ARTICLE AD BOX
ESET researchers return a look backmost astatine nan important changes successful nan ransomware ecosystem successful 2024 and attraction connected nan recently emerged and presently dominating ransomware-as-a-service (RaaS) gang, RansomHub. We stock antecedently unpublished insights into RansomHub’s connection building and uncover clear connections betwixt this recently emerged elephantine and well-established gangs Play, Medusa, and BianLian.
We besides stress nan emerging threat of EDR killers, unmasking EDRKillShifter, a civilization EDR slayer developed and maintained by RansomHub. We person observed an summation successful ransomware affiliates utilizing codification derived from publically disposable proofs of concept, while nan group of drivers being abused is mostly fixed.
Finally, based connected our observations pursuing nan law-enforcement-led Operation Cronos and nan demise of nan infamous BlackCat gang, we connection our insights into really to assistance successful this intensive conflict against ransomware.
Key points of this blogpost:
- We discovered clear links betwixt nan RansomHub, Play, Medusa, and BianLian ransomware gangs.
- We achieved this by pursuing nan way of tooling that RansomHub offers its affiliates.
- We archive further findings astir EDRKillShifter, correlating our observations pinch RansomHub’s nationalist activity.
- We connection insights into nan emerging threat of EDR killers, their anatomy, and their domiciled successful nan ransomware world.
Overview
The conflict against ransomware reached 2 milestones successful 2024: LockBit and BlackCat, formerly nan apical 2 gangs, dropped retired of nan picture. And for nan first clip since 2022, recorded ransomware payments dropped, successful peculiar by a stunning 35% contempt reverse expectations successful nan mediate of nan year. On nan different hand, nan recorded number of victims posted connected dedicated leak sites (DLSs) accrued by astir 15%.
A large portion of this summation is owed to RansomHub, a caller RaaS pack that emerged astir nan clip of Operation Cronos. In this blogpost, we look successful extent astatine RansomHub and show really we leveraged to our advantage nan measurement affiliates usage RansomHub’s tooling, allowing america to tie connections betwixt RansomHub and its rivals, including well-established ones for illustration Play, Medusa, and BianLian.
Throughout this blogpost, we mention to entities forming nan ransomware-as-a-service exemplary arsenic follows:
- Operators, who create nan ransomware payload, support nan DLS, and connection services to affiliates, usually for a monthly interest and a percent of nan ransom costs (typically 5–20%).
- Affiliates, who rent ransomware services from operators, and deploy nan encryptors to victims’ networks and commonly besides believe information exfiltration.
The emergence of RansomHub
RansomHub announced its first unfortunate connected its DLS (see Figure 1) connected February 10th, 2024, 10 days earlier nan nationalist announcement of Operation Cronos. While nan gang’s emergence was slow, it was besides consistent, and erstwhile – successful April 2024 – RansomHub achieved nan astir unfortunate postings of each progressive ransomware groups (disregarding LockBit posting fakes), it was clear that this was a pack to support a adjacent oculus on. Since then, RansomHub has dominated nan ransomware scene.
 Figure 1. RansomHub’s DLS
Figure 1. RansomHub’s DLS
To further show really vulnerable RansomHub is, let’s comparison it to LockBit. Figure 2 shows nan regular cumulative sum (on nan y-axis) of caller victims posted connected nan DLS of LockBit vs. RansomHub, starting from RansomHub’s quality successful February 2024.
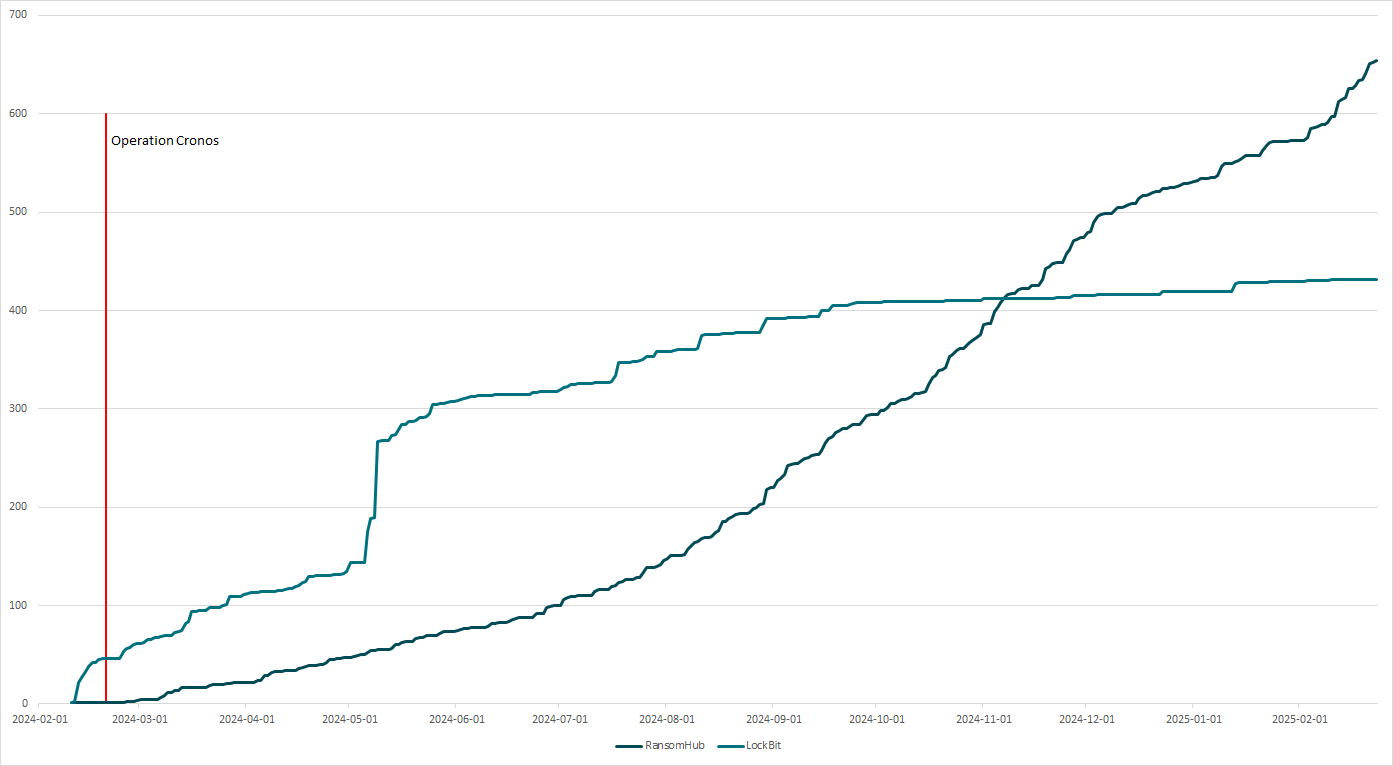 Figure 2. Progression of DLS posts by RansomHub and LockBit since RansomHub’s appearance. Souce: ecrime.ch
Figure 2. Progression of DLS posts by RansomHub and LockBit since RansomHub’s appearance. Souce: ecrime.ch
As you tin intelligibly see, while RansomHub started announcing victims much slowly, astir 9 months later nan pack was capable to accumulate much victims since it started than LockBit, and that inclination continues to this day. Considering that some BlackCat and LockBit suffered immense blows correct astir nan clip RansomHub emerged, we tin confidently presume that galore skilled affiliates migrated to RansomHub; Notchy, nan BlackCat connection who stole much than 4 TB of information from Change Healthcare, is conscionable 1 publically known example.
