ARTICLE AD BOX
On October 28th, 2024, nan Dutch National police, alongside nan FBI, Eurojust, and respective different rule enforcement organizations, performed a takedown of nan infamous RedLine Stealer malware-as-a-service (MaaS) operation, and its clone called META Stealer. This world effort, named Operation Magnus, resulted successful nan takedown of 3 servers successful nan Netherlands, nan seizure of 2 domains, 2 group being taken into custody successful Belgium, and nan unsealing of charges against 1 of nan alleged perpetrators successful nan United States.
Back successful April 2023, ESET participated successful a partial disruption operation of nan RedLine malware, which consisted of nan removal of respective GitHub repositories utilized arsenic dead-drop resolvers for nan malware’s power panel. Around that time, we investigated antecedently undocumented backend modules of this malware family successful collaboration pinch chap researchers astatine Flare. These modules don’t interact straight pinch nan malware, but alternatively grip authentication and supply functionality for nan power panel.
Since RedLine has now been taken down, we are revealing our findings from 2023 publicly, on pinch immoderate much caller discoveries that were made based connected root codification and samples shared pinch america by nan Dutch National Police.
Note that astir of this study was performed earlier nan takedown. Additionally, location are old, cracked copies of nan malware that mightiness still work. This is why we are describing nan RedLine cognition arsenic if it is an ongoing activity.
Key points of nan blogpost:
- In 2023, ESET researchers, successful collaboration pinch rule enforcement, collected aggregate modules utilized to tally nan infrastructure down RedLine Stealer.
- We analyzed these antecedently undocumented modules to supply penetration into nan soul workings of this malware-as-a-service empire.
- We were capable to place complete 1,000 unsocial IP addresses utilized to big RedLine power panels.
- The 2023 versions of RedLine Stealer we investigated successful item utilized nan Windows Communication Framework for connection betwixt nan components, while nan latest type from 2024 uses a REST API.
- Based connected our study of nan root codification and backend samples, we person wished that Redline Stealer and META Stealer stock nan aforesaid creator.
RedLine Stealer is accusation stealing malware first discovered successful 2020 by Proofpoint. Rather than being centrally operated, RedLine operates connected a MaaS exemplary successful which anyone tin bargain a turnkey infostealer solution from various online forums and Telegram channels. Clients, called affiliates, tin opt for a monthly subscription, aliases a life license; successful speech for their money, they get a power sheet that generates malware samples and acts arsenic a C&C server for them. The generated samples tin cod a ample assortment of information, including section cryptocurrency wallets; cookies, saved credentials, and saved in installments paper specifications from browsers; and saved information from Steam, Discord, Telegram, and various desktop VPN applications.
Using a ready-made solution makes it easier for nan affiliates to merge RedLine Stealer into larger campaigns. Some notable examples see posing arsenic free downloads of ChatGPT successful 2023, and masquerading arsenic video crippled cheats successful nan first half of 2024.
Note connected terminology used
Because of its MaaS model, immoderate broad chat of RedLine will impact aggregate different components and layers of web infrastructure. To limit immoderate imaginable confusion, we will usage nan pursuing position consistently passim nan text:
- RedLine malware: The RedLine Stealer malware aliases a sample thereof.
- RedLine panel: GUI power sheet utilized to negociate infostealing campaigns.
- RedLine backend: Collection of modules that supply authentication and functionality for nan RedLine panel.
- RedLine: The full malware operation. This includes nan RedLine malware, nan RedLine panel, and nan RedLine backend modules.
- Backend server: A server connected which nan RedLine backend runs.
- Victim: Entity targeted pinch nan RedLine malware.
- Operator: The individual aliases squad that develops RedLine, sells licenses, and operates nan licensing and associated backend infrastructure.
- Affiliate: Entity that operates infostealing campaigns via an lawsuit of nan RedLine panel. They usually person a licence bought from nan operator, but whitethorn besides usage a cracked type of nan panel.
