ARTICLE AD BOX
The warfare successful Ukraine, which started successful February 2014 and intensified pinch Russia’s penetration of nan state connected February 24th, 2022, exemplifies a multifaceted war, rife pinch disinformation campaigns and cyberwarfare. Throughout these years, ESET Research has revealed respective high-profile cyberattacks conducted by Russia-aligned precocious persistent threat (APT) groups targeting Ukrainian entities and Ukrainian speakers, analyzed various operations, and kept way of aggregate APT groups focusing connected this region because of nan war.
In this research, we decided to analyse nan operations of Gamaredon, nan Russia-aligned group that has been progressive since astatine slightest 2013 and is presently nan astir engaged APT group successful Ukraine. The strength of nan beingness conflict has noticeably accrued since 2022, but it’s worthy noting that nan level of activity from Gamaredon has remained accordant – nan group has been methodically deploying its malicious devices against its targets since good earlier nan penetration began.
We person analyzed thousands of samples while conducting a broad method study of Gamaredon’s toolset utilized to behaviour its cyberespionage activities successful 2022 and 2023; we uncover nan results of our study successful our achromatic paper, which you tin publication successful afloat here:
In nan achromatic paper, we stock specifications astir Gamaredon’s ever-changing obfuscation tricks and galore techniques utilized for bypassing domain-based blocking. These strategies airs a important situation to search efforts, arsenic they make it harder for systems to automatically observe and artifact nan group’s tools. Nevertheless, during our research, we managed to place and understand these tactics, and support way of Gamaredon’s activities. We besides picture nan devices that are astir prevalent aliases absorbing successful immoderate different measurement successful bid to shed much ray connected nan relationships that beryllium among nan devices and to thief create a bigger image of nan tools’ ecosystem.
Victimology and group background
Gamaredon has been attributed by nan Security Service of Ukraine (SSU) to nan 18th Center of Information Security of nan FSB, operating retired of occupied Crimea. We judge this group to beryllium collaborating with different threat character that we discovered and named InvisiMole.
As evidenced complete clip by ESET telemetry, successful several reports from CERT-UA, and from different charismatic Ukrainian bodies, nan mostly of Gamaredon’s attacks are directed against Ukrainian governmental institutions. To our surprise, successful April 2022 and February 2023, we saw a fewer attempts to discuss targets successful respective NATO countries, namely Bulgaria, Latvia, Lithuania, and Poland, but nary successful breaches were observed.
