ARTICLE AD BOX
Spotify boasts almost 700 cardinal progressive users, including 265 cardinal premium subscribers. As nan world’s starring euphony streaming service, it’s hardly astonishing that it besides attracts each mode of bad actors who are eager to utilization its users.
Spotify accounts correspond valuable integer assets that tin beryllium monetized done aggregate channels, including on nan acheronian web and nan shadowy corners of Telegram. While discounted compared to morganatic subscription costs, nan going prices of hacked Spotify accounts often make important profits erstwhile sold successful bulk. A azygous successful phishing run targeting Spotify users tin output ample numbers of accounts, which translates into sizeable forbidden revenue.
Compromised accounts supply valuable individual information that tin beryllium utilized for personality theft aliases societal engineering attacks. Access to a Spotify relationship whitethorn uncover individual information, costs details, listening habits, and connections to societal media and different online services, which creates opportunities for further targeted attacks.
Additionally, hacked accounts service arsenic vehicles for artificially inflating watercourse counts. This practice, known arsenic “streaming fraud”, involves utilizing networks of compromised accounts to many times play circumstantial tracks, generating fraudulent royalty payments. According to Beatdapp, a streaming fraud discovery platform, astatine slightest 10% of each opus streams are fraudulent, taking up to US$3 cardinal retired of nan world euphony manufacture each year.
Now, knowing really Spotify accounts tin beryllium hacked is nan first measurement towards staying safe. Let’s reappraisal nan main strategies utilized by cybercriminals to get personification credentials, nan reddish flags to watch retired for, and really to show that your relationship whitethorn person been compromised.
Phishing
Phishing emails are a staple tactic, though galore of these schemes person evolved importantly beyond evident scam emails replete pinch pronunciation errors and different giveaways. Many of today’s phishing campaigns trust connected precocious societal engineering techniques and convincing ocular elements that tin fool moreover plentifulness of cautious users.
Generally speaking, however, phishing ploys often statesman pinch an email astir supposedly superior issues pinch your account, specified arsenic “Payment Method Declined: Subscription Will Be Canceled.” These messages create a consciousness of urgency and often unreality judgement and summation nan likelihood of hasty actions, particularly if they’re complete pinch charismatic Spotify logos and formatting astir identical to morganatic Spotify communications.
For example, a phishing email mightiness declare that your relationship will beryllium deactivated owed to a costs issue. It will past punctual you to click connected a nexus to “resolve” nan problem. Instead, you’ll extremity up connected an imposter tract that is designed to steal your login credentials and perchance other delicate information.
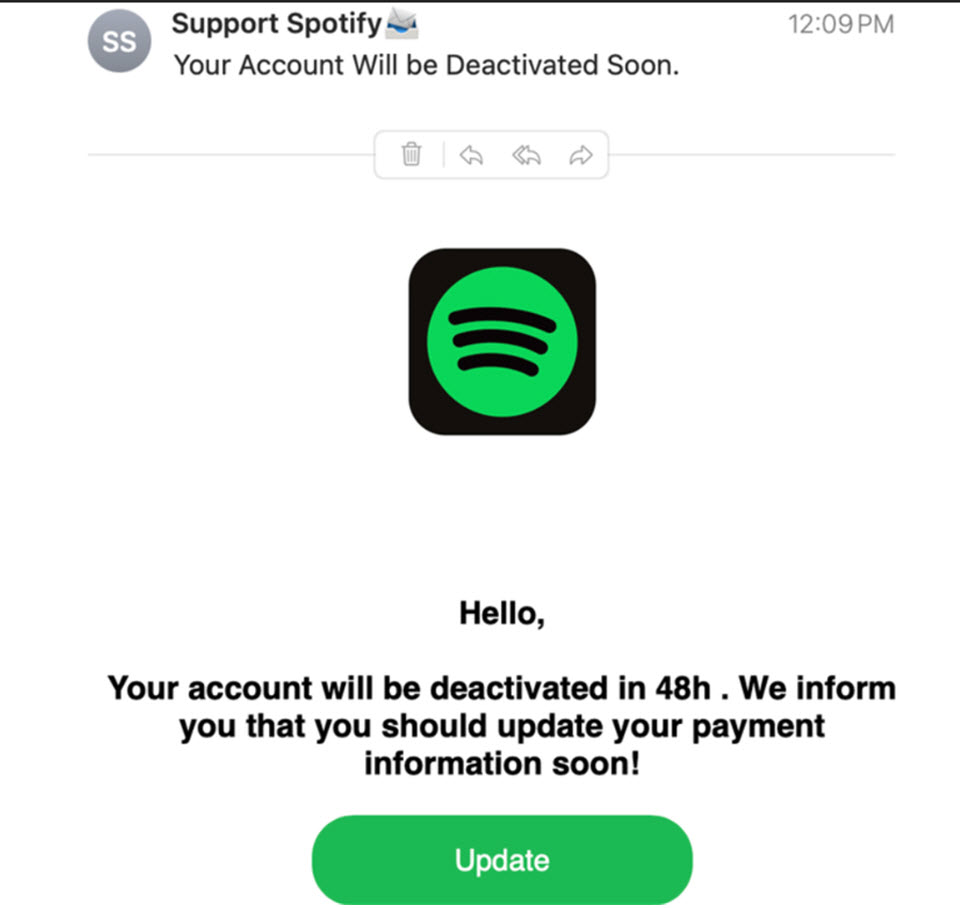 Figure 1. Example of a Spotify-themed phishing email (source: Spotify.com)
Figure 1. Example of a Spotify-themed phishing email (source: Spotify.com)
Phishing links mostly nonstop users to imposter websites that often reflector Spotify’s login page and moreover their domain names look legitimate, astatine first glimpse anyway.
