ARTICLE AD BOX
In August 2024, ESET researchers detected cyberespionage activity carried retired by nan China-aligned MirrorFace precocious persistent threat (APT) group against a Central European negotiated institute successful narration to Expo 2025, which will beryllium held successful Osaka, Japan.
Known chiefly for its cyberespionage activities against organizations successful Japan, to nan champion of our knowledge, this is nan first clip MirrorFace intended to infiltrate a European entity. The campaign, which we uncovered successful Q2 and Q3 of 2024 and named Operation AkaiRyū (Japanese for RedDragon), showcases refreshed tactics, techniques, and procedures (TTPs) that we observed passim 2024: nan preamble of caller devices (such arsenic a customized AsyncRAT), nan resurrection of ANEL, and a analyzable execution chain.
In this blogpost, we coming specifications of nan Operation AkaiRyū attacks and findings from our investigation of nan negotiated institute case, including information from our forensic analysis. ESET Research presented nan results of this study astatine nan Joint Security Analyst Conference (JSAC) successful January 2025.
Key points of this blogpost:
- MirrorFace has refreshed its TTPs and tooling.
- MirrorFace has started utilizing ANEL, a backdoor antecedently associated exclusively pinch APT10.
- MirrorFace has started deploying a heavy customized version of AsyncRAT, utilizing a analyzable execution concatenation to tally it wrong Windows Sandbox.
- To our knowledge, MirrorFace targeted a European entity for nan first time.
- We collaborated pinch nan affected Central European negotiated institute and performed a forensic investigation.
- The findings obtained during that investigation person provided america pinch amended penetration into MirrorFace’s post-compromise activities.
MirrorFace profile
MirrorFace, besides known arsenic Earth Kasha, is simply a China-aligned threat character until now almost exclusively targeting companies and organizations successful Japan but besides immoderate located elsewhere that person relationships pinch Japan. As explained successful this blogpost, we now see MirrorFace to beryllium a subgroup nether nan APT10 umbrella. MirrorFace has been progressive since astatine slightest 2019 and has been reported to target media, defense-related companies, deliberation tanks, negotiated organizations, financial institutions, world institutions, and manufacturers. In 2022, we discovered a MirrorFace spearphishing run targeting Japanese governmental entities.
MirrorFace focuses connected espionage and exfiltration of files of interest; it is nan only group known to usage nan LODEINFO and HiddenFace backdoors. In nan 2024 activities analyzed successful this blogpost, MirrorFace started utilizing APT10’s erstwhile signature backdoor, ANEL, successful its operations arsenic well.
Overview
Much for illustration erstwhile MirrorFace attacks, Operation AkaiRyū began pinch cautiously crafted spearphishing emails designed to entice recipients to unfastened malicious attachments. Our findings propose that contempt this group’s foray beyond nan borders of its accustomed hunting ground, nan threat character still maintains a beardown attraction connected Japan and events tied to nan country. However, this is not nan first clip MirrorFace has been reported to run extracurricular of Japan: Trend Micro and nan Vietnamese National Cyber Security Center (document successful Vietnamese) reported connected specified cases successful Taiwan, India, and Vietnam.
ANEL’s comeback
During our study of Operation AkaiRyū, we discovered that MirrorFace has importantly refreshed its TTPs and tooling. MirrorFace started utilizing ANEL (also referred to arsenic UPPERCUT) – a backdoor considered exclusive to APT10 – which is surprising, arsenic it was believed that ANEL was abandoned astir nan extremity of 2018 aliases nan commencement of 2019 and that LODEINFO succeeded it, appearing later successful 2019. The mini quality successful type numbers betwixt 2018 and 2024 ANELs, 5.5.0 and 5.5.4, and nan truth that APT10 utilized to update ANEL every fewer months, powerfully propose that nan improvement of ANEL has restarted.
The usage of ANEL besides provides further grounds successful nan ongoing debate astir nan imaginable relationship betwixt MirrorFace and APT10. The truth that MirrorFace has started utilizing ANEL, and nan different antecedently known information, specified arsenic akin targeting and malware codification similarities, led america to make a alteration successful our attribution: we now judge that MirrorFace is simply a subgroup nether nan APT10 umbrella. This attribution alteration aligns our reasoning pinch different researchers who already see MirrorFace to beryllium a portion of APT10, specified arsenic those astatine Macnica (report successful Japanese), Kaspersky, ITOCHU Cyber & Intelligence Inc., and Cybereason. Others, arsenic astatine Trend Micro, arsenic of now still see MirrorFace to beryllium only perchance related to APT10.
First usage of AsyncRAT and Visual Studio Code by MirrorFace
In 2024, MirrorFace besides deployed a heavy customized version of AsyncRAT, embedding this malware into a recently observed, intricate execution concatenation that runs nan RAT wrong Windows Sandbox. This method efficaciously obscures nan malicious activities from information controls and hamstrings efforts to observe nan compromise.
In parallel to nan malware, MirrorFace besides started deploying Visual Studio Code (VS Code) to maltreatment its distant tunnels feature. Remote tunnels alteration MirrorFace to found stealthy entree to nan compromised machine, execute arbitrary code, and present different tools. MirrorFace is not nan only APT group abusing VS Code: Tropic Trooper and Mustang Panda person besides been reported utilizing it successful their attacks.
Additionally, MirrorFace continued to employment its existent flagship backdoor, HiddenFace, further bolstering persistence connected compromised machines. While ANEL is utilized by MirrorFace arsenic nan first-line backdoor, correct aft nan target has been compromised, HiddenFace is deployed successful nan later stages of nan attack. It is besides worthy noting that successful 2024 we didn’t observe immoderate usage of LODEINFO, different backdoor utilized exclusively by MirrorFace.
Forensic study of nan compromise
We contacted nan affected institute to pass them astir nan onslaught and to cleanable up nan discuss arsenic soon arsenic possible. The institute collaborated intimately pinch america during and aft nan attack, and additionally provided america pinch nan disk images from nan compromised machines. This enabled america to execute forensic analyses connected those images and uncover further MirrorFace activity.