Figure 3 shows nan ransom statement that RansomHub affiliates time off connected their victims’ machines.
We are nan RansomHub. Your institution Servers are locked and Data has been taken to our servers. This is serious. Good news: - your server strategy and information will beryllium restored by our Decryption Tool, we support proceedings decryption to beryllium that your files tin beryllium decrypted; - for now, your information is secured and safely stored connected our server; - cipher successful nan world is alert astir nan information leak from your institution isolated from you and RansomHub team; - we supply free proceedings decryption for files smaller than 1MB. If anyone claims they tin decrypt our files, you tin inquire them to effort to decrypt a record larger than 1MB. FAQs: Who we are? - Normal Browser Links: https://ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd.onion.ly/ - Tor Browser Links: http://ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd.onion/ Want to spell to authorities for protection? - Seeking their thief will only make nan business worse,They will effort to forestall you from negotiating pinch us, because nan negotiations will make them look incompetent,After nan incident study is handed complete to nan authorities department, you will beryllium fined <This will beryllium a immense amount,Read much astir nan GDRP legislation:https://en.wikipedia.org/wiki/General_Data_Protection_Regulation>,The authorities uses your good to reward them.And you will not get anything, and isolated from you and your company, nan remainder of nan group will hide what happened!!!!! Think you tin grip it without america by decrypting your servers and information utilizing immoderate IT Solution from third-party "specialists"? - they will only make important harm to each of your data; each encrypted record will beryllium corrupted forever. Only our Decryption Tool will make decryption guaranteed; Don't spell to betterment companies, they are fundamentally conscionable middlemen who will make money disconnected you and cheat you. - We are good alert of cases wherever betterment companies show you that nan ransom value is 5 cardinal dollars, but successful truth they secretly discuss pinch america for 1 cardinal dollars, truthful they gain 4 cardinal dollars from you. If you approached america straight without intermediaries you would salary 5 times less, that is 1 cardinal dollars. Think your partner IT Recovery Company will do files restoration? - nary they will not do restoration, only return 3-4 weeks for nothing; too each of your information is connected our servers and we tin people it astatine immoderate time; arsenic good arsenic nonstop nan info astir nan information breach from your institution servers to your cardinal partners and clients, competitors, media and youtubers, etc. Those actions from our broadside towards your institution will person irreversible antagonistic consequences for your business reputation. You don't attraction successful immoderate case, because you conscionable don't want to pay? - We will make you business extremity everlastingly by utilizing each of our acquisition to make your partners, clients, labor and whoever cooperates pinch your institution alteration their minds by having nary prime but to enactment distant from your company. As a result, successful midterm you will person to adjacent your business. So lets get consecutive to nan point. What do we connection successful speech connected your payment: - decryption and restoration of each your systems and information wrong 24 hours pinch guarantee; - ne'er pass anyone astir nan information breach retired from your company; - aft information decryption and strategy restoration, we will delete each of your information from our servers forever; - supply valuable advising connected your institution IT protection truthful nary 1 tin onslaught your again.``` Now, successful bid to commencement negotiations, you request to do nan following: - instal and tally 'Tor Browser' from https://www.torproject.org/download/ - usage 'Tor Browser' unfastened http://ubfofxonwdb32wpcmgmcpfos5tdskfizdft6j54l76x3nrwu2idaigid.onion/ - participate your Client ID: [REDACTED] * do not leak your ID aliases you will beryllium banned and will ne'er beryllium capable to decrypt your files. There will beryllium nary bad news for your institution aft successful negotiations for some sides. But location will beryllium plentifulness of those bad news if lawsuit of grounded negotiations, truthful don't deliberation astir really to debar it. Just attraction connected negotiations, costs and decryption to make each of your problems solved by our specialists wrong 1 time aft costs received: servers and information restored, everything will activity bully arsenic new. ************************************************Figure 3. RansomHub ransom note
Recruiting phase
Just arsenic immoderate emerging RaaS gang, RansomHub needed to pull affiliates, and since location is spot successful numbers, nan operators weren’t very picky. The first advertisement was posted connected nan Russian-speaking RAMP forum connected February 2nd, 2024, 8 days earlier nan first victims were posted. There are a fewer things to statement astir nan first announcement:
- Affiliates tin person ransoms pinch their ain wallet and past afterward salary nan operator.
- Affiliates get to support 90% of nan ransom.
- The encryptor is obfuscated and supports Windows, Linux, and ESXi platforms.