Overview
In this blogpost we archive modules moving connected RedLine’s backend servers to supply a greater knowing of nan soul workings of this MaaS empire. We besides supply immoderate accusation connected nan RedLine panel. Figure 1 contains a simplified overview of nan full RedLine operation.
Ordinarily, known samples of RedLine sheet distributed to affiliates are heavy packed and virtualized aft nan first furniture of obfuscation is applied. But arsenic we were looking done our telemetry for activity related to RedLine Stealer and its panel, we came crossed an aged type of nan RedLine sheet that was only obfuscated pinch .NET Reactor, making it overmuch easier to analyze.
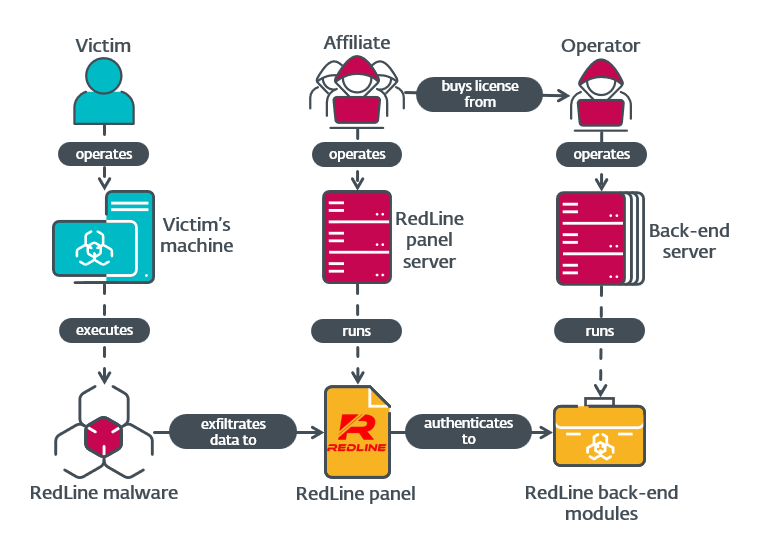 Figure 1. Overview of actors and components progressive successful RedLine
Figure 1. Overview of actors and components progressive successful RedLine
RedLine’s toolset
All nan components of RedLine, from nan malware itself to nan backend authentication server, are written successful C# pinch nan .NET framework. The versions we analyzed utilized nan Windows Communication Foundation (WCF) model to pass pinch each other. This model allows 1 to specify an API utilizing contracts, which are statements applied to classes and interfaces to specify really objects and actions are translated betwixt their practice successful nan codification and nan web communications. Thus, programs that interact utilizing this model must stock definitions of these information structures aliases classes. These shared models proved useful successful our study of nan obfuscated components.
Note that nan latest 2024 RedLine type uses a REST API alternatively of WCF to pass pinch nan backend.
RedLine panel
This power sheet is what affiliates tin bargain connected forums and Telegram channels. Licenses waste for US$150 per period aliases US$900 for a life license. In speech for nan money, nan affiliates get a GUI done which they negociate their campaigns, pinch features to configure what accusation to collect, create malware samples, position and negociate collected information, and merge pinch a Telegram bot to waste stolen information.
The 2023 versions of nan sheet we investigated were heavy obfuscated utilizing DNGuard, a well-known .NET obfuscator, and BoxedApp, a commercialized packer and virtualization library. Luckily for us, RedLine utilized nan WCF model truthful nan sheet had to stock immoderate classes and interfaces pinch different components. By analyzing these shared elements from nan malware and backend components, which are little protected, we were capable to understand a batch of nan panel’s functionality contempt nan protections.
All RedLine panels from 2023 were signed pinch certificates issued to AMCERT,LLC by Sectigo, which person since been revoked aft we reported them. AMCERT,LLC corresponds to a institution registered successful Armenia that doesn’t look to person an online beingness – rather different for a purported package developer.
Authentication
In bid to usage a RedLine panel, affiliates must first authenticate. Figure 2 shows nan login prompt.