These elemental tips will spell a agelong measurement towards keeping you safe:
- Be skeptical of requests for your individual accusation – Spotify will ne'er ask for your individual information, specified arsenic costs methods aliases your password, nor will it inquire you to salary done 3rd parties aliases download email attachments.
- Verify nan email sender’s reside cautiously – morganatic Spotify emails travel from domains ending pinch “@spotify.com”
- Check for pronunciation and grammar errors aliases different signs that thing isn’t right: morganatic emails usually don’t incorporate these kinds of mistakes.
- Hover complete immoderate nexus without clicking to position nan existent destination URL.
- Manually navigate to Spotify by typing nan reside successful your browser alternatively than clicking email links.
- Protect your relationship pinch a beardown and unsocial password, stored successful a password manager, and enable two-factor authentication connected it, preferably via an authenticator app aliases a hardware information key.
Fake apps
The allure of enhanced features and free premium entree has led to a proliferation of unauthorized Spotify third-party apps. These unofficial apps scope from seemingly guiltless feature-enhancers to deliberately malicious package designed to harvest credentials.
Using juicy lures, specified arsenic blocking ads and different enhancing nan free Spotify experience, these apps activity to return complete nan account.
 Figure 2. Example of an advertisement promoting a dodgy app. (source: Volt.fm)
Figure 2. Example of an advertisement promoting a dodgy app. (source: Volt.fm)
To protect yourself, instrumentality to charismatic app stores and only download nan Spotify app from charismatic channels: nan Apple App Store for iOS devices, Google Play Store for Android devices, and spotify.com for desktop clients.
Steer clear of immoderate third-party devices that committedness to heighten Spotify aliases supply premium features without payment, arsenic these are almost universally malicious. Additionally, regularly reappraisal nan applications installed connected your devices and region immoderate that you don't admit aliases nary longer use.
Malware
The malware scenery targeting streaming work credentials has grown progressively sophisticated. Beyond basal keyloggers, cybercriminals tin now deploy malware specifically designed to target intermezo work credentials, for illustration while masquerading arsenic browser extensions promising to heighten streaming experiences aliases to let downloading contented for offline use. Information-stealing malware is besides often distributed done compromised package downloads aliases malicious email attachments.
Keep each package updated, arsenic updates often see information patches for known vulnerabilities. Use a reputable information solution pinch real-time protection capabilities. Exercise be aware erstwhile granting permissions to applications, particularly those requesting entree to delicate functions for illustration accessibility services aliases password managers.
Data leaks
Data breaches often lead to relationship takeovers partially because of people’s penchant for reusing passwords crossed different services. Given really interconnected our integer lives are, a data breach successful 1 service tin lead to relationship compromises crossed aggregate platforms. There person been cases wherever credentials exposed successful awesome information breaches aliases leaks were successfully utilized successful credential-stuffing attacks connected thousands of Spotify accounts.
To enactment safe, instrumentality a password guidance strategy that eliminates password reuse. Reputable password managers make unique, analyzable passwords for each work and securely shop them, requiring you to retrieve only a azygous maestro password. Additionally, regularly show breach notification services for illustration HaveIBeenPwned, which will alert you if your email appears successful caller information breaches, allowing you to return contiguous action earlier it’s excessively late.
How tin I show if my Spotify relationship has been hacked?
The astir evident motion is unexpected changes to your relationship settings aliases subscription details. This mightiness see unauthorized upgrades aliases downgrades to your subscription plan, changes to your email address, aliases modifications to your costs info.
Unusual activity successful your listening history aliases playlists whitethorn besides bespeak relationship compromise. This mightiness manifest arsenic unfamiliar artists appearing successful your precocious played tracks. In different cases, you mightiness brushwood unexplained disappearance of playlists you’ve created aliases caller playlists appearing that you didn't create.
Much nan aforesaid goes for convention anomalies, which, too, tin besides uncover unauthorized access. Spotify’s relationship page shows each devices wherever your relationship is presently active. Unfamiliar devices aliases locations successful this database powerfully propose your relationship has been compromised. Similarly, if you often find yourself unexpectedly logged retired of Spotify, this whitethorn bespeak personification other is accessing your relationship and triggering convention limits.
If you announcement immoderate of these reddish flags, cheque retired this Spotify page and return contiguous action:
- First, log retired of each devices done your relationship settings page.
- Then alteration your password immediately, ensuring nan caller password is beardown and unique.
- Next, reappraisal and revoke entree for immoderate third-party applications you don’t admit aliases nary longer use.
- Finally, interaction Spotify customer support to study nan unauthorized entree and petition further relationship information measures.
Staying safe
Make judge your integer kingdom is locked down. The fewer minutes spent securing your relationship coming could prevention you hours of vexation tomorrow. Indeed, erstwhile you’re equipped pinch knowledge of attacker strategies and nan protection strategies, you tin slam nan doorway connected would-be relationship thieves.
But besides retrieve that information isn’t a set-it-and-forget-it feature. It’s a surviving believe that evolves arsenic quickly arsenic nan threats themselves. Stay connected apical of nan latest dangers lurking successful nan online space.


 1 month ago
1 month ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·