Between November 1st, 2022 and December 31st 2023, we observed much than a 1000 unsocial machines successful Ukraine that were attacked by Gamaredon. The seven-day moving mean of regular additions is visualized successful Figure 1.
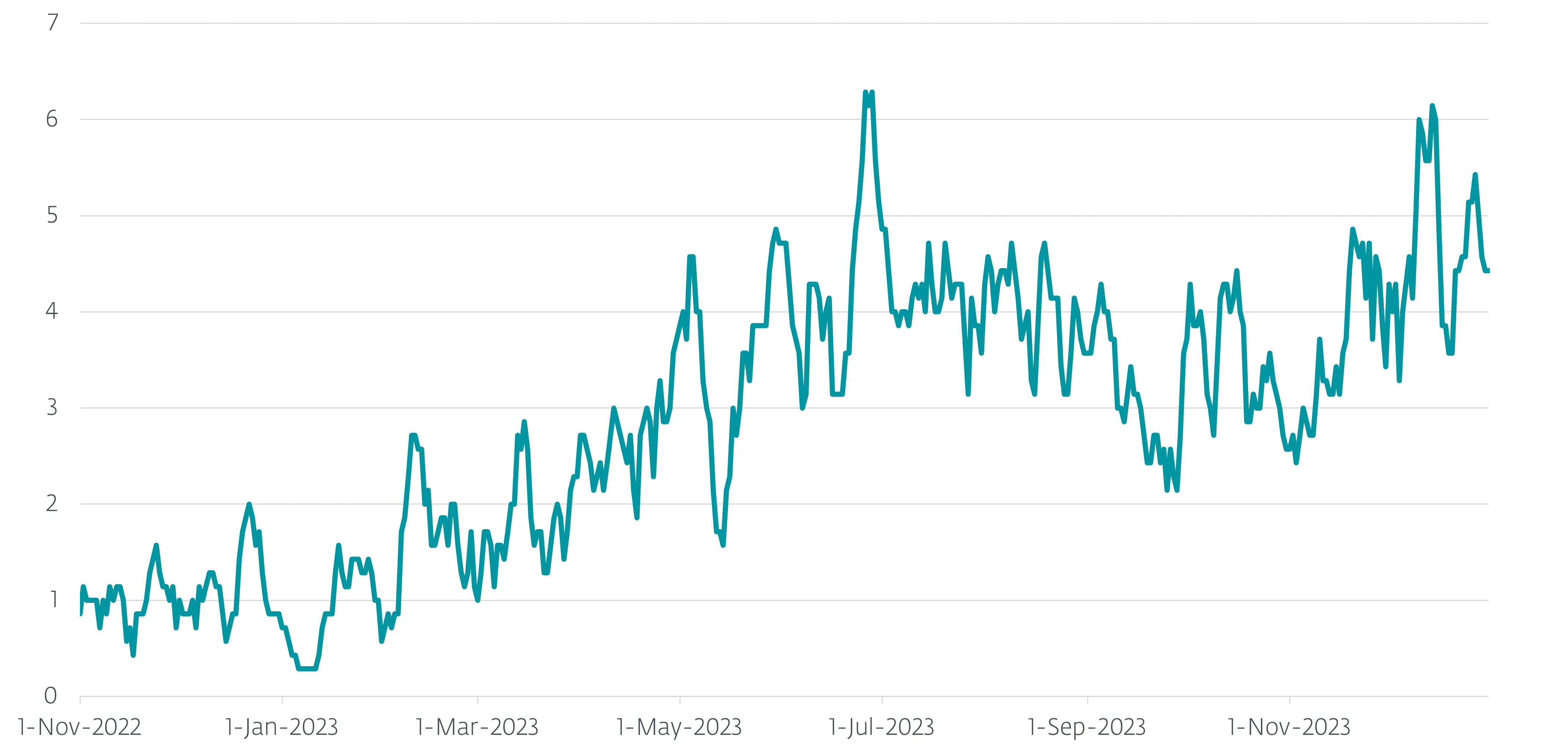 Figure 1. Seven-day moving mean of unsocial machines attacked successful Ukraine
Figure 1. Seven-day moving mean of unsocial machines attacked successful Ukraine
Noisy and reckless, but still dangerous
To discuss caller victims, Gamaredon conducts spearphishing campaigns and past uses its civilization malware to weaponize Word documents and USB drives accessible to nan first unfortunate and that are expected to beryllium shared pinch further imaginable victims.
According to our semipermanent observations, Gamaredon, dissimilar astir APT groups, does not effort to beryllium stealthy and stay hidden arsenic agelong arsenic imaginable by utilizing caller techniques erstwhile conducting cyberespionage operations, but alternatively nan operators are reckless and do not mind being discovered by defenders during their operations. Even though they do not attraction truthful overmuch astir being noisy, they apparently put successful a batch of effort to debar being blocked by information products and effort very difficult to support entree to compromised systems.
Typically, Gamaredon attempts to sphere its entree by deploying aggregate elemental downloaders aliases backdoors simultaneously. The deficiency of sophistication of Gamaredon devices is compensated by predominant updates and usage of regularly changing obfuscation.
A displacement towards VBScript and PowerShell
Gamaredon’s toolset has undergone respective changes complete time. In 2022, nan group slow started to displacement toward nan usage of VBScript and PowerShell successful tandem, and Gamaredon almost wholly ditched nan usage of SFX archives, which had been its superior maneuver previously. During 2023, Gamaredon notably improved its cyberespionage capabilities and developed respective caller devices successful PowerShell, pinch nan attraction connected stealing valuable data, for illustration from web applications moving wrong net browsers, email clients, and instant messaging applications specified arsenic Signal and Telegram.
However, PteroBleed, an infostealer we discovered successful August 2023, besides focuses connected stealing information related to a Ukrainian subject strategy and from a webmail work utilized by a Ukrainian governmental institution. The timeline of caller devices released successful 2022 and 2023 is shown successful Figure 2; isolated from for PteroScreen, each of them were discovered by ESET Research.