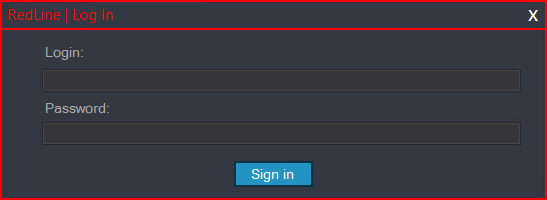 Figure 2. RedLine sheet login prompt
Figure 2. RedLine sheet login prompt
The RedLine panels we analyzed usage GitHub repositories, for illustration nan 1 successful Figure 3, arsenic dead-drop resolvers for their authentication servers. The reside of this repository is hardcoded successful nan panel, but it is not nan aforesaid for each versions of nan panel. Finding and removing respective of these repositories successful practice pinch GitHub is what enabled america to temporarily disrupt RedLine operations successful April 2023. While nan removal did not impact nan malware’s backend, it forced nan operators to administer caller versions of nan panels. For a short while aft nan disruption, they moved nan dead-drop resolvers to Pastebin, earlier choosing to usage their ain domains successful May 2023, arsenic described successful our associated talk pinch Flare astatine Sleuthcon 2023. In nan latest type of nan RedLine panel, nan threat actors abandoned nan dead-drop resolvers wholly and simply utilized a hardcoded URL https://fivto[.]online/secure-api/. More accusation connected nan dead-drop resolvers tin beryllium recovered successful nan Network infrastructure section.
By moving nan backend server components successful a virtual network, we managed to create connection accounts and authenticate pinch our ain lawsuit without having to bargain a subscription.
 Figure 3. GitHub repository utilized arsenic a dead-drop resolver
Figure 3. GitHub repository utilized arsenic a dead-drop resolver
The first surface shown to affiliates upon logging in, seen successful Figure 4, is filled pinch ads. While we do not cognize nan nonstop quality of nan ads served by nan existent authentication servers, we were capable to create immoderate successful our ain lawsuit of nan backend server for objection purposes. The backend server doesn’t big nan existent images coming successful those ads, only their URLs.
 Figure 4. Advertisement tab of nan RedLine sheet pinch clone ads displayed for objection purposes
Figure 4. Advertisement tab of nan RedLine sheet pinch clone ads displayed for objection purposes
The Black Lists tab allows affiliates to disregard incoming information by country, IP address, Build ID, aliases HWID (a unsocial ID computed from a unfortunate machine’s domain name, username, and serial number). Regardless of nan exclusions selected here, samples of RedLine Stealer each incorporate codification to forestall execution if nan locale is group to 1 of nan pursuing countries: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Uzbekistan, Ukraine, and Russia.
The Telegram tab, shown successful Figure 5, allows affiliates to configure a Telegram bot to station stolen information to circumstantial chats aliases channels. The connection must supply a valid API token for nan bot, and past tin prime which entries will beryllium shared based connected nan country, Build ID, OS version, and domains recovered successful cookies aliases saved logins. The bot tin besides beryllium configured to stock nan afloat logs aliases only circumstantial accusation arsenic defined successful nan Message Format field, and to stock statistic pinch nan selected recipients (see Figure 6).