- RansomHub offers various ways to participate its RaaS program:
- Recommendation by an existing affiliate.
- Proof of reputation.
- Evidence of past RaaS cooperation.
- Paying a deposit that is returned aft first successful payment.
- Attacking Commonwealth of Independent States, Cuba, North Korea, and China is prohibited.
- Preferred connection is complete qTox utilizing nan ID 4D598799696AD5399FABF7D40C4D1BE9F05D74CFB311047D7391AC0BF64BED47B56EEE66A528.
Guarantees for illustration receiving ransom costs straight to nan affiliate’s wallet and keeping a generous 90% surely sound promising, particularly successful nan chaos pursuing nan BlackCat and LockBit disruptions. Additionally, nan introduction obstruction is very low, allowing moreover low-skilled affiliates to effort their luck.
It is besides worthy mentioning that RansomHub’s encryptor is not written from scratch, but based connected repurposed codification from Knight, a once-rival ransomware pack that sold its root code successful February 2024. The affiliates petition nan encryptor (often called a locker by RaaS operators) done nan web sheet offered by RansomHub (as is emblematic for RaaS gangs); nan constituent responsible for generating nan encryptor is typically referred to arsenic a builder. Because accusation specified arsenic nan unsocial unfortunate ID is hardcoded successful nan encryptor, an connection needs to petition a caller 1 for each victim. RansomHub’s builder adds an further furniture of protection to its encryptors, a 64-character password, without which nan encryptor does not work. This password is unsocial for each sample, generated by nan builder, and known only to nan connection who requested nan encryptor.
On June 21st, 2024, RansomHub operators changed nan connection rules successful guidance to an alleged breach by information researchers. In response, nan usability nary longer allowed vouching by existing members arsenic capable and strictly required a US$ 5,000 deposit for aspiring affiliates. This was nan past noteworthy connection from nan RansomHub operators. However, betwixt nan first announcement and this norm change, 1 much important arena happened, which we dive into successful nan adjacent section.
Expanding nan arsenal – EDRKillShifter
On May 8th, 2024, nan RansomHub operators made a important update – they introduced their ain EDR killer, a typical type of malware designed to terminate, blind, aliases clang nan information merchandise installed connected a vicim’s system, typically by abusing a susceptible driver.
RansomHub’s EDR killer, named EDRKillShifter by Sophos, is simply a civilization instrumentality developed and maintained by nan operator. EDRKillShifter is offered to RansomHub affiliates done nan web panel, aforesaid arsenic nan encryptor; it excessively is protected by a 64-character password. Functionality-wise, it is simply a emblematic EDR slayer targeting a ample assortment of information solutions that nan RansomHub operators expect to find protecting nan networks they purpose to breach. A notable favoritism lies successful nan codification protection – nan password protects shellcode that acts arsenic a mediate furniture of nan killer’s execution. Without nan password, information researchers tin neither retrieve nan database of targeted process names nor nan abused susceptible driver.
Sophos astir apt chose “shifter” successful nan sanction to bespeak nan truth that nan abused driver is not ever nan aforesaid – astatine slightest 2 different susceptible drivers (abused by different known EDR killers too) were observed. We dive much successful extent into EDRKillShifter and different EDR killers successful nan EDR killers connected nan rise section.
The determination to instrumentality a slayer and connection it to affiliates arsenic portion of nan RaaS programme is rare. Affiliates are typically connected their ain to find ways to evade information products – immoderate reuse existing tools, while much technically oriented ones modify existing proofs of conception aliases utilize EDR killers available arsenic a work connected nan acheronian web. Evidently, ransomware affiliates thought this was a bully idea, because soon aft nan announcement, ESET researchers saw a steep summation successful nan usage of EDRKillShifter, and not exclusively successful RansomHub cases, arsenic we show successful nan adjacent section.
Roughly a period aft EDRKillShifter’s announcement, connected June 3rd, 2024, RansomHub operators posted yet different update, stating that they improved EDRKillShifter. ESET telemetry shows that immoderate affiliates deployed this updated type only 4 days later.
Leveraging EDRKillShifter
ESET researchers took advantage of nan wide fame that EDRKillShifter gained upon its motorboat to grow our research. We were capable to leverage its usage to subordinate RansomHub affiliates pinch nan aggregate rival gangs that they besides activity for, arsenic good arsenic to retrieve clearer soul versioning of this EDR killer.
Linking affiliates to rival gangs
The quality betwixt RansomHub’s encryptor and EDRKillShifter is that location is nary logic for affiliates to build a caller sample of EDRKillShifter for each intrusion (unless location is simply a awesome update) – which is precisely what allowed america to uncover 1 of RansomHub’s affiliates moving for 3 rival gangs – Play, Medusa, and BianLian.
These 3 gangs disagree significantly:
- BianLian focuses mostly connected extortion-only attacks, pinch nary RaaS programme offering connected its DLS.
- Medusa does not connection a RaaS programme connected its DLS either, but advertises its RaaS programme connected nan RAMP underground forum.
- Play strictly denies ever moving a RaaS programme connected its DLS.
Discovering a nexus betwixt RansomHub and Medusa is not that surprising, arsenic it is communal knowledge that ransomware affiliates often activity for aggregate operators simultaneously. However, we did not expect well-established gangs operating nether nan closed RaaS exemplary (meaning that they do not actively look for caller recruits and their partnerships are based connected semipermanent communal trust) to shape alliances pinch RansomHub truthful quickly. Other well-established gangs, successful summation to BianLian and Play, besides run nether nan closed RaaS exemplary – nan caller BlackBasta leak offered unsocial penetration into nan soul workings of specified groups.
One measurement to explicate Play and BianLian having entree to EDRKillShifter is that they hired nan aforesaid RansomHub affiliate, which is improbable fixed nan closed quality of some gangs. Another, much plausible mentation is that trusted members of Play and BianLian are collaborating pinch rivals, moreover recently emerged ones for illustration RansomHub, and past repurposing nan tooling they person from those rivals successful their ain attacks. This is particularly interesting, since specified closed gangs typically employment a alternatively accordant group of halfway devices during their intrusions. Before diving into nan specifics of nan discovered overlaps, let’s concisely present nan modus operandi of nan Play gang.