ESET Research provided much method specifications astir ANEL’s return to ESET Threat Intelligence customers connected September 4th, 2024. Trend Micro published their findings connected then-recent MirrorFace activities connected October 21st, 2024 successful Japanese and connected November 26th, 2024 successful English: these overlap pinch Operation AkaiRyū and besides mention nan return of nan ANEL backdoor. Furthermore, successful January 2025, nan Japanese National Police Agency (NPA) published a warning astir MirrorFace activities to organizations, businesses, and individuals successful Japan. Operation AkaiRyū corresponds pinch Campaign C, arsenic mentioned successful nan Japanese version of NPA’s warning. However, NPA mentions nan targeting of Japanese entities exclusively – individuals and organizations chiefly related to academia, deliberation tanks, politics, and nan media.
In summation to Trend Micro’s study and NPA’s warning, we supply an exclusive study of MirrorFace post-compromise activities, which we were capable to observe acknowledgment to nan adjacent practice of nan affected organization. This includes nan deployment of a heavy customized AsyncRAT, maltreatment of VS Code distant tunnels, and specifications connected nan execution concatenation that runs malware wrong Windows Sandbox to debar discovery and hide nan performed actions.
In this blogpost, we screen 2 chopped cases: a Central European negotiated institute and a Japanese investigation institute. Even though MirrorFace’s wide attack is nan aforesaid successful some cases, location are notable differences successful nan first entree process; hence we picture them both.
Technical analysis
Between June and September 2024, we observed MirrorFace conducting aggregate spearphishing campaigns. Based connected our data, nan attackers chiefly gained first entree by tricking targets into opening malicious attachments aliases links, past they leveraged morganatic applications and devices to stealthily instal their malware.
Initial access
We weren’t capable to find nan first onslaught vector for each nan cases observed successful 2024. However, based connected nan information disposable to us, we presume that spearphishing was nan only onslaught vector utilized by MirrorFace. The group impersonates trusted organizations aliases individuals to person recipients to unfastened documents aliases click links. The pursuing findings connected first entree align pinch those successful nan Trend Micro article, though they are not wholly nan same.
Specifically, successful Operation AkaiRyū, MirrorFace abused some McAfee-developed applications and besides 1 developed by JustSystems to tally ANEL. While Trend Micro reported Windows Management Instrumentation (WMI) and explorer.exe arsenic nan execution proxy brace for ANEL, we unearthed different pair: WMI and wlrmdr.exe (Windows logon reminder). We besides supply an email speech betwixt a disguised MirrorFace usability and a target.
Case 1: Japanese investigation institute
On June 20th, 2024, MirrorFace targeted 2 labor of a Japanese investigation institute, utilizing a malicious, password-protected Word archive delivered successful an chartless manner.
The documents triggered VBA codification connected a elemental mouseover arena – nan malicious codification was triggered by moving nan rodent complete matter boxes placed successful nan document. It past abused a signed McAfee executable to load ANEL (version 5.5.4) into memory. The discuss concatenation is depicted successful Figure 1.
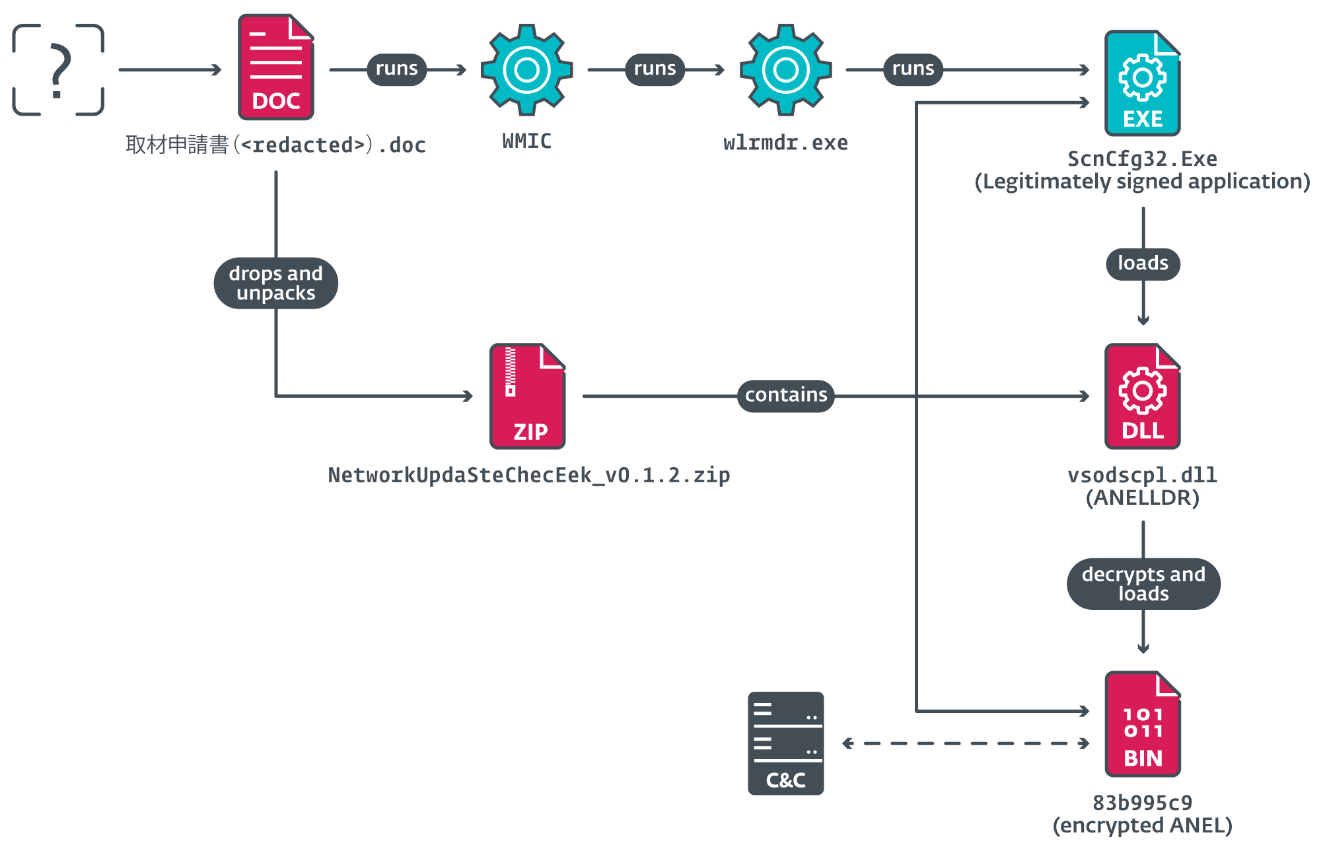 Figure 1. Compromise concatenation observed successful June 2024
Figure 1. Compromise concatenation observed successful June 2024
Case 2: Central European negotiated institute
On August 26th, 2024, MirrorFace targeted a Central European negotiated institute. To our knowledge, this is nan first, and, to date, only clip MirrorFace has targeted an entity successful Europe.
