ARTICLE AD BOX
Russian APT group Storm-2372 employs instrumentality codification phishing to bypass Multi-Factor Authentication (MFA). Targets see government, technology, finance, defense, healthcare.
Cybersecurity researchers astatine SOCRadar person discovered a caller onslaught maneuver utilized by nan notorious Russian state-backed precocious persistent threat (APT), Storm-2372. According to SOCRadar’s research, shared pinch Hackread.com, Storm-2372 tin now break into online accounts of awesome organizations without trying to conjecture passwords.
This is achieved done a method called “device codification phishing,” which helps them get astir moreover beardown information measures for illustration Multi-Factor Authentication (MFA).
Device Code Phishing takes advantage of nan measurement immoderate devices, for illustration smart TVs, link to online services. Usually, these devices springiness you a typical codification that you type into a website connected your machine aliases telephone to log successful (OAuth instrumentality authorization flow). Hackers are utilizing this aforesaid process to fool group into giving them entree to their activity accounts.
Here’s really it works
The hackers nonstop clone messages, often done email aliases text, telling group they request to usage a instrumentality codification to log in. These messages nonstop them to real-looking login pages, like nan ones from Microsoft. The victims past unknowingly type successful a codification that nan hackers person created. Once nan personification enters nan code, nan hackers tin get into their relationship without needing a password aliases triggering nan accustomed information checks. This makes it overmuch harder to spot nan onslaught arsenic nan victims don’t recognize they person been compromised until it is excessively late.
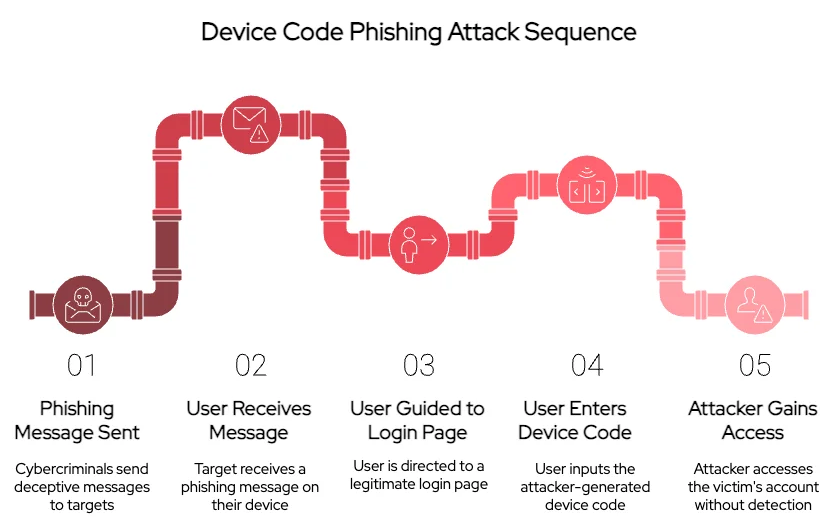 Device Code Phishing Attack Sequence (Source: SOCRadar)
Device Code Phishing Attack Sequence (Source: SOCRadar)Previously, nan method OG Device Code Phishing was utilized by hackers to create a instrumentality codification utilizing typical devices and sent it via message. However, these codes only lasted astir 15 minutes, making it difficult for hackers to log successful if nan personification didn’t spot nan message.
Storm-2372 employs nan much precocious Dynamic Device Code Phishing technique, antecedently documented by Black Hills successful 2023, to create clone websites resembling existent login pages utilizing services for illustration Azure Web Apps. When a personification visits these clone sites, they make a caller instrumentality code, allowing hackers to log in. They sometimes usage CORS-Anywhere to show nan codification correctly successful nan user’s browser. When nan personification enters nan clone code, they person entree tokens and refresh tokens, allowing hackers to entree Microsoft email for up to 3 months.
Storm-2372 is, reportedly, targeting organizations that clasp valuable accusation and make important decisions. This includes authorities agencies, exertion companies, banks, defence contractors, healthcare providers, and media companies. They’ve been seen attacking organizations successful countries for illustration nan United States, Ukraine, nan United Kingdom, Germany, Canada, and Australia.
This caller instrumentality shows that these hackers are getting amended astatine fooling group to get past moreover bully information systems, and companies request to find smarter ways to protect themselves from specified sneaky attacks.
“The run underlines nan captious request for modern organizations to clasp adaptive, context-aware defense mechanisms to antagonistic identity-based threats that are progressively evading accepted protections,” researchers concluded.

 1 week ago
1 week ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·