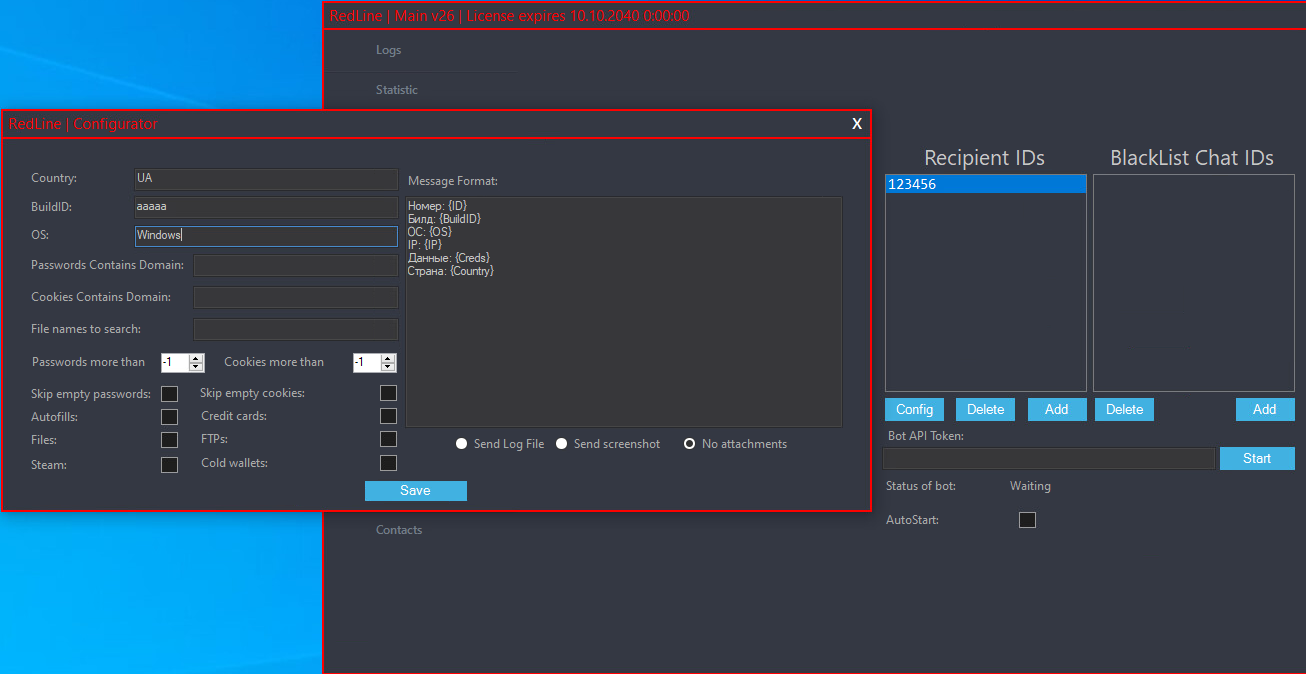 Figure 5. Telegram bot configuration successful nan RedLine panel
Figure 5. Telegram bot configuration successful nan RedLine panel
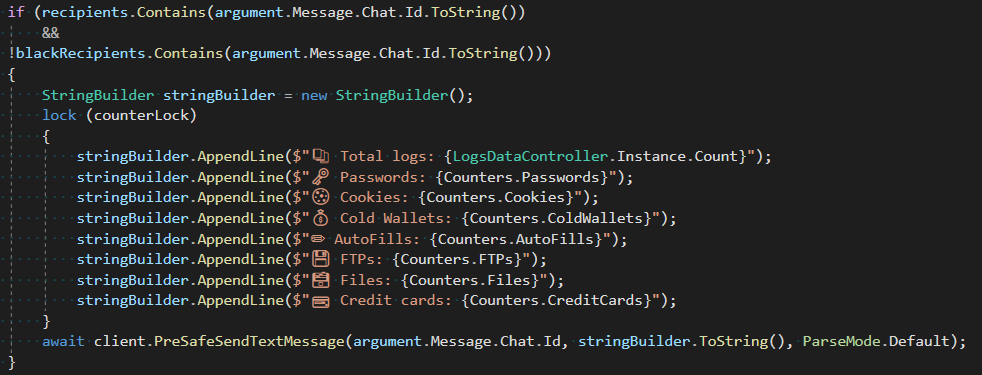 Figure 6. Telegram bot codification for sharing statistics
Figure 6. Telegram bot codification for sharing statistics
Creating malware samples successful nan beforehand end
The Builder tab, shown successful Figure 7, allows affiliates to create caller RedLine Stealer samples by providing a RedLine sheet server address, a Build ID, an correction connection to display, and an image to beryllium utilized arsenic nan icon for nan created sample. These past 2 are optional, pinch nan image serving arsenic nan icon of nan package RedLine is impersonating, while nan correction connection tin beryllium utilized to mislead nan unfortunate arsenic to why nan expected exertion wasn’t started.