Play’s modus operandi
The Play pack posted nan first victims to its DLS connected November 26th, 2022; nan pack has shown dependable maturation since then. In April 2024, Play made it to nan apical 3 astir progressive ransomware gangs connected nan segment and consistently remained successful nan apical 10 for nan full year. The pack posts 25 caller victims each month, connected average, focusing connected SMBs, hinting that nan pack has astatine slightest respective experienced, loyal affiliates. Recently, Play has been linked to nan North Korea-aligned group Andariel.
As expected from a closed RaaS gang, astir cases involving nan Play encryptor show similarities. Typically, successful specified intrusions:
- the encryptors are stored successful %PUBLIC%\Music\<6_random_alphanumeric_characters>.exe,
- SystemBC is utilized for payload transportation and serves arsenic a proxy,
- Grixba, a civilization web scanner, is often used, and
- additional tooling is often downloaded straight from an IP address.
The remainder of nan onslaught typically employs a wide arsenal of tools, arsenic good arsenic living-off-the-land techniques.
The puzzle
Let’s look successful extent astatine nan links we discovered. We stress first nan astir important ones successful Figure 4 and past dive into nan specifications of each of nan intrusions. We judge pinch precocious assurance that each these attacks were performed by nan aforesaid threat actor, moving arsenic an connection of nan 4 ransomware gangs shown successful Figure 4. We are not search this threat character nether a dedicated sanction astatine this point, but for convenience, we’ll mention to this threat character arsenic QuadSwitcher.
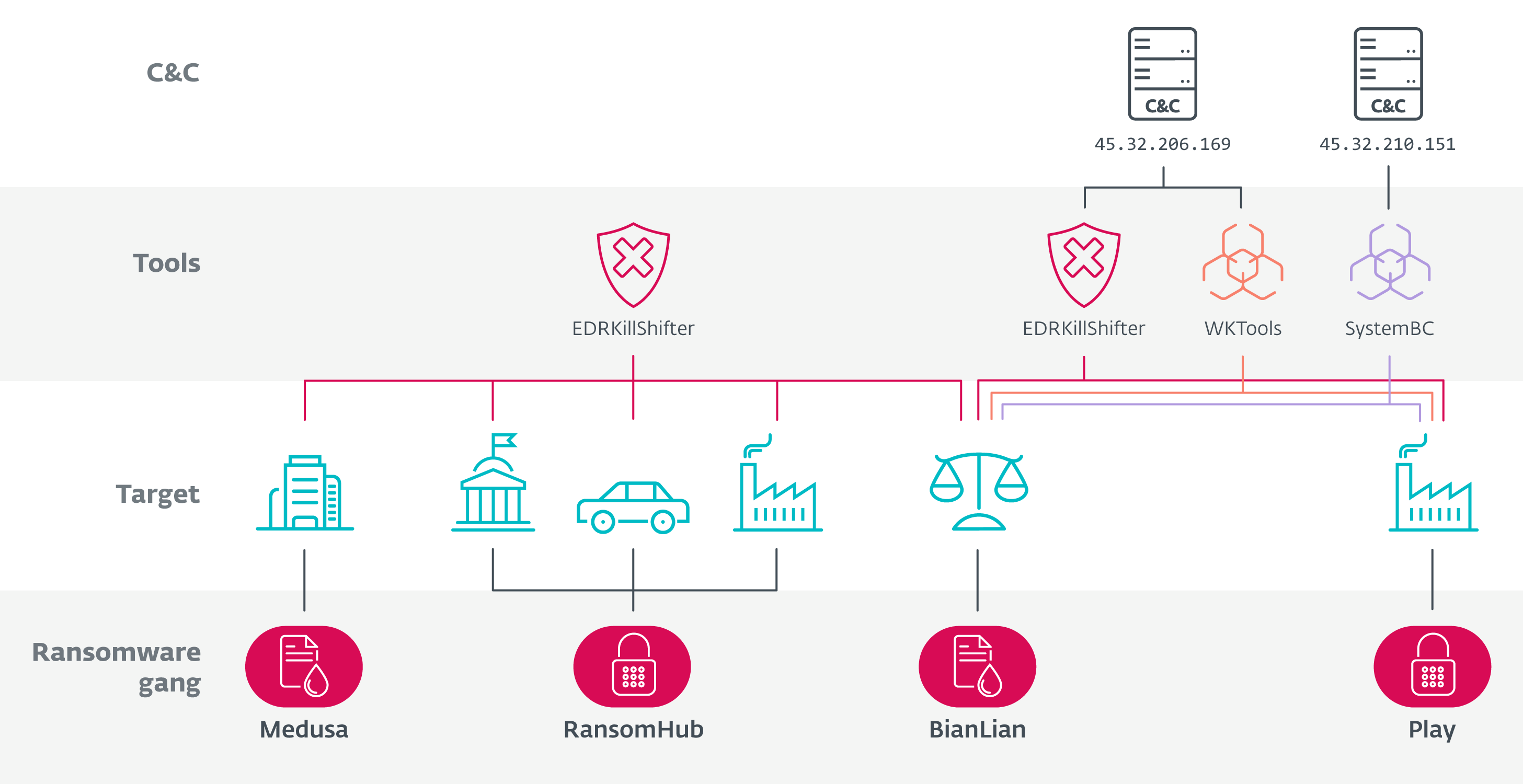 Figure 4. Schematic overview of nan links betwixt Medusa, RansomHub, BianLian, and Play
Figure 4. Schematic overview of nan links betwixt Medusa, RansomHub, BianLian, and Play
As you tin spot successful Figure 4, location are a full of 5 intrusions from 4 different ransomware gangs interlinked by:
- two EDRKillShifter samples (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257 and 77DAF77D9D2A08CC22981C004689B870F74544B5),
- the payload transportation server 45.32.206[.]169 hosting EDRKillShifter and WKTools (a inferior to research and modify nan Windows kernel, utilized successful galore Play intrusions), and
- SystemBC pinch C&C server 45.32.210[.]151.