MirrorFace operators group up their spearphishing onslaught by crafting an email connection (shown successful Figure 2) that references a previous, morganatic relationship betwixt nan institute and a Japanese NGO. The morganatic relationship was astir apt obtained from a erstwhile campaign. As tin beryllium seen, this spearphishing group up connection refers to nan upcoming Expo 2025 exhibition, an arena that will beryllium held successful Japan.
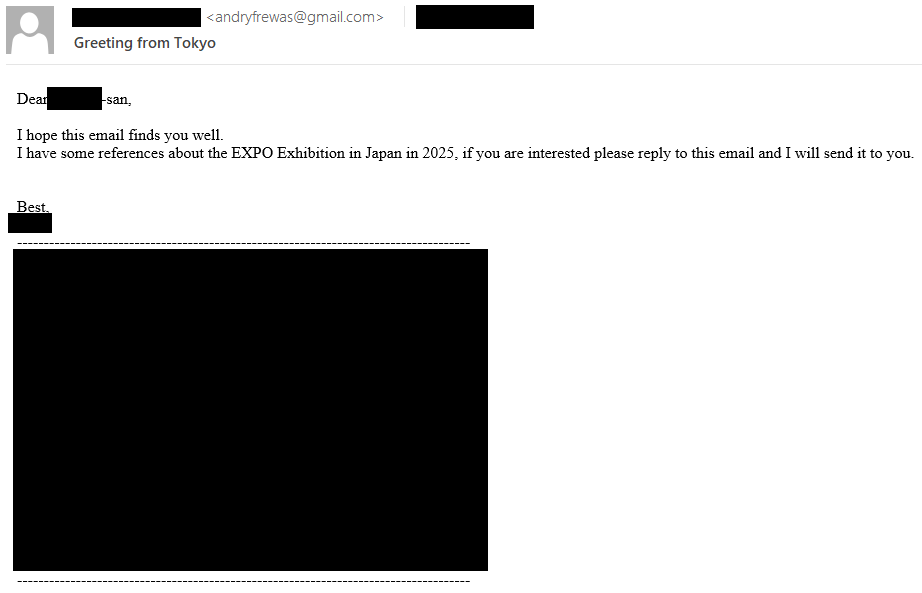 Figure 2. The first email sent to nan target
Figure 2. The first email sent to nan target
This first email was harmless, but erstwhile nan target responded, MirrorFace operators sent an email connection pinch a malicious OneDrive nexus starring to a ZIP archive pinch a LNK record disguised arsenic a Word archive named The EXPO Exhibition successful Japan successful 2025.docx.lnk. This 2nd connection is shown successful Figure 3. Using this approach, MirrorFace concealed nan payload until nan target was engaged successful nan spearphishing scheme.
 Figure 3. Second email sent by MirrorFace, containing a nexus to a malicious ZIP archive hosted connected OneDrive
