ARTICLE AD BOX
Silent Push uncovers an alleged Russian intelligence phishing run impersonating nan CIA, targeting Ukraine supporters, anti-war activists and informants.
Cybersecurity researchers astatine Silent Push person discovered a analyzable and extended phishing operation, allegedly launched by Russian Intelligence Services aliases a likewise motivated entity, targeting individuals who support Ukraine and reason nan Russian government.
The campaign, which surfaced successful early 2025, employed clone website lures to stitchery individual accusation from Russian citizens and informants. This was a peculiarly delicate endeavour fixed nan illegality of anti-war activities wrong nan Russian Federation.
The phishing sites collected personification input utilizing a operation of fixed HTML and JavaScript. Data exfiltration was often facilitated done elemental POST requests to threat-actor-controlled servers aliases done nan abuse of Google Forms.
Researchers identified 4 chopped phishing clusters, each impersonating a salient organization: nan US Central Intelligence Agency (CIA), nan Russian Volunteer Corps (RVC), Legion Liberty, and Hochuzhit, an appeals hotline for Russian work members operated by Ukrainian intelligence.
Despite their divers impersonations, these clusters stock a communal objective: nan illicit postulation of individual data. As noted by nan morganatic Liberty of Russia Legion successful a March 14, 2024, X post, “We punctual you that nan only charismatic telegram transmission of nan Legion is listed connected our website: hxxps://legionlibertyarmy. Do not beryllium fooled by fakes. Do not autumn into nan traps of nan information forces of nan Putin regime!”
The threat actors utilized a bulletproof hosting provider, Nybula LLC (ASN 401116), to big phishing pages designed to mimic nan charismatic websites of these organizations. This tactic, on pinch nan usage of Google Forms and website forms to stitchery data, reveals a blase effort to deceive and extract delicate accusation from unsuspecting victims.
The campaign’s infrastructure study revealed interconnectedness crossed nan 4 clusters, pinch shared technicalities specified arsenic nan WHOIS statement sanction “Semen Gerda,” akin metadata, and communal registration done nan NiceNIC registrar.
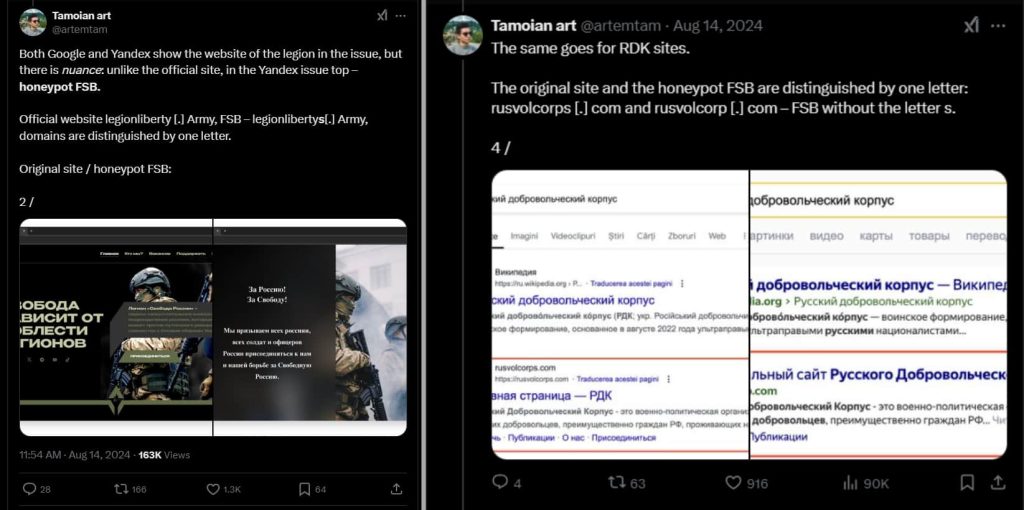
The phishing pages employed various strategies to lure victims. For instance, nan rusvolcorpsnet domain lured users pinch a “Join Here” button, starring to a Google Form requesting elaborate individual information. Similarly, nan legionlibertytop domain utilized a bluish “Join” fastener to nonstop users to a morganatic Google Form, while a greenish fastener led to a shape controlled by nan threat actors.
CIA impersonation progressive nan creation of domains for illustration ciagovicu and jagotovoffcom, which featured suspicious web forms and embedded illegitimate .onion links. The threat actors moreover manipulated YouTube content, replacing charismatic CIA links pinch their phishing domains.
Conversely, nan Hochuzhit cluster, targeting Russian work members seeking to surrender, utilized domains for illustration hochuzhitlifecom and hochuzhitlife. Silent Push Threat Analysts, successful collaboration pinch information interrogator Artem Tamoian, uncovered further domains and infrastructure, including legionllbertyarmy, which was hosted connected Cloudflare.
Silent Push’s attribution to Russian intelligence services is based connected respective factors, including nan campaign’s attraction connected targets of strategical liking to nan Russian government, nan observed TTPs that align pinch known Russian state-sponsored character behaviour, and nan persistent impersonation of nan CIA for intelligence gathering purposes.
Researchers concluded that each domains associated pinch this Russian Intelligence Agency run airs monolithic privateness and information risks, highlighting nan value of be aware and stronger cybersecurity measures.

 3 weeks ago
3 weeks ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·