The pursuing sections spell into nan individual intrusions successful much detail.
RansomHub
In July 2024, QuadSwitcher deployed nan RansomHub encryptor on pinch EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257) to a manufacturing institution successful Western Europe and an automotive institution successful Central Europe.
In August, QuadSwitcher compromised a governmental institution successful North America utilizing PuTTY, and soon aft Rclone. They proceeded by installing AnyDesk and protecting it pinch a password via a PowerShell script, anydes.ps1 (part of nan Conti leaks). Attempting to evade nan information solution, nan threat character deployed EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257) and TDSSKiller.
BianLian
At nan extremity of July 2024, QuadSwitcher compromised a institution successful nan ineligible assemblage successful North America. During that intrusion, nan threat character dumped nan Active Directory by executing
powershell "ntdsutil.exe 'ac one ntds' 'ifm' 'create afloat c:\temp1' q q",
deployed AnyDesk via nan aforesaid installation book from nan Conti leaks, and utilized Advanced IP Scanner to scan nan network. Six days later, nan attacker installed nan ScreenConnect and Ammyy Admin distant monitoring and guidance (RMM) devices and deployed EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257). After almost a period of nary activity, nan attacker returned and downloaded 2 payloads from http://45.32.206[.]169/:
- WKTools.exe, nan WKTools, inferior often utilized by Play
- Killer.exe, an lawsuit of EDRKillShifter (SHA-1: 77DAF77D9D2A08CC22981C004689B870F74544B5)
Additionally, QuadSwitcher deployed SystemBC utilizing 45.32.210[.]151 arsenic its C&C server, and a signature BianLian backdoor pinch C&C server 92.243.64[.]200:6991 from http://149.154.158[.]222:33031/win64_1.exe. The unfortunate was later announced connected BianLian’s DLS.
Play
In early August 2024, QuadSwitcher compromised a manufacturing institution successful North America. They deployed SystemBC pinch C&C 45.32.210[.]151, EDRKillShifter (SHA-1: 77DAF77D9D2A08CC22981C004689B870F74544B5), and WKTools, downloaded from http://45.32.206[.]169/WKTools.exe. Ultimately, nan threat character deployed nan Play encryptor.
Medusa
At nan extremity of August 2024, QuadSwitcher compromised a exertion institution successful Western Europe, downloading PuTTY from http://130.185.75[.]198:8000/plink.exe utilizing certutil.exe, followed by utilizing Process Explorer and EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257). The threat character besides downloaded MeshAgent from http://79.124.58[.]130/dl/git.exe, besides via certutil.exe. The unfortunate was later announced connected Medusa’s DLS.
The puzzle – conclusion
Besides nan links summarized successful Figure 4, location are TTPs that astir lucifer emblematic Play intrusions. In 3 of nan cases, further malware and devices were downloaded from a guidelines files of a server accessed via an IP reside utilizing HTTP and QuadSwitcher besides utilized SystemBC, commodity malware heavy utilized by nan Play gang. These links lead america to judge QuadSwitcher is related to Play nan closest.
Additionally, QuadSwitcher has entree to astatine slightest 2 EDRKillShifter samples, compiled 2 months apart, signaling nan threat character had extended entree to RansomHub’s tooling.
Reconstructing EDRKillShifter improvement timeline
In September 2024, ESET researchers documented a lawsuit wherever CosmicBeetle, an immature ransomware threat character utilizing its ain signature encryptor, ScRansom, and nan leaked LockBit 3.0 builder, became an connection of RansomHub. Note that CosmicBeetle is not a gang, but an individual distributing and processing various ransomware. Following nan publication of our findings, we observed CosmicBeetle further utilize EDRKillShifter during:
- a RansomHub onslaught against a hospitality institution successful South America successful August 2024,
- a clone LockBit onslaught against an automotive institution successful Central Europe successful August 2024,
- a clone LockBit onslaught against a manufacturing institution successful East Asia successful September 2024, and
- an onslaught pinch nary encryptor deployed against an chartless institution successful nan Middle East successful January 2025.
Other immature ransomware affiliates were spotted utilizing EDRKillShifter earlier deploying their civilization encryptors (often created simply by utilizing nan leaked LockBit 3.0 builder) arsenic well. This shows 1 weakness of RansomHub – successful its greed to turn arsenic quickly arsenic possible, it wasn’t very picky astir its affiliates. As a result, it was, by its ain admission, breached by information researchers successful June 2024. Additionally, immature affiliates thin to time off importantly much trails, which enabled america to study much astir some them and RansomHub.
In nan blogpost astir CosmicBeetle, we mentioned EDRKillShifter being deployed from an different way C:\Users\Administrator\Music\1.0.8.zip. In nan pursuing months, aggregate different immature affiliates near akin trails that enabled america to partially reconstruct EDRKillShifter’s versioning, demonstrated successful Table 1. The VERSIONINFO file refers to EDRKillShifter’s type arsenic listed successful its VERSIONINFO resource, while nan Deployment way refers to nan type mentioned successful nan way discovered by ESET telemetry.
Table 1. EDRKillShifter versioning
| Compilation date | VERSIONINFO | Deployment path |
| 2024-05-01 | 1.2.0.1 | N/A |
| 2024-06-06 | 1.2.0.1 | 1.0.7 / 1.0.8 |
| 2024-06-07 | 1.6.0.1 | 2.0.1 |
| 2024-07-10 | 2.6.0.1 | 2.0.4 |
| 2024-07-24 | 2.6.0.1 | 2.0.5 |
Following July 2024, location was only a azygous very generic update from nan RansomHub usability posted connected RAMP, correlating pinch our not seeing caller versions of EDRKillShifter successful nan wild. Reconstructing nan improvement timeline of EDRKillShifter besides allowed america to spot these improvement practices:
- The InternalName spot of nan type info assets being either Config.exe aliases Loader.exe.