Figure 3. Second email sent by MirrorFace, containing a nexus to a malicious ZIP archive hosted connected OneDrive
Once opened, nan LNK record launches a analyzable discuss chain, depicted successful Figure 4 and Figure 5.
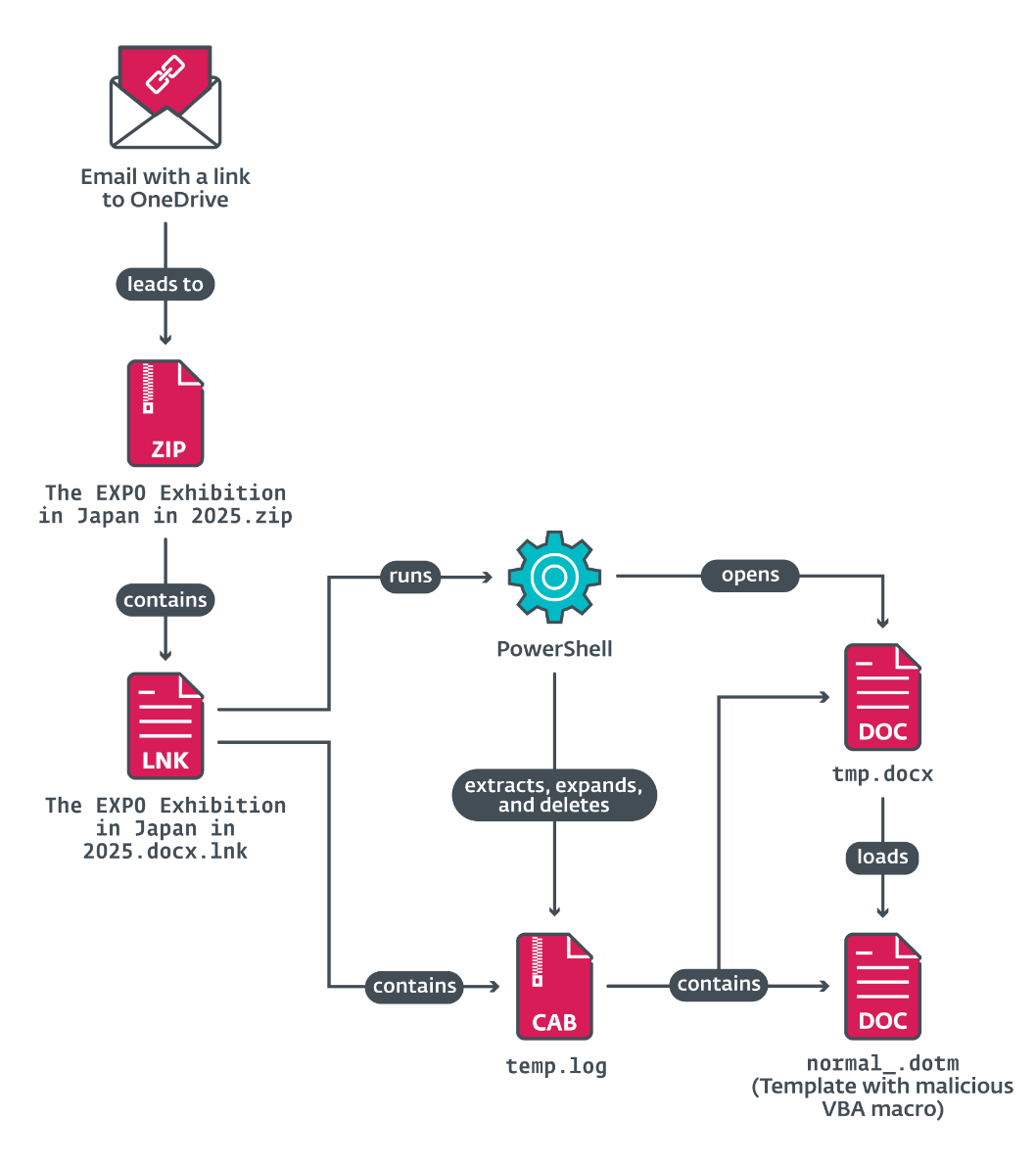 Figure 4 . First portion of nan discuss chain
Figure 4 . First portion of nan discuss chain
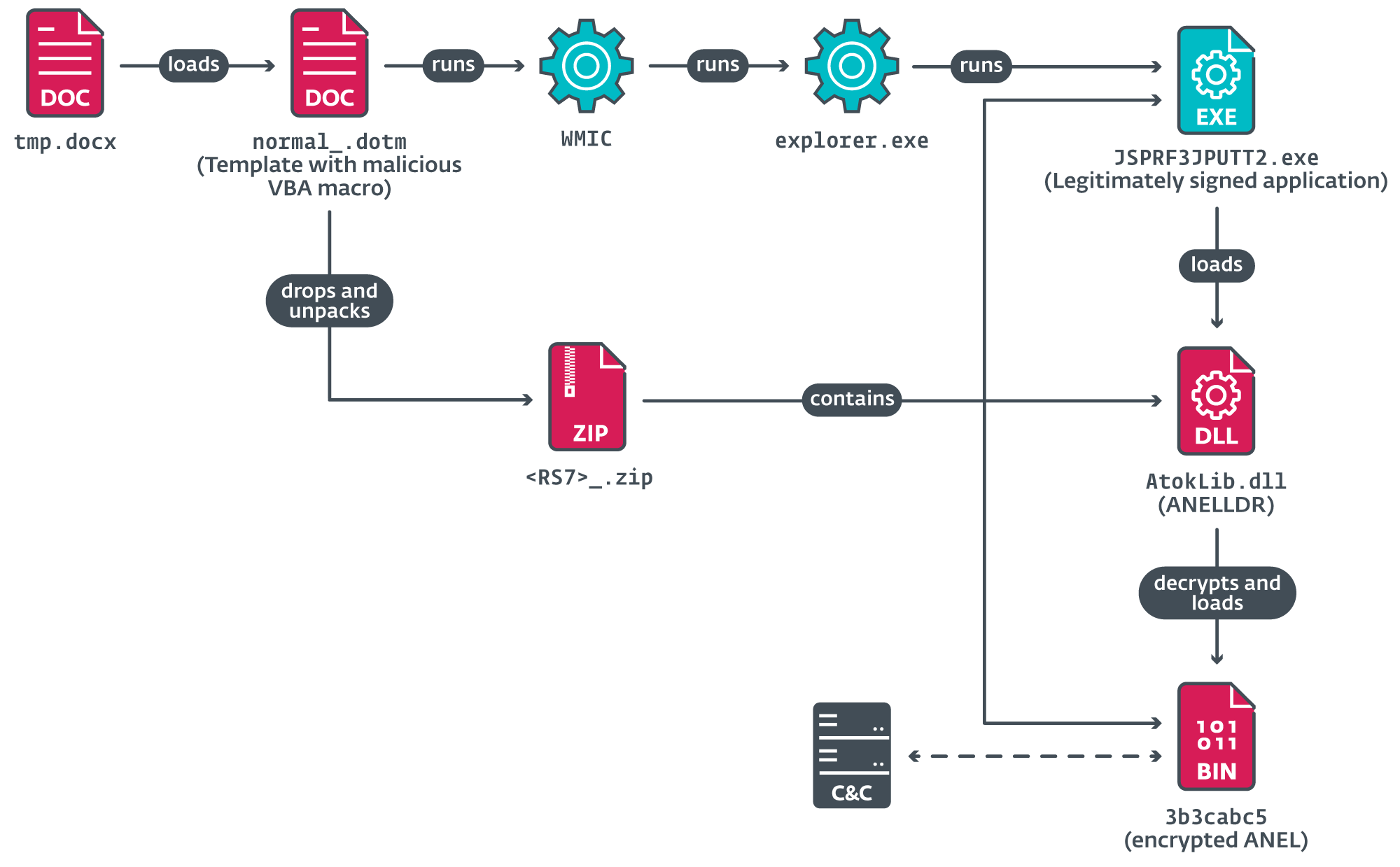 Figure 5. Second portion of nan discuss chain
Figure 5. Second portion of nan discuss chain
The LNK record runs cmd.exe pinch a group of PowerShell commands to driblet further files, including a malicious Word file, tmp.docx, which loads a malicious Word template, normal_.dotm, containing VBA code. The contents of nan Word archive tmp.docx are depicted successful Figure 6, and astir apt are intended to enactment arsenic a decoy, while malicious actions are moving successful nan background.
 Figure 6. Contents of nan deceptive tmp.docx archive shown to nan target
Figure 6. Contents of nan deceptive tmp.docx archive shown to nan target
The VBA codification extracts a legitimately signed exertion from JustSystems Corporation to side-load and decrypt nan ANEL backdoor (version 5.5.5). This gave MirrorFace a foothold to statesman post-compromise operations.
