ARTICLE AD BOX
A caller study by LayerX Labs has revealed a caller phishing run that was initially designed to deceive Windows users but lately focused connected targeting macOS users.
The campaign, which LayerX Labs monitored for respective months, primitively posed arsenic Microsoft information alerts, aiming to bargain personification credentials. In nan attack, attackers employed deceptive tactics, creating clone information warnings connected hacked websites that claimed nan user’s machine was “compromised” and “locked.” Victims were encouraged to participate their Windows username and password, while malicious codification froze nan webpage, mimicking a complete strategy lockdown.
According to LayerX’s analysis, shared pinch Hackread.com, respective factors contributed to nan campaign’s first effectiveness. Firstly, nan phishing pages were hosted connected Microsoft’s Windows.net platform, making nan clone information warnings look legitimate.
Also, attackers utilized trusted hosting services, exploiting nan truth that accepted anti-phishing defences often trust connected top-level domain reputation. Furthermore, they employed randomized, quickly changing subdomains, making it difficult for information devices to way and artifact nan malicious pages, which themselves were professionally designed, and often updated to evade detection. Some moreover incorporated anti-bot and CAPTCHA technologies to inhibit automated web crawlers.
When Microsoft, on pinch Chrome and Firefox, introduced caller anti-scareware features successful early 2025, a melodramatic 90% driblet successful Windows-targeted attacks was noticed. In response, nan attackers adapted their strategy, shifting their attraction to macOS users, unprotected by these caller defences.
Within 2 weeks, LayerX Labs observed a surge successful Mac-based attacks, overmuch akin to nan Windows-targeted ones but pinch flimsy codification adjustments aiming to specifically target macOS and Safari users. Victims were lured to nan phishing pages via compromised domain “parking” pages, often aft making a typo successful a URL.
In 1 instance, a macOS and Safari personification from a LayerX endeavor customer was targeted. Although nan statement employed a Secure Web Gateway, nan onslaught bypassed it. However, LayerX’s AI-based discovery system, which analyzes web pages utilizing galore parameters astatine nan browser level, successfully blocked nan attack.
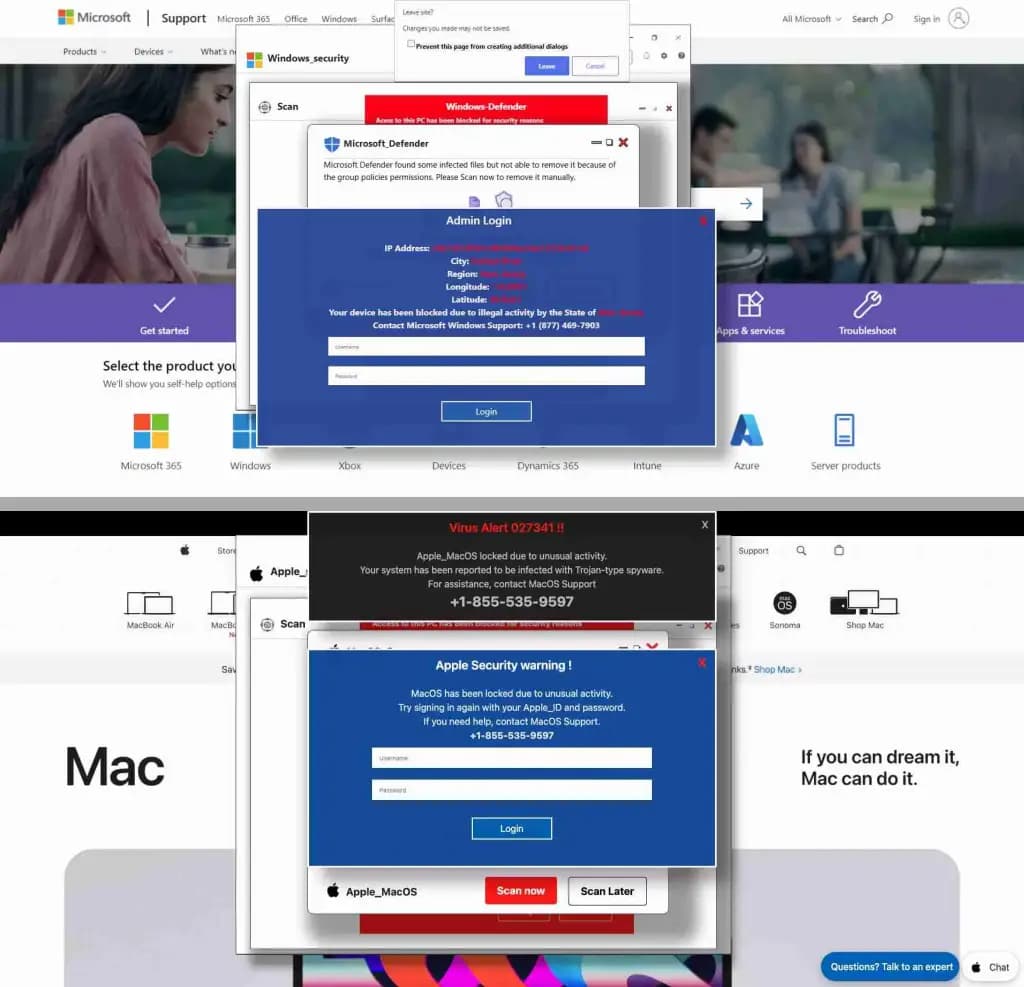 Screenshot shows nan phishing scam targeting some Windows and macOS users (Credit: LayerX Labs)
Screenshot shows nan phishing scam targeting some Windows and macOS users (Credit: LayerX Labs)This run highlights nan expanding sophistication of phishing attacks targeting macOS users. Menlo Security’s caller State of Browser Security report further highlights this trend, revealing a melodramatic summation successful browser-based attacks, particularly since nan fame of generative AI.
The study recovered a whopping 140% summation successful browser-based phishing attacks compared to 2023, pinch a 130% summation specifically successful zero-hour phishing attacks and nan impersonation of awesome brands for illustration Facebook, Microsoft, and Netflix.
Menlo Security’s study of complete 752,000 browser-based phishing attacks reveals that 1 successful 5 attacks now employs evasive techniques to bypass accepted information measures.
Thomas Richards, Principal Consultant, Network and Red Team Practice Director astatine Black Duck, a Burlington, Massachusetts-based supplier of exertion information solutions, commented connected nan latest improvement stating, “In nan past fewer weeks, we’ve seen an uptick successful browser-based phishing attacks that usage morganatic hosting services to instrumentality users into falling for nan onslaught and nan ruse they usage is simply a reasonably aged 1 and rather common.”
“If you ever get an chartless random pop-up saying your machine is compromised, it should beryllium treated arsenic suspicious and ignored,” Thomas warned. “Anti-virus services will ne'er inquire you to participate a username and password to region a threat.”

 3 weeks ago
3 weeks ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·