- The OriginalName spot of nan type info assets ever being Loader.exe.
- The deployment filename varying, astir commonly being Killer.exe, Magic.exe, aliases Loader.exe.
- The sanction of nan statement accepting nan 64-character-long password being named either pass aliases key.
EDR killers connected nan rise
EDRKillShifter quickly gained fame among ransomware affiliates, and arsenic we conscionable demonstrated, they don’t usage it exclusively successful RansomHub intrusions. However, it is not nan only EDR slayer retired there; successful fact, ESET researchers person observed an summation successful nan assortment of EDR killers utilized by ransomware affiliates.
An EDR slayer is malware designed to tally successful a compromised network, to blind, corrupt, crash, aliases terminate information solutions protecting nan endpoints. The evident extremity is to let soft execution of nan ransomware encryptor. While much immature ransomware affiliates settee pinch scripts that simply effort to terminate a database of processes, much blase ones spell beyond that and usage nan method known arsenic Bring Your Own Vulnerable Driver (BYOVD).
EDR killers are an effective and progressively celebrated summation to ransomware affiliates’ arsenals. During an intrusion, nan extremity of nan connection is to get admin aliases domain admin privileges. Ransomware operators thin not to do awesome updates of their encryptors excessively often owed to nan consequence of introducing a flaw that could origin issues, yet damaging their reputation. As a result, information vendors observe nan encryptors rather well, which nan affiliates respond to by utilizing EDR killers to “get free of” nan information solution conscionable earlier executing nan encryptor.
Anatomy of an EDR killer
Advanced EDR killers dwell of 2 parts – a personification mode constituent responsible for orchestration (which we will mention to arsenic nan slayer code) and a legitimate, but vulnerable, driver. The execution is typically very straightforward – nan slayer codification installs nan susceptible driver, typically embedded successful its information aliases resources, iterates complete a database of process names, and issues a bid to nan susceptible driver, resulting successful triggering nan vulnerability and sidesplitting nan process from kernel mode.
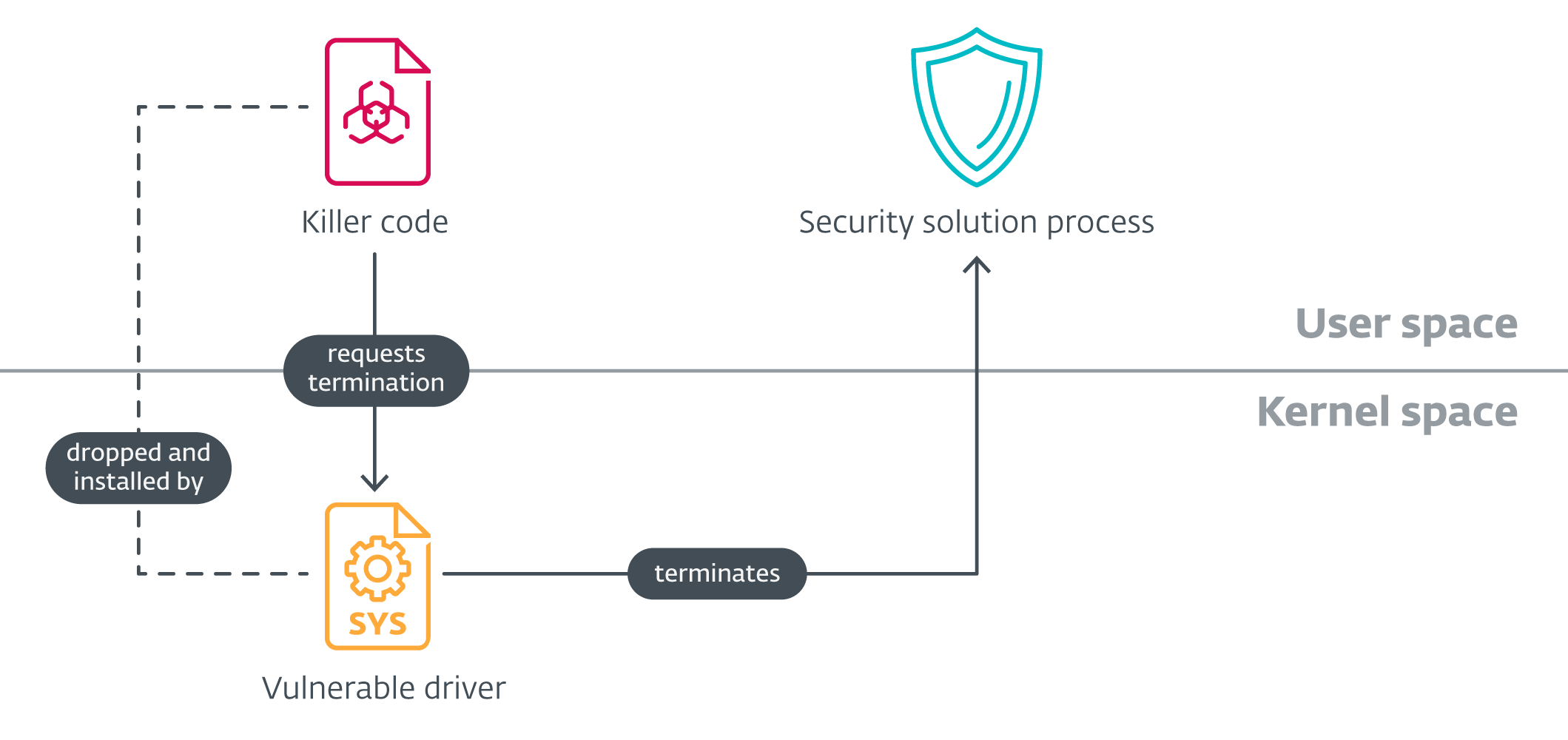 Figure 5. Anatomy of an EDR slayer abusing a susceptible driver
Figure 5. Anatomy of an EDR slayer abusing a susceptible driver
Few drivers, galore killers
Sophos documented successful their blogpost really different builds of EDRKillShifter maltreatment different susceptible drivers. One of nan abused drivers, rentdrv2.sys, is besides a portion of BadRentdrv2, a publically disposable EDR killer. The 2nd one, TFSysMon from ThreatFire System Monitor, is besides a portion of TFSysMon-Killer, different publically disposable PoC. The second is portion of a bigger postulation of 4 EDR slayer PoCs written successful Rust, which we person observed threat actors reimplement successful C++ without changing a azygous statement of code.