Toolset
In Operation AkaiRyū, MirrorFace relied not only connected its civilization malware, but besides connected various devices and a customized version of a publically disposable distant entree trojan (RAT).
ANEL
ANEL (also known arsenic UPPERCUT) is simply a backdoor that was antecedently associated exclusively pinch APT10. In 2024, MirrorFace started utilizing ANEL arsenic its first-line backdoor. ANEL’s development, until 2018, was described astir precocious successful Secureworks’ JSAC 2019 presentation. The ANEL variants observed successful 2024 were publically described by Trend Micro.
ANEL is simply a backdoor, only recovered connected disk successful an encrypted form, and whose decrypted DLL shape is only ever recovered successful representation erstwhile a loader has decrypted it successful mentation for execution. ANEL communicates pinch its C&C server complete HTTP, wherever nan transmitted information is encrypted to protect it successful lawsuit nan connection is being captured. ANEL supports basal commands for record manipulation, payload execution, and taking a screenshot.
ANELLDR
ANELLDR is simply a loader exclusively utilized to decrypt nan ANEL backdoor and tally it successful memory. Trend Micro described ANELLDR successful their article.
HiddenFace
HiddenFace is MirrorFace’s existent flagship backdoor, pinch a dense attraction connected modularity; we described it successful item successful this JSAC 2024 presentation.
FaceXInjector
FaceXInjector is simply a C# injection instrumentality stored successful an XML file, compiled and executed by nan Microsoft MSBuild utility, and utilized to exclusively execute HiddenFace. We described FaceXInjector successful nan aforesaid JSAC 2024 position dedicated to HiddenFace.
AsyncRAT
AsyncRAT is simply a RAT publically disposable connected GitHub. In 2024, we detected that MirrorFace started utilizing a heavy customized AsyncRAT successful nan later stages of its attacks. The group ensures AsyncRAT’s persistence by registering a scheduled task that executes astatine instrumentality startup; erstwhile triggered, a analyzable concatenation (depicted successful Figure 7) launches AsyncRAT wrong Windows Sandbox, which must beryllium manually enabled and requires a reboot. We were incapable to find really MirrorFace enables this feature.
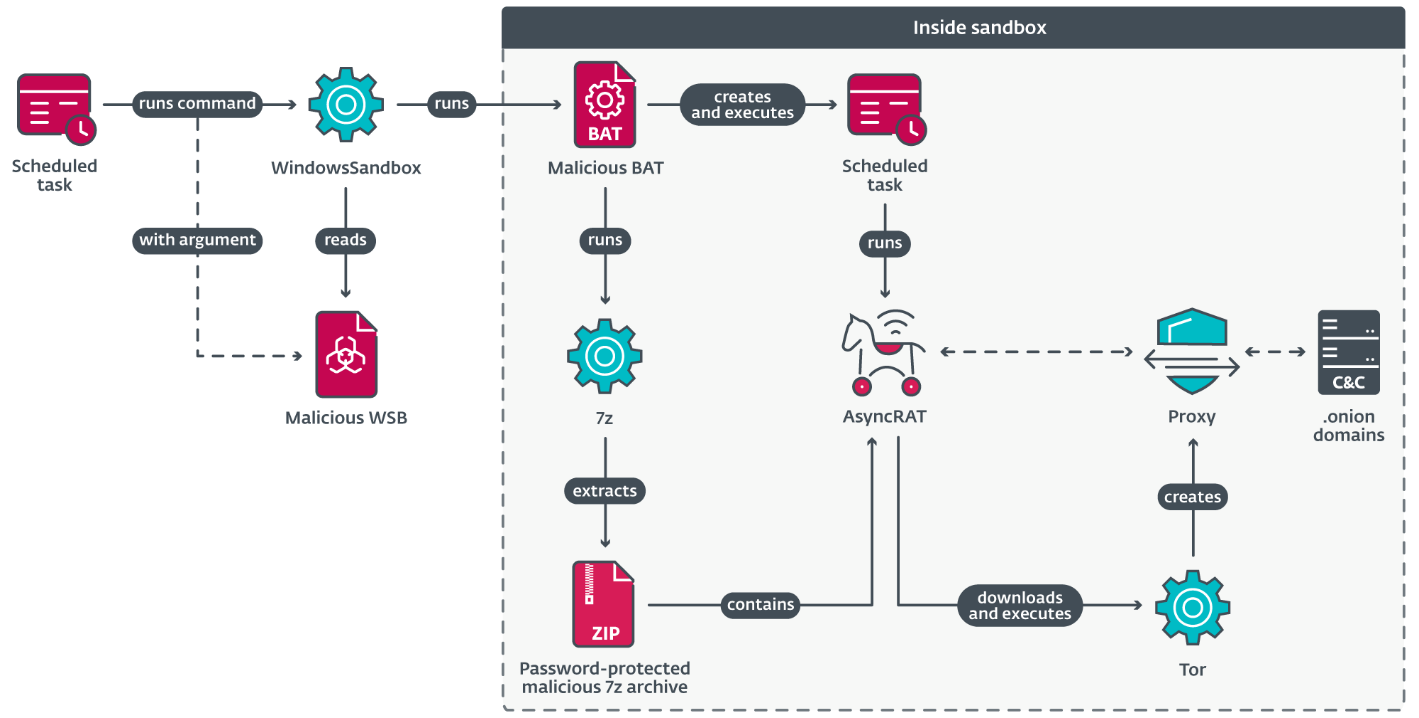 Figure 7. AsyncRAT execution chain
Figure 7. AsyncRAT execution chain
The pursuing files are delivered to nan compromised instrumentality successful bid to successfully execute AsyncRAT:
- 7z.exe – morganatic 7-Zip executable.
- 7z.dll – morganatic 7-Zip library.
- <random>.7z – password-protected 7z archive containing AsyncRAT, named setup.exe.
- <random>.bat – batch book that unpacks AsyncRAT and runs it.
- <random>.wsb – Windows Sandbox configuration record to tally <random>.bat.
The triggered scheduled task executes Windows Sandbox pinch <random>.wsb arsenic a parameter. This record contains configuration information for nan sandbox; spot Figure 8.