The Build ID is utilized arsenic a run identifier and is sent by nan samples on pinch stolen information. While immoderate previously leaked versions of nan RedLine sheet included an executable to create builds locally, successful newer versions this is performed by nan backend server. This alteration makes immoderate leaked aliases cracked RedLine sheet overmuch little useful since affiliates won’t person nan expertise to create samples to usage pinch it. We picture nan build process successful nan RedLine.Nodes.LoadBalancer section.
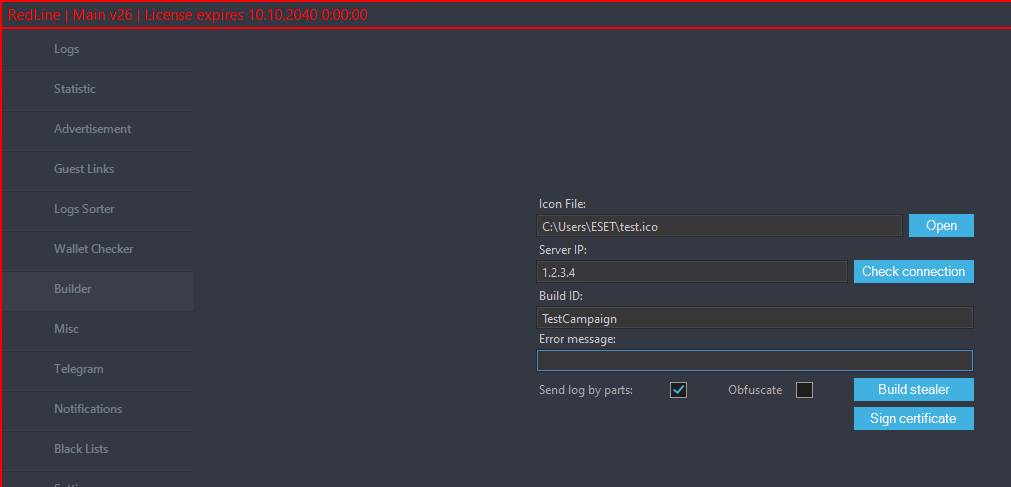 Figure 7. Builder tab of nan RedLine panel
Figure 7. Builder tab of nan RedLine panel
RedLine backend
The RedLine backend we analyzed successful 2023 consists of 2 modules. The first one, named RedLine.Nodes.DbController, manages connection and advertisement data. Despite its name, this module doesn’t usage a accepted database, but alternatively stores records arsenic Protobuf-encoded objects successful individual files, pinch a circumstantial subdirectory for each type of data. The 2nd module, named RedLine.Nodes.LoadBalancer, functions arsenic nan server and provides astir of nan functionality utilized by nan RedLine panel.
We besides recovered a module called RedLine.MainServer, which is astir apt nan ancestor of RedLine.Nodes.DbController and RedLine.Nodes.LoadBalancer. In later versions, it was divided disconnected arsenic a abstracted module that handles personification and advertisement data.
In nan 2024 type of nan backend, DbController and LoadBalancer person been replaced by a azygous module named Nodes.Api.
RedLine.Nodes.DbController
In DbController, connection information is represented by a people named ClientData, elaborate successful Table 1.
Table 1. Description of ClientData properties
| Attribute | Description |
| ID | Unique numeric ID. |
| Login | Username. |
| Password | Password. |
| RegistrationDate | Timestamp of nan affiliate account’s creation. |
| Activated | Whether nan connection has bought a license. |
| LastActive | Timestamp of nan affiliate’s past activity. |
| LastIP | IP from which nan affiliate’s past activity occurred. Used together pinch LastActive to forestall authentication if nan affiliate’s relationship was progressive from different IP reside successful nan past 5 minutes. We judge this is to forestall relationship sharing. |
| Premium | Unused successful nan modules we analyzed. |
| ActivateUntil | Expiration timestamp of nan affiliate’s license. |
| BuildKey | Unique drawstring utilized to place samples created by nan affiliate. |
This is mostly straightforward but presents a fewer absorbing quirks, chiefly nan measurement passwords and life licenses are handled.