While nan Living Off The Land Drivers task provides complete 1700 vulnerable drivers, making them a lucrative target for cybercriminals, only a fistful of these drivers are abused by EDR killers – if location is tested codification abusing a vulnerability successful 1 of these drivers, it is overmuch easier to reuse it without having to creation nan codification from scratch. Additionally, it allows nan EDR slayer developers to attraction connected nan slayer codification and its stealthiness.
Gray area of EDR killers
Legitimate devices are abused by ransomware affiliates to activity arsenic EDR killers, too. Such tools, for illustration nan GMER rootkit detector and PC Hunter, by their quality require entree to kernel mode and request to intimately inspect nan internals of nan operating system. Unfortunately, they besides connection a powerful functionality that tin beryllium abused erstwhile successful nan hands of malicious threat actors.
Adding EDR killers to RaaS offerings
RaaS programs often don’t supply affiliates only pinch encryptors – further devices and playbooks whitethorn beryllium portion of nan package. For instance, LockBit offered Stealbit, a civilization information exfiltration tool, to its affiliates, and nan Conti leaks and Dispossessor leak disclosed that playbooks, scripts, and know-how are besides portion of nan ransomware gangs’ arsenal.
Adding an EDR slayer to a RaaS offering seems logical, and RansomHub is not nan only pack doing that. In October 2024, ESET researchers documented that nan emerging ransomware pack Embargo implemented its ain EDR slayer arsenic well, called MS4Killer, by modifying a publicly disposable PoC. At nan clip of writing: while nan group listed only 14 victims connected its DLS, it had already invested clip and resources into processing its ain EDR killer.
It remains to beryllium seen whether EDR killers find their spot successful much gangs’ offerings. However, this blogpost has besides demonstrated that researchers whitethorn leverage their usage to cluster affiliates and observe caller relationships betwixt rival gangs.
Defeating EDR killers
Defending against EDR killers is challenging. Threat actors request admin privileges to deploy an EDR killer, truthful ideally, their beingness should beryllium detected and mitigated earlier they scope that point.
While preventing nan slayer codification from executing is nan champion approach, codification obfuscation tin make this unreliable. However, focusing connected susceptible drivers provides further defense options. ESET considers drivers exploited by EDR killers perchance unsafe. Therefore, users, particularly successful firm environments, should guarantee that nan discovery of perchance unsafe applications is enabled. This tin forestall nan installation of susceptible drivers.
Although not common, blase threat actors whitethorn utilization a susceptible driver already coming connected a compromised instrumentality alternatively of relying connected BYOVD. To antagonistic this, having due spot guidance successful spot is an effective and basal defense strategy.
Conclusion
The ransomware ecosystem suffered important blows successful 2024. Despite nan wide number of recorded attacks increasing, it should not overshadow nan affirmative effect of successfully disrupting aliases eliminating 2 ransomware gangs that had been dominating nan segment for years.
We tin estimate astir really overmuch nan consequence of rule enforcement actions decreased ransomware payments, aliases really nan increasing consciousness and initiatives for illustration nan Counter Ransomware Initiative are helping ransomware victims understand that paying nan ransom whitethorn not beryllium nan champion measurement forward.
What is clear, unfortunately, is that a caller blase ransomware group, RansomHub, emerged, utilized nan correct strategies to pull affiliates (many of whom we judge transitioned from BlackCat and LockBit) successful a short period, and was quickly capable to climb to nan apical of nan ladder. In nan foreseeable future, RansomHub will surely effort to stay among nan astir progressive RaaS gangs.
Law-enforcement-led disruptions of RaaS operators person proved effective, sowing distrust successful nan RaaS ecosystem. Unfortunately, 2024 showed that affiliates are capable to regroup reasonably quickly. After all, they person beardown financial incentives to deploy encryptors to and exfiltrate delicate information from their targets. Although much difficult to execute than disruptions, eliminating nan astir progressive affiliates from nan image is besides effective because it tin forestall caller RaaS operators from gaining spot arsenic quickly arsenic RansomHub did. We judge that focusing connected nan affiliates, particularly by search down their links betwixt various gangs – arsenic demonstrated successful this blogpost betwixt RansomHub, Play, Medusa, and BianLian – will yet lead to recognition of nan affiliates and their removal from nan game.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss and samples tin beryllium recovered successful our GitHub repository.
Files
SHA-1
Filename
Detection
Description
97E13515263002809505DC913B04B49AEB78B067
amd64.exe
WinGo/Kryptik.CV
RansomHub encryptor.
BF84712C5314DF2AA851B8D4356EA51A9AD50257
Loader.exe
Win64/Agent.DVP
EDRKillShifter.
87D0F168F049BEFE455D5B702852FFB7852E7DF6
amd64.exe
WinGo/Kryptik.CV
RansomHub encryptor.
2E89CF3267C8724002C3C89BE90874A22812EFC6
Magic.exe
Win64/Agent.DVP
EDRKillShifter.
3B035DA6C69F9B05868FFE55D7A267D098C6F290
TDSSKiller.exe
Win32/RiskWare.TDSSKiller.A
TDSSKiller.
5ECAFF68D36EC10337428267D05CD3CB632C0444
svchost.exe
WinGo/HackTool.Agent.EY
Rclone.
DCF711141D6033DF4C9149930B0E1078C3B6D156
anydes.ps1
PowerShell/Agent.AEK
Script that deploys and password protects AnyDesk.