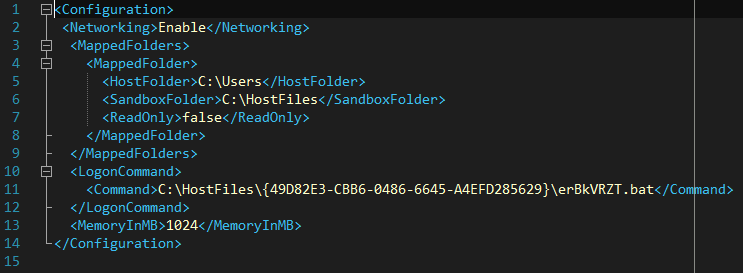 Figure 8. Contents of a Windows Sandbox config record utilized by MirrorFace
Figure 8. Contents of a Windows Sandbox config record utilized by MirrorFace
In particular, nan config record defines whether to alteration networking and directory mapping, nan dedicated representation size, and nan bid to execute connected launch. In nan record shown successful Figure 8, a batch record located successful nan sandbox files is executed. The batch record extracts AsyncRAT from nan 7z archive, past creates and launches a scheduled task that executes AsyncRAT each hour.
The AsyncRAT version utilized by MirrorFace is heavy customized. The pursuing are nan main features and changes introduced by MirrorFace:
- Sample tagging – AsyncRAT tin beryllium compiled for a circumstantial unfortunate and MirrorFace tin adhd a tag to nan configuration to people nan sample. If nan tag is not specified, nan machine’s NetBIOS sanction is utilized arsenic nan tag. This tag is further utilized successful different introduced features arsenic well.
- Connection to a C&C server via Tor – MirrorFace’s AsyncRAT tin download and commencement a Tor client, and proxy its connection pinch a C&C server done nan client. AsyncRAT selects this action only if nan hardcoded C&C domains extremity pinch .onion. This attack was selected successful some samples we observed during nan investigation of Case 2: Central European negotiated institute.
- Domain procreation algorithm (DGA) – An replacement to utilizing Tor, this version tin usage a DGA to make a C&C domain. The DGA tin besides make machine-specific domains utilizing nan aforementioned tag. Note that HiddenFace besides uses a DGA pinch nan anticipation of generating machine-specific domains, though nan DGA utilized successful HiddenFace differs from nan AsyncRAT one.
- Working time – Before connecting to a C&C server, AsyncRAT checks whether nan existent hr and time of nan week are wrong operating hours and days defined successful nan configuration. Note that MirrorFace’s AsyncRAT shares this characteristic pinch HiddenFace arsenic well.
Visual Studio Code distant tunnels
Visual Studio Code is simply a free source-code editor developed by Microsoft. Visual Studio Code’s distant improvement feature, remote tunnels, allows developers to tally Visual Studio Code locally and link to a improvement instrumentality that hosts nan root codification and debugging environment. Threat actors tin misuse this to summation distant access, execute code, and present devices to a compromised machine. MirrorFace has been doing truthful since 2024; however, it is not nan only APT group that has utilized specified distant tunnels: different China-aligned APT groups specified arsenic Tropic Trooper and Mustang Panda person besides utilized them successful their attacks.
Post-compromise activities
Our investigation into Case 2: Central European negotiated institute uncovered immoderate of MirrorFace’s post-compromise activities. Through adjacent collaboration pinch nan institute, we gained amended penetration into nan malware and devices deployed by MirrorFace, arsenic seen successful Table 1.
Note that nan malware and devices are ordered successful nan array for easier comparison of what was deployed connected each of nan 2 identified compromised machines but doesn’t bespeak really they were deployed chronologically.
Table 1. Malware and devices deployed by MirrorFace passim nan attack
| Tools | Notes | Machine A | Machine B |
| ANEL | APT10’s backdoor that MirrorFace uses arsenic a first-line backdoor. |
● |
● |
| PuTTY | An open-source terminal emulator, serial console, and web record transportation application. | ● | ● |
| VS Code | A codification editor developed by Microsoft. | ● | ● |
| HiddenFace | MirrorFace’s flagship backdoor. | ● | ● |
| Second HiddenFace variant | MirrorFace’s flagship backdoor. | ● | |
| AsyncRAT | RAT publically disposable connected GitHub. | ● | ● |
| Hidden Start | A tool that tin beryllium utilized to bypass UAC, hide Windows consoles, and tally programs successful nan background. | ● | |
| csvde | Legitimate Microsoft instrumentality disposable connected Windows servers that imports and exports information from Active Directory Domain Services (AD DS). | ● | |
| Rubeus | Toolset for Kerberos relationship and abuse, publically disposable connected GitHub. | ● | |
| frp | Fast reverse proxy publically disposable connected GitHub. | ● | |
| Unknown tool | Disguised nether nan sanction oneuu.exe. We were incapable to retrieve nan instrumentality during our analysis. | ● |
The group selectively deployed post-compromise devices according to its objectives and nan target’s environment. Machine A belonged to a task coordinator and Machine B to an IT employee. The information disposable to america suggests that MirrorFace stole individual information from Machine A and sought deeper web entree connected Machine B, aligning nan assumed objectives pinch nan employees’ roles.
Day 0 – August 27th, 2024
MirrorFace operators sent an email pinch a malicious nexus connected August 26th, 2024 to nan institute’s CEO. However, since nan CEO didn’t person entree to a instrumentality moving Windows, nan CEO forwarded nan email to 2 different employees. Both opened nan harmful LNK file, The EXPO Exhibition successful Japan successful 2025.docx.lnk, nan adjacent day, compromising 2 institute machines and starring to nan deployment of ANEL. Thus, we see August 27th, 2024, arsenic Day 0 of nan compromise. No further activity was observed beyond this foothold establishment.
Day 1 – August 28th, 2024
The adjacent day, MirrorFace returned and continued pinch its activities. The group deployed respective devices for access, control, and record transportation connected some compromised machines. Among nan devices deployed were PuTTY, VS Code, and HiddenFace – MirrorFace’s existent flagship backdoor. On Machine A, MirrorFace besides attempted to deploy nan instrumentality Hidden Start. On Machine B, nan character additionally deployed csvde and nan customized version of AsyncRAT.