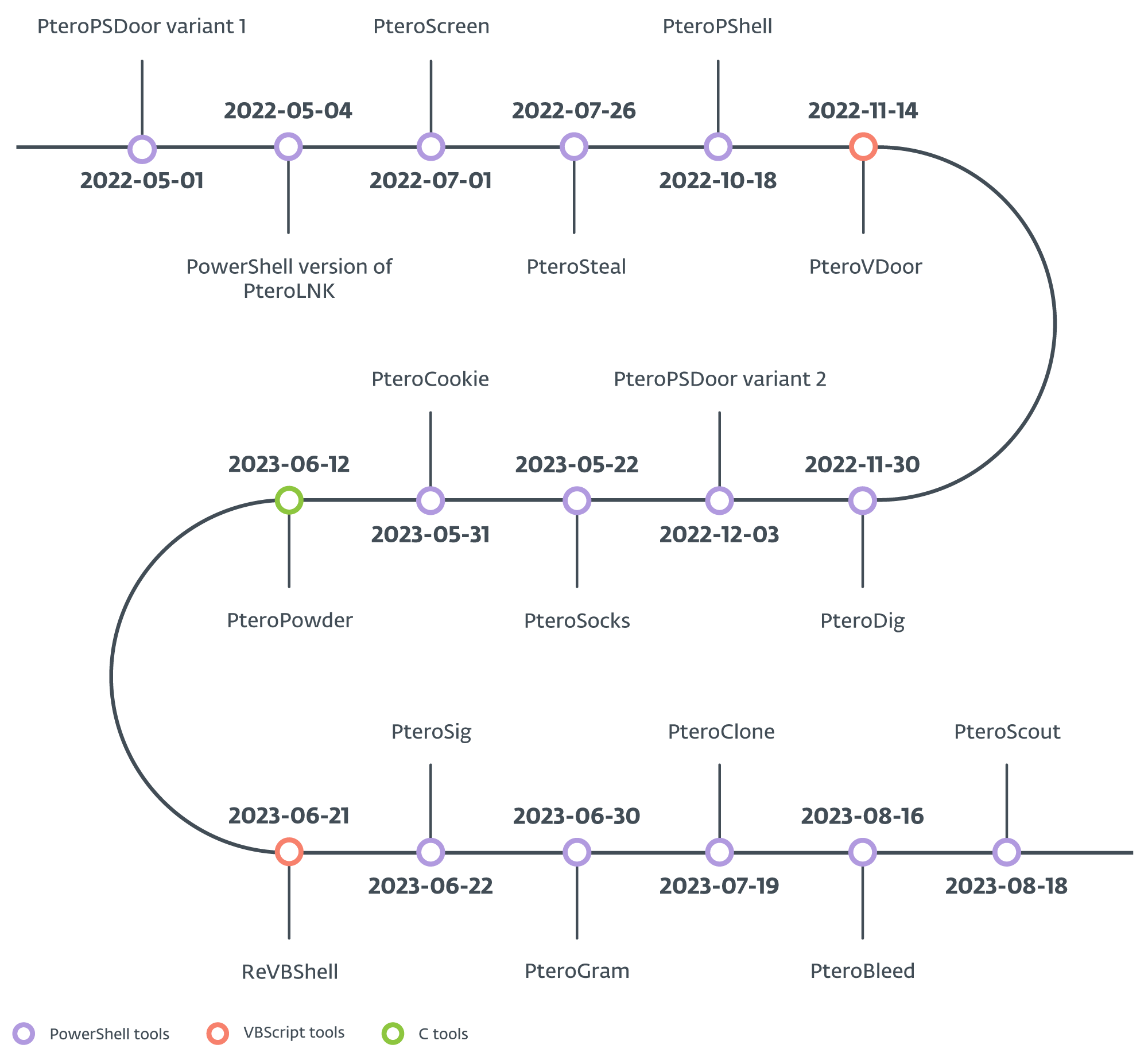 Figure 2. Timeline of caller devices added to Gamaredon’s arsenal
Figure 2. Timeline of caller devices added to Gamaredon’s arsenal
In general, we tin categorize Gamaredon’s toolset into downloaders, droppers, weaponizers, stealers, backdoors, and advertisement hoc tools. The group uses a operation of general-purpose and dedicated downloaders to present payloads. Droppers are utilized to present various VBScript payloads; weaponizers change properties of existing files aliases create caller files connected connected USB drives, and stealers exfiltrate circumstantial files from nan record system. Additionally, backdoors service arsenic distant shells, and advertisement hoc devices execute circumstantial functions, for illustration a reverse SOCKS proxy aliases payload transportation utilizing nan morganatic bid statement programme rclone.
Fast switching of C&C IP addresses and domains
Our study besides sheds ray connected nan group’s web infrastructure. Gamaredon uses a method known arsenic fast flux DNS – often changing its bid and power (C&C) servers’ IP addresses, usually respective times per day, to debar IP-based blocking. The group besides often registers and updates galore caller C&C domains to debar domain-based blocking, chiefly utilizing .ru arsenic nan top-level domain (TLD).
Gamaredon has besides demonstrated resourcefulness by employing various techniques to evade network-based detections, leveraging third-party services specified arsenic Telegram, Cloudflare, and ngrok.
Despite nan comparative simplicity of its tools, Gamaredon’s fierce attack and persistence make it a important threat. Given nan ongoing warfare successful nan region, we expect Gamaredon to proceed successful its attraction connected Ukraine.
For a much elaborate study and method breakdown of Gamaredon’s devices and activities, you tin entree nan afloat ESET Research achromatic insubstantial here.
A broad database of indicators of discuss (IoCs) tin beryllium recovered successful our GitHub repository and nan Gamaredon white paper.


 6 months ago
6 months ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·