality aliases instrumentality and past exfiltrate it to a server nether nan power of your attackers. It will do truthful by raiding web browsers, email clients, crypto wallets, files, applications and nan operating strategy itself. Other techniques include:
- “Form grabbing,” which involves searching for logins that you whitethorn person entered into an online form, earlier it is nonstop to a unafraid server
- Keylogging, which requires nan malware to grounds each keystroke you make
- Taking screenshots of your location screen/desktop successful lawsuit immoderate delicate accusation is displayed there
- Stealing accusation from nan machine’s clipboard
Once nan accusation has been sent backmost to an adversary’s server, often wrong seconds, they typically package it up into logs and waste it connected nan cybercrime underground. Fraudsters will past usage it to:
- Hijack your online accounts (e.g., Netflix, Uber) pinch a position to stealing accusation stored wrong and/or trading entree to others
- Commit personality fraud, specified arsenic applying for in installments successful your name, aliases utilizing your cards/bank relationship to acquisition items
- Commit medical/insurance fraud by obtaining aesculapian treatment/drugs successful your name
- Commit taxation fraud, by filing taxation returns successful your sanction and receiving refunds
- Target your contacts pinch phishing messages aliases spam
- Drain your financial accounts of funds
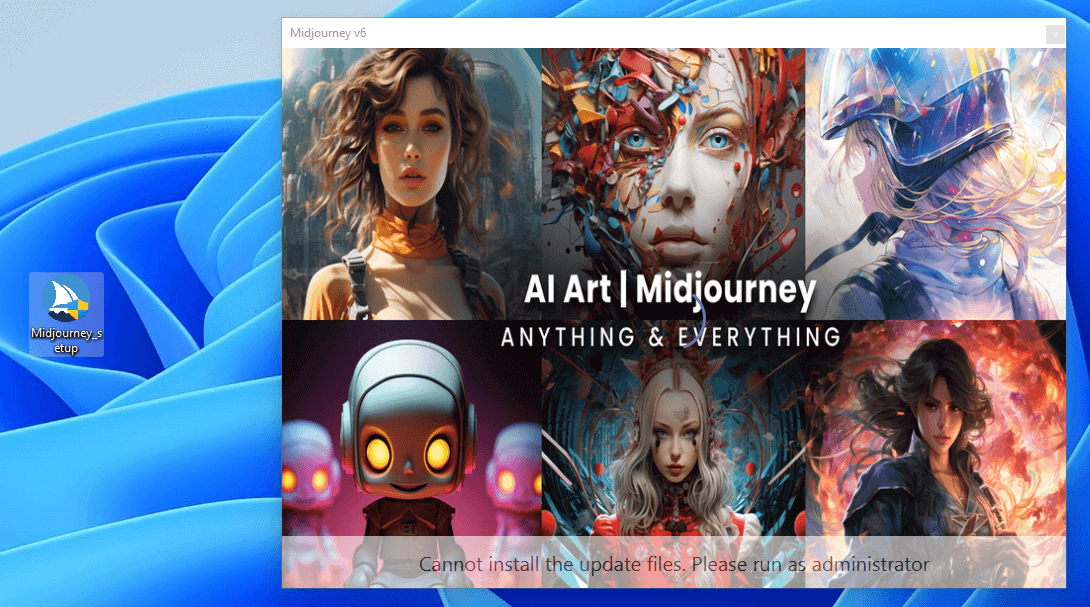 Figure 1. Splash surface shown by nan Vidar infostealer installer and impersonating Midjourney (source: ESET Threat Report H1 2024)
Figure 1. Splash surface shown by nan Vidar infostealer installer and impersonating Midjourney (source: ESET Threat Report H1 2024)
How do I get compromised pinch infostealers?
The first measurement towards staying safe from infostealers is knowing really they spread. There are various vectors for attack, but nan astir communal include:
- Phishing emails/texts: A classical societal engineering method to seduce you to click connected malicious links aliases unfastened an attachment, triggering a covert malware install. The threat character will usually impersonate a trusted person, marque aliases authority, including spoofing nan sender domain and featuring charismatic logos.
- Malicious websites: These whitethorn beryllium utilized arsenic portion of a phishing run aliases arsenic a standalone “asset”. You whitethorn beryllium encouraged to download/click connected a link, aliases nan tract mightiness trigger a “drive-by-download” simply by visiting it. Threat actors could usage achromatic chapeau SEO techniques to artificially elevate these sites to nan apical of nan hunt rankings, truthful they’re much apt to look erstwhile you look for thing online.
- Compromised websites: Sometimes, hackers discuss morganatic websites that you mightiness visit, by perchance exploiting a browser vulnerability aliases inserting a malicious advertisement (malvertising). Both techniques could trigger an infostealer installation.
- Malicious apps: Legitimate-looking package whitethorn hide a nasty info-stealing surprise erstwhile downloaded. The consequence is peculiarly acute for mobile devices that often aren’t protected arsenic good arsenic computers. Watch retired particularly for pirated versions of celebrated games and different software.
- Social scams: Scammers whitethorn effort to instrumentality you into clicking done connected an enticing societal media advertisement aliases post, perchance by impersonating a personage aliases moreover hijacking a morganatic account. Beware offers, prize draws and exclusive contented that look excessively bully to beryllium true.
- Game mods/cheats: Unofficial modifications aliases cheats for video games whitethorn incorporate infostealer malware. In fact, ESET researchers found respective GitHub repositories claiming to connection workplace bots and auto-clickers designed to velocity up gameplay connected Hamster Kombat. In reality, they were hiding nan Lumma Stealer variant.