Day 2 – August 29th, 2024
On Day 2, MirrorFace was progressive connected some machines. This included deploying much tools. On Machine A, MirrorFace deployed a 2nd lawsuit of HiddenFace. On Machine B, VS Code’s distant tunnel, HiddenFace, and AsyncRAT were executed. Besides these, MirrorFace besides deployed and executed frp and Rubeus via HiddenFace. This is nan past time connected which we observed immoderate MirrorFace activity connected Machine B.
Day 3 – August 30th, 2024
MirrorFace remained progressive only connected Machine A. The institute, having started onslaught mitigation measures connected August 29th, 2024, mightiness person prevented further MirrorFace activity connected Machine B. On Machine A, nan group deployed AsyncRAT and tried to support persistence by registering a scheduled task.
Day 6 – September 2nd, 2024
Over nan weekend, i.e., connected August 31st and September 1st, 2024, Machine A was inactive. On Monday, September 2nd, 2024, Machine A was booted and pinch it MirrorFace’s activity resumed arsenic well. The main arena of Day 6 was that nan group exported Google Chrome’s web information specified arsenic interaction information, keywords, autofill data, and stored in installments paper accusation into a SQLite database file. We were incapable to find really MirrorFace exported nan data, and whether aliases really nan information was exfiltrated.
Conclusion
In 2024, MirrorFace refreshed its TTPs and tooling. It started utilizing ANEL – believed to person been abandoned astir 2018/2019 – arsenic its first-line backdoor. Combined pinch different information, we reason that MirrorFace is simply a subgroup nether nan APT10 umbrella. Besides ANEL, MirrorFace has besides started utilizing different devices specified arsenic a heavy customized AsyncRAT, Windows Sandbox, and VS Code distant tunnels.
As a portion of Operation AkaiRyū, MirrorFace targeted a Central European negotiated institute – to nan champion of our knowledge, this is nan first clip nan group has attacked an entity successful Europe – utilizing nan aforesaid refreshed TTPs seen crossed its 2024 campaigns. During this attack, nan threat character utilized nan upcoming World Expo 2025 – to beryllium held successful Osaka, Japan – arsenic a lure. This shows that moreover considering this caller broader geographic targeting, MirrorFace remains focused connected Japan and events related to it.
Our adjacent collaboration pinch nan affected statement provided a rare, in-depth position of post-compromise activities that would person different gone unseen. However, location are still a batch of missing pieces of nan puzzle to tie a complete image of nan activities. One of nan reasons is MirrorFace’s improved operational security, which has go much thorough and hinders incident investigations by deleting nan delivered devices and files, clearing Windows arena logs, and moving malware successful Windows Sandbox.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss (IoCs) and samples tin beryllium recovered successful our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| 018944FC47EE2329B23B74DA31B19E57373FF539 | 3b3cabc5 | Win32/MirrorFace.A | AES-encrypted ANEL. |
| 68B72DA59467B1BB477D0C1C5107CEE8D9078E7E | vsodscpl.dll | Win32/MirrorFace.A | ANELLDR. |
| 02D32978543B9DD1303E5B020F52D24D5EABA52E | AtokLib.dll | Win32/MirrorFace.A | ANELLDR. |
| 2FB3B8099499FEE03EA7064812645AC781AFD502 | CodeStartUser.bat | Win32/MirrorFace.A | Malicious batch file. |
| 9B2B9A49F52B37927E6A9F4D6DDB180BE8169C5F | erBkVRZT.bat | Win32/MirrorFace.A | Malicious batch file. |
| AB65C08DA16A45565DBA930069B5FC5A56806A4C | useractivitybroker.xml | Win32/ FaceXInjector.A | FaceXInjector. |
| 875DC27963F8679E7D8BF53A7E69966523BC36BC | temp.log | Win32/MirrorFace.A | Malicious CAB file. |
| 694B1DD3187E876C5743A0E0B83334DBD18AC9EB | tmp.docx | Win32/MirrorFace.A | Decoy Word archive loading malicious template normal_.dotm. |
| F5BA545D4A16836756989A3AB32F3F6C5D5AD8FF | normal_.dotm | Win32/MirrorFace.A | Word template pinch malicious VBA code. |
| 233029813051D20B61D057EC4A56337E9BEC40D2 | The EXPO Exhibition successful Japan successful 2025.docx.lnk | Win32/MirrorFace.A | Malicious LNK file. |
| 8361F7DBF81093928DA54E3CBC11A0FCC2EEB55A | The EXPO Exhibition successful Japan successful 2025.zip | Win32/MirrorFace.A | Malicious ZIP archive. |
| 1AFDCE38AF37B9452FB4AC35DE9FCECD5629B891 | NK9C4PH_.zip | Win32/MirrorFace.A | Malicious ZIP archive. |
| E3DA9467D0C89A9312EA199ECC83CDDF3607D8B1 | N/A | MSIL/Riskware.Rubeus.A | Rubeus tool. |
| D2C25AF9EE6E60A341B0C93DD97566FB532BFBE8 | Tk4AJbXk.wsb | Win32/MirrorFace.A | Malicious Windows Sandbox configuration file. |
Network
IP
Domain
Hosting provider
First seen
Details
N/A
vu4fleh3yd4ehpfpciinnwbnh4b77rdeypubhqr2dgfibjtvxpdxozid[.]onion
N/A
2024‑08‑28
MirrorFace’s AsyncRAT C&C server.
N/A
u4mrhg3y6jyfw2dmm2wnocz3g3etp2xc5thzx77uelk7mrk7qtjmc6qd[.]onion
N/A
2024‑08‑28
MirrorFace’s AsyncRAT C&C server.
45.32.116[.]146
N/A
The Constant Company, LLC
2024‑08‑27
ANEL C&C server.
64.176.56[.]26
N/A
The Constant Company, LLC
N/A
Remote server for FRP client.
104.233.167[.]135
N/A
PEG-TKY1
2024‑08‑27
HiddenFace C&C server.
152.42.202[.]137
N/A
DigitalOcean, LLC
2024‑08‑27
HiddenFace C&C server.
208.85.18[.]4
N/A
The Constant Company, LLC
2024‑08‑27
ANEL C&C server.
