ARTICLE AD BOX
A caller collaborative effort by researchers Rachid Allam and Yasser Allam has exposed a captious vulnerability wrong nan Next.js framework, a wide utilized JavaScript model based connected React pinch astir 10 cardinal play downloads.
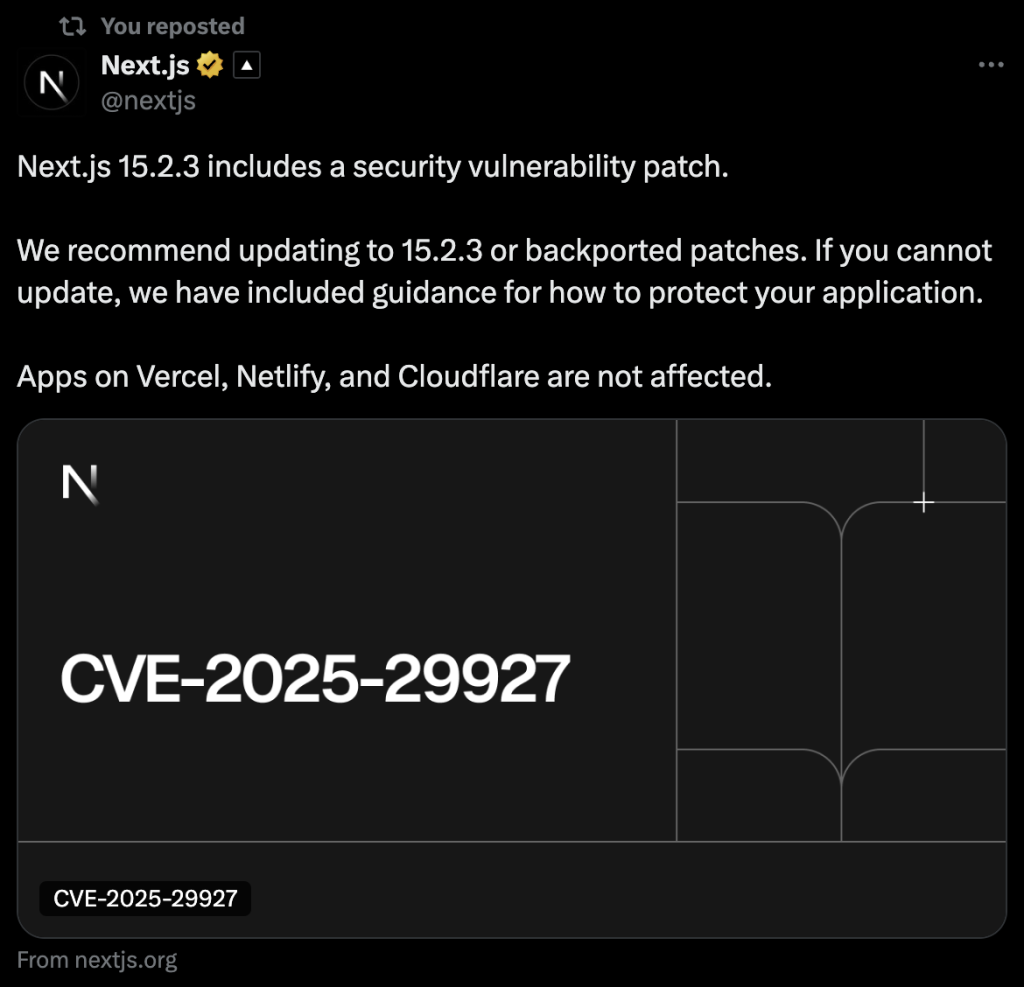
Their research, documented successful a elaborate publication, reveals a flaw successful nan Next.js middleware that allows for unauthorized entree and control, impacting each versions of nan framework. This flaw, designated CVE-2025-29927 and rated arsenic critical, allows unauthorized entree to protected resources.
Reportedly, nan vulnerability specifically targets nan middleware function, which is simply a constituent designed to execute codification earlier a petition is completed and is often utilized for important information functions, including authentication and authorization. However, nan discovered vulnerability allows attackers to bypass these information measures.
The halfway of nan vulnerability lies successful nan handling of nan “x-middleware-subrequest” header. By manipulating this header pinch a circumstantial value, attackers tin efficaciously disregard nan middleware’s intended rules, gaining unauthorized access. As Allam explained, “The header and its worth enactment arsenic a cosmopolitan cardinal allowing rules to beryllium overridden.”
The vulnerability stems from codification intended to forestall recursive requests, which could lead to infinite loops. Ironically, this very codification introduced a constituent of failure, enabling nan authorization bypass.
The worth required for this bypass is derived from nan middleware’s path, which, depending connected nan Next.js version, tin beryllium “middleware,” “src/middleware,” aliases a variety involving nan “pages” directory successful older versions.
Researchers demonstrated various exploits, including authorization/rewrite bypasses, Content Security Policy (CSP) bypasses, and moreover imaginable Denial-of-Service (DoS) attacks done cache poisoning.
“If nan tract has a cache/CDN system, it whitethorn beryllium imaginable to unit nan caching of a 404 response, rendering its pages unusable,” they noted, highlighting nan wide scope of imaginable impacts.
They initially believed that only versions 12.0.0 and 12.0.7 were affected but later identified that each versions were susceptible and duly notified nan Next.js team.
The squad promptly acknowledged nan vulnerability, issuing an advisory and providing patches for susceptible versions.
- For Next.js 15.x, this rumor is fixed successful 15.2.3.
- For Next.js 14.x, this rumor is fixed successful 14.2.25.
- For Next.js 13.x, this rumor is fixed successful 13.5.9.
- For Next.js 12.x, this rumor is fixed successful 12.3.5.
Earlier versions require workarounds, specified arsenic blocking outer requests containing nan “x-middleware-subrequest” header.
Notably, applications hosted connected Vercel aliases Netlify person been automatically protected. The framework’s maintainers person since admitted to missing “the people connected partner communications” and person committed to improving early information advisories by establishing a dedicated partner mailing list.
 Next.js station connected X (Source: zhero_web_security)
Next.js station connected X (Source: zhero_web_security)
The Next.js documentation, which antecedently highlighted middleware’s domiciled successful authentication and authorization, has since been updated to stress that it should not beryllium nan sole information measure.
Nevertheless, nan find and disclosure of CVE-2025-29927 show nan value of due information checks, particularly successful wide utilized frameworks for illustration Next.js.

 3 weeks ago
3 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·