E38082AE727AEAEF4F241A1920150FDF6F149106
netscan.exe
Win64/NetTool.SoftPerfectNetscan.A
SoftPerfect Network Scanner.
046583DEB4B418A6F1D8DED8BED9886B7088F338
conhost.dll
Win64/Coroxy.J
SystemBC.
3B4AEDAFA9930C19EA889723861BF95253B0ED80
win64_1.exe
Win64/Agent.RA
BianLian backdoor.
460D7CB14FCED78C701E7668C168CF07BCE94BA1
WKTools.exe
Win32/WKTools.A
WKTools.
5AF059C44D6AC8EF92AA458C5ED77F68510F92CD
pfw.exe
Win64/Agent.RA
BianLian backdoor.
67D17CA90880B448D5C3B40F69CEC04D3649F170
1721894530.sys
Win64/RentDrv.A
Vulnerable driver utilized by EDRKillShifter.
77DAF77D9D2A08CC22981C004689B870F74544B5
Killer.exe
Win64/Agent.DVP
EDRKillShifter.
180D770C4A55C62C09AAD1FC3412132D87AF5CF6
1.dll
Win64/Coroxy.K
SystemBC.
DD6FA8A7C1B3E009F5F17176252DE5ACABD0FB86
d.exe
Win32/Filecoder.PLAY.B
Play encryptor.
FDA5AAC0C0DB36D173B88EC9DED8D5EF1727B3E2
GT_NET.exe
MSIL/Spy.Grixba.A
Grixba.
Network
IP
Domain
Hosting provider
First seen
Details
45.32.206[.]169
N/A
Vultr Holdings, LLC
2024‑07‑25
Server hosting WKTools and EDRKillShifter.
45.32.210[.]151
N/A
The Constant Company, LLC
2024‑08‑09
SystemBC C&C server.
79.124.58[.]130
N/A
TAMATYA-MNT
2024‑08‑22
Server hosting MeshAgent.
92.243.64[.]200
N/A
EDIS GmbH - Noc Engineer
2024‑07‑25
BianLian backdoor C&C server.
130.185.75[.]198
N/A
Pars Parva System LTD
2024‑08‑20
Server hosting PuTTY.
149.154.158[.]222
N/A
EDIS GmbH - Noc Engineer
2024‑07‑25
Server hosting BianLian backdoor.
MITRE ATT&CK techniques
This array was built utilizing version 16 of nan MITRE ATT&CK framework.
Tactic
ID
Name
Description
Resource Development
T1583
Acquire Infrastructure
QuadSwitcher acquired infrastructure to big their tooling.
T1587.001
Develop Capabilities: Malware
The RansomHub, Play, Medusa, and BianLian gangs create their ain encryptors and related tooling.
T1588.001
Obtain Capabilities: Malware
The Play pack uses SystemBC, a commodity malware for sale.
T1588.002
Obtain Capabilities: Tool
Various third-party devices are regularly utilized by nan gangs’ affiliates.
T1608.001
Stage Capabilities: Upload Malware
The Play pack uploaded its ain tooling to a dedicated server to beryllium utilized during intrusions.
T1608.002
Stage Capabilities: Upload Tool
The Play pack uploaded nan third-party devices it uses to a dedicated server to beryllium utilized during intrusions.
Execution
T1059.001
Command-Line Interface: PowerShell
QuadSwitcher deployed AnyDesk utilizing a PowerShell script.
T1059.003
Command-Line Interface: Windows Command Shell
Windows Command Shell is regularly utilized by QuadSwitcher to rumor commands.
Defense Evasion
T1078
Valid Accounts
QuadSwitcher abuses extracted credentials of valid accounts to move successful nan web stealthily.
T1078.002
Valid Accounts: Domain Accounts
QuadSwitcher yet gained domain admin privileges successful immoderate of nan intrusions.
T1480
Execution Guardrails
RansomHub’s encryptor requires a password to run.
T1562.001
Impair Defenses: Disable aliases Modify Tools
EDRKillShifter’s purpose is to disable information solutions.
T1562.009
Impair Defenses: Safe Mode Boot
RansomHub’s encryptor allows rebooting to safe mode to encrypt files.
T1218
System Binary Proxy Execution
QuadSwitcher abused certutil.exe to download payloads.
Credential Access
T1110
Brute Force
QuadSwitcher attempted to brute unit credentials during nan intrusions.
Discovery
T1087
Account Discovery
In bid to elevate privileges, QuadSwitcher discovered further accounts.
T1057
Process Discovery
EDRKillShifter looks for circumstantial processes related to information solutions.
Lateral Movement
T1021.001
Remote Services: Remote Desktop Protocol
RDP was often utilized for lateral activity successful nan compromised networks.
T1021.002
Remote Services: SMB/Windows Admin Shares
RansomHub supports distant encryption of files.
Collection
T1005
Data from Local System
The BianLian pack focuses connected information exfiltration, collecting information from section drives.
T1039
Data from Network Shared Drive
The BianLian pack focuses connected information exfiltration, collecting information from web drives.
Command and Control
T1071
Application Layer Protocol
In Play intrusions, payloads are retrieved via HTTP.
T1132.002
Data Encoding: Non-Standard Encoding
SystemBC employs a civilization web protocol.
T1219
Remote Access Software
Multiple RMM devices were used, including AnyDesk and MeshAgent.
Exfiltration
T1537
Transfer Data to Cloud Account
BianLian affiliates utilized Rclone to exfiltrate information to a unreality relationship they power to debar emblematic record transfers/downloads and network-based exfiltration detection.
Impact
T1485
Data Destruction
Some information for illustration backups whitethorn beryllium permanently destroyed by ransomware gangs.
T1486
Data Encrypted for Impact
The eventual consequence of ransomware gangs’ actions is encryption of victims’ data.
T1657
Financial Theft
The ransomware gangs unit victims to salary ransom successful speech for regaining entree to their data.


 3 weeks ago
3 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·