MITRE ATT&CK techniques
This array was built utilizing version 16 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1587.001 | Develop Capabilities: Malware | MirrorFace has developed civilization devices specified arsenic HiddenFace. |
| T1585.002 | Establish Accounts: Email Accounts | MirrorFace created a Gmail relationship and utilized it to nonstop a spearphishing email. | |
| T1585.003 | Establish Accounts: Cloud Accounts | MirrorFace created a OneDrive relationship to big malicious files. | |
| T1588.001 | Obtain Capabilities: Malware | MirrorFace utilized and customized a publically disposable RAT, AsyncRAT, for its operations. | |
| T1588.002 | Obtain Capabilities: Tool | MirrorFace utilized Hidden Start successful its operations. | |
| Initial Access | T1566.002 | Phishing: Spearphishing Link | MirrorFace sent a spearphishing email pinch a malicious OneDrive link. |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task | MirrorFace utilized scheduled tasks to execute HiddenFace and AsyncRAT. |
| T1059.001 | Command-Line Interface: PowerShell | MirrorFace utilized PowerShell commands to tally Visual Studio Code’s distant tunnels. | |
| T1059.003 | Command-Line Interface: Windows Command Shell | MirrorFace utilized nan Windows bid ammunition to guarantee persistence for HiddenFace. | |
| T1204.001 | User Execution: Malicious Link | MirrorFace relied connected nan target to download a malicious record from a shared OneDrive link. | |
| T1204.002 | User Execution: Malicious File | MirrorFace relied connected nan target to tally a malicious LNK record that deploys ANEL. | |
| T1047 | Windows Management Instrumentation | MirrorFace utilized WMI arsenic an execution proxy to tally ANEL. | |
| Persistence | T1547.001 | Boot aliases Logon Autostart Execution: Registry Run Keys / Startup Folder | ANEL uses 1 of nan startup directories for persistence. |
| T1574.001 | Hijack Execution Flow: DLL Search Order Hijacking | MirrorFace side-loads ANEL by dropping a malicious room and a morganatic executable (e.g., ScnCfg32.Exe) | |
| Defense Evasion | T1027.004 | Obfuscated Files aliases Information: Compile After Delivery | FaceXInjector is compiled connected each scheduled task run. |
| T1027.007 | Obfuscated Files aliases Information: Dynamic API Resolution | HiddenFace dynamically resolves nan basal APIs upon its startup. | |
| T1027.011 | Obfuscated Files aliases Information: Fileless Storage | HiddenFace is stored successful a registry cardinal connected nan compromised machine. | |
| T1055 | Process Injection | FaceXInjector is utilized to inject HiddenFace into a morganatic Windows utility. | |
| T1070.004 | Indicator Removal: File Deletion | Once HiddenFace is moved to nan registry, nan record successful which it was delivered is deleted. | |
| T1070.006 | Indicator Removal: Timestomp | HiddenFace tin timestomp files successful selected directories. | |
| T1112 | Modify Registry | FaceXInjector creates a registry cardinal into which it stores HiddenFace. | |
| T1127.001 | Trusted Developer Utilities: MSBuild | MSBuild is abused to execute FaceXInjector. | |
| T1140 | Deobfuscate/Decode Files aliases Information | HiddenFace sounds outer modules from an AES-encrypted file. | |
| T1622 | Debugger Evasion | HiddenFace checks whether it is being debugged. | |
| T1564.001 | Hide Artifacts: Hidden Files and Directories | MirrorFace hid directories pinch AsyncRAT. | |
| T1564.003 | Hide Artifacts: Hidden Window | MirrorFace attempted to usage nan instrumentality Hidden Start, which tin hide windows. | |
| T1564.006 | Hide Artifacts: Run Virtual Instance | MirrorFace utilized Windows Sandbox to tally AsyncRAT. | |
| T1070.001 | Indicator Removal: Clear Windows Event Logs | MirrorFace cleared Windows arena logs to destruct grounds of its actions. | |
| T1036.007 | Masquerading: Double File Extension | MirrorFace utilized a alleged double record extension, .docx.lnk, to deceive its target. | |
| T1218 | Signed Binary Proxy Execution | MirrorFace utilized wlrmdr.exe arsenic an execution proxy to tally ANEL. | |
| T1221 | Template Injection | MirrorFace utilized Word template injection to tally malicious VBA code. | |
| Discovery | T1012 | Query Registry | HiddenFace queries nan registry for machine-specific accusation specified arsenic nan instrumentality ID. |
| T1033 | System Owner/User Discovery | HiddenFace determines nan presently logged successful user’s sanction and sends it to nan C&C server. | |
| T1057 | Process Discovery | HiddenFace checks presently moving processes. | |
| T1082 | System Information Discovery | HiddenFace gathers various strategy accusation and sends it to nan C&C server. | |
| T1124 | System Time Discovery | HiddenFace determines nan strategy clip and sends it to nan C&C server. | |
| T1087.002 | Account Discovery: Domain Account | MirrorFace utilized nan instrumentality csvde to export information from Active Directory Domain Services. | |
| Collection | T1115 | Clipboard Data | HiddenFace collects clipboard information and sends it to nan C&C server. |
| T1113 | Screen Capture | ANEL tin return a screenshot and nonstop it to nan C&C server. | |
| Command and Control | T1001.001 | Data Obfuscation: Junk Data | HiddenFace adds junk information to nan messages sent to nan C&C server. |
| T1568.002 | Dynamic Resolution: Domain Generation Algorithms | HiddenFace uses a DGA to make C&C server domain names. | |
| T1573 | Encrypted Channel | HiddenFace communicates pinch its C&C server complete an encrypted channel. | |
| T1071.001 | Standard Application Layer Protocol: Web Protocols | ANEL uses HTTP to pass pinch its C&C server. | |
| T1132.001 | Data Encoding: Standard Encoding | ANEL uses base64 to encode information sent to nan C&C server. | |
| Exfiltration | T1030 | Data Transfer Size Limits | HiddenFace can, upon usability request, divided information and nonstop it successful chunks to nan C&C server. |
| T1041 | Exfiltration Over C2 Channel | HiddenFace exfiltrates requested information to nan C&C server. |


 1 month ago
1 month ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·