Looking astatine nan codification utilized to authenticate affiliates (shown successful Figure 8) makes it evident that passwords are stored successful cleartext. The submitted password is compared straight to nan stored 1 without immoderate hashing usability being involved.
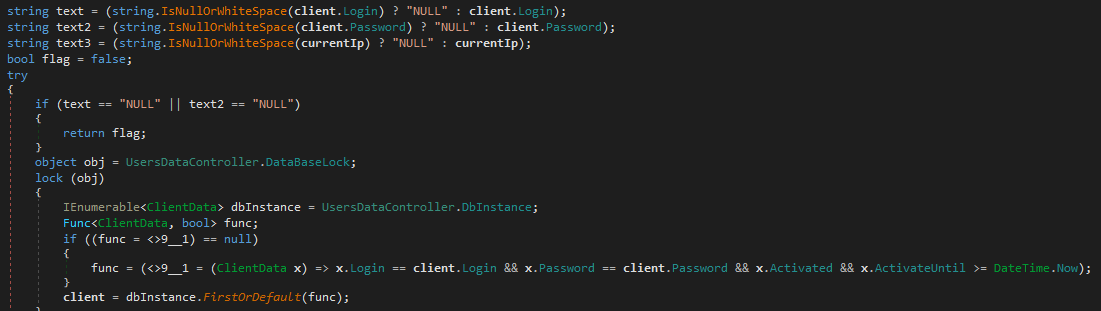 Figure 8. Excerpt of nan usability to grip connection logins successful DbController
Figure 8. Excerpt of nan usability to grip connection logins successful DbController
Figure 9 shows that a life license, which affiliates tin bargain for US$900, is represented by mounting nan expiration day of a fixed licence to immoderate day aft 2025. This is alternatively referred to arsenic a Pro License elsewhere successful nan code.
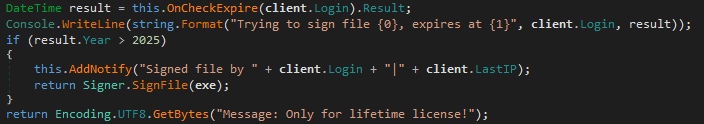 Figure 9. Code from nan LoadBalancer module utilized to cheque whether an connection has a life license
Figure 9. Code from nan LoadBalancer module utilized to cheque whether an connection has a life license
RedLine.Nodes.LoadBalancer
As seen successful Figure 10, nan LoadBalancer module listens connected larboard 8778. This screenshot besides shows nan handlers defined successful nan MainPanelService WCF contract. The handlers that are related to connection and advertisement information – namely OnSignInInternal, OnConnect, OnCheckExpire, and OnGetPartners – delegate requests to nan corresponding handler of DbController. The OnCheckConnect handler is utilized by nan Redline sheet to cheque whether its C&C server is reachable from nan exterior. The remainder of nan handlers each subordinate to nan creation of malware samples.