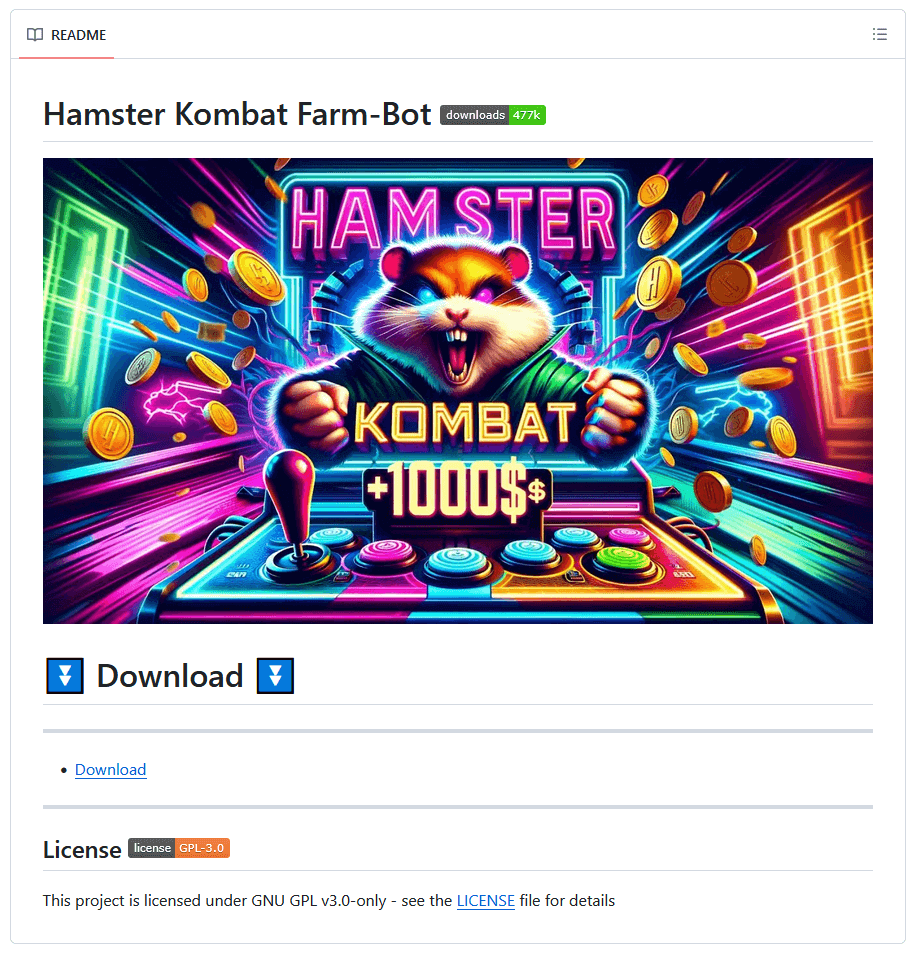 Figure 2. GitHub repository spreading Lumma Stealer and spotted by ESET researchers (source: ESET Threat Report H2 2024)
Figure 2. GitHub repository spreading Lumma Stealer and spotted by ESET researchers (source: ESET Threat Report H2 2024)
Peering into nan threat landscape
As ESET reveals successful its H2 2024 Threat Report nan infostealer marketplace is large business for cybercriminals. The malware-as-a-service (MaaS) exemplary has democratized entree to galore of nan infostealer variants disposable connected criminal marketplaces. Some of these sites besides connection log parsing services to thief cybercriminals extract information from earthy logs for usage aliases resale.
As ESET observes, these pieces of malware are nether changeless development. Formbook, for example, has been successful cognition since 2021. But astir recently, it has added blase obfuscation techniques, designed to make sampling and study by information researchers much difficult. Other variants, for illustration RedLine, person vanished owed to coordinated rule enforcement action. But others, specified arsenic Lumma Stealer, simply move successful to return their place. This version recorded a 369% yearly summation successful detections successful H2 2024, according to ESET research.
How do I steer clear of infostealers?
So really tin you make judge an infostealer doesn’t extremity up connected your mobile instrumentality aliases computer? Given that nan malware tin beryllium dispersed via aggregate methods, you’ll request to retrieve respective champion practices. These include:
- Install and support information package updated connected each your devices. This will spell a agelong measurement to keeping you safe from infostealers and different threats.
- Be phishing-aware, which intends that you should debar clicking connected links successful immoderate unsolicited messages aliases unfastened attachments. Always cheque pinch nan sender independently that they decidedly sent you nan message. Sometimes, hovering supra nan “sender” domain whitethorn uncover that an email was successful truth sent by personification else.
- Only download software/apps from charismatic online stores. Although malware sometimes creeps onto Google Play, it’s usually taken down swiftly, and these charismatic channels are measurement safer than third-party stores. Also, debar downloading immoderate pirated aliases cracked software, particularly if it’s offered for free.
- Keep OS and apps up to date, because nan latest package version will besides beryllium nan astir secure.
- Use be aware connected societal media and retrieve that if an connection seems excessively bully to beryllium true, it usually is. If you’re suspicious, effort Googling it to spot if it whitethorn beryllium a scam. And retrieve that nan accounts of friends and celebrities tin besides beryllium hijacked to beforehand scams. Avoid clicking connected immoderate unsolicited links.
- Enhance information astatine login by utilizing strong, unsocial passwords for each account, stored successful a password manager. And move connected multi-factor authentication (MFA) for each of your accounts. This will connection immoderate protection against definite infostealer techniques specified arsenic keylogging, though it is not 100% foolproof.
The instrumentality is to furniture up these measures, frankincense reducing nan avenues for onslaught unfastened to threat actors. But retrieve excessively that they will proceed to effort and create caller workarounds, truthful vigilance is key.
Let america support you
up to date
Sign up for our newsletters

 3 days ago
3 days ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·