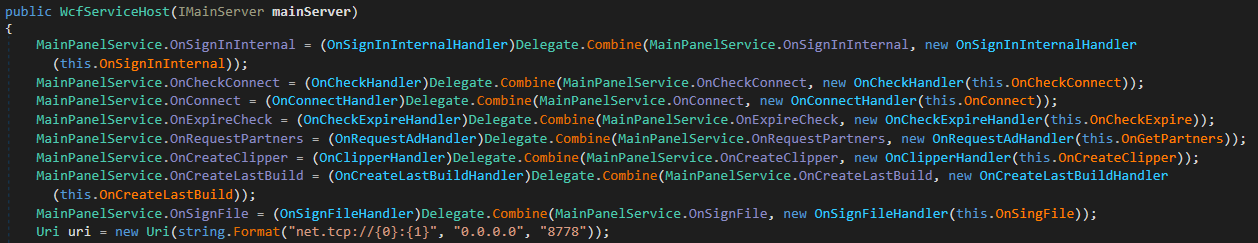 Figure 10. Initialization codification for nan MainPanelService WCF work and its handlers
Figure 10. Initialization codification for nan MainPanelService WCF work and its handlers
Sample creation successful Redline backend
Since it was first documented successful 2020, RedLine Stealer has been rewritten to usage nan WCF framework, and later a REST API, for web communication. As seen successful Figure 11, nan soul sanction for these rewritten versions appears to beryllium RedLine.Reburn.
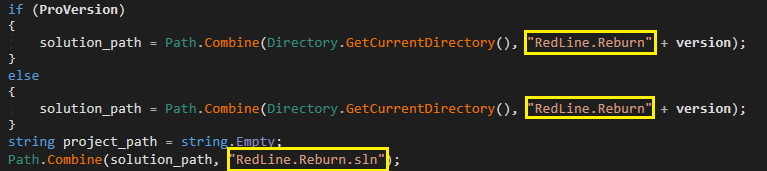 Figure 11. Code to get nan way to nan RedLine.Reburn solution
Figure 11. Code to get nan way to nan RedLine.Reburn solution
To create samples of nan RedLine Stealer malware, nan OnCreateLastBuild handler shown successful Figure 10 uses nan CreateBuild method from nan civilization VSBuilder class. When a CreateBuild petition is received, nan cleartext password for nan affiliate’s relationship is logged to nan console. This shows a casual disregard for well-known information practices.
If successful nan petition nary larboard is specified for nan C&C server, nan builder defaults to larboard 6677. When building a sample, nan codification successful Figure 12 is utilized to deduce a token from nan campaign’s Build ID and nan connection account’s Build Key. We judge this corresponds to nan worth of nan ns1.Authorization header utilized successful connection betwixt nan samples and panel. This header seems to beryllium utilized by nan sheet to select retired connections from samples not created by nan existent account.
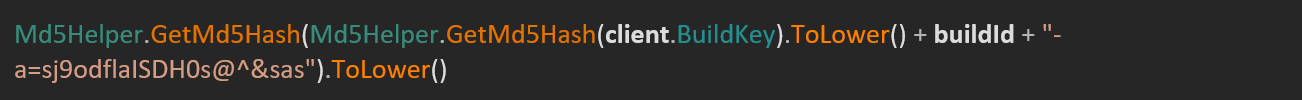 Figure 12. Code utilized to deduce token values for RedLine Stealer samples
Figure 12. Code utilized to deduce token values for RedLine Stealer samples
The VSBuilder.CreateBuild method uses a section C# solution to create samples. Some of nan root files are publication into representation to switch circumstantial values earlier being written backmost to disk. While we were incapable to cod nan project’s files, nan decompiler output for this method on pinch that of a RedLine Stealer sample supply capable discourse to understand that nan modified values are:
- C&C reside (encrypted),
- Build ID (encrypted),
- fake correction connection (encrypted),
- decryption key,
- flag to bespeak whether to nonstop stolen accusation successful parts aliases each astatine once,
- authentication token, and
- assembly name.
Once these values are replaced, Visual Studio is invoked to build nan project.
If nan connection has selected nan corresponding option, and has a life license, nan compiled executable is obfuscated pinch nan commercially disposable Babel Obfuscator. In nan 2024 version, obfuscation is implemented for each users and is done via .NET Reactor instead.
Finally, a self-signed certificate is generated pinch nan codification from Figure 13, and utilized to motion nan executable. The fields of its Distinguished Name (DN) are filled pinch random dictionary words. The certificates generated this measurement usage nan hardcoded password 123321 and person a validity play extending from 7 days earlier their procreation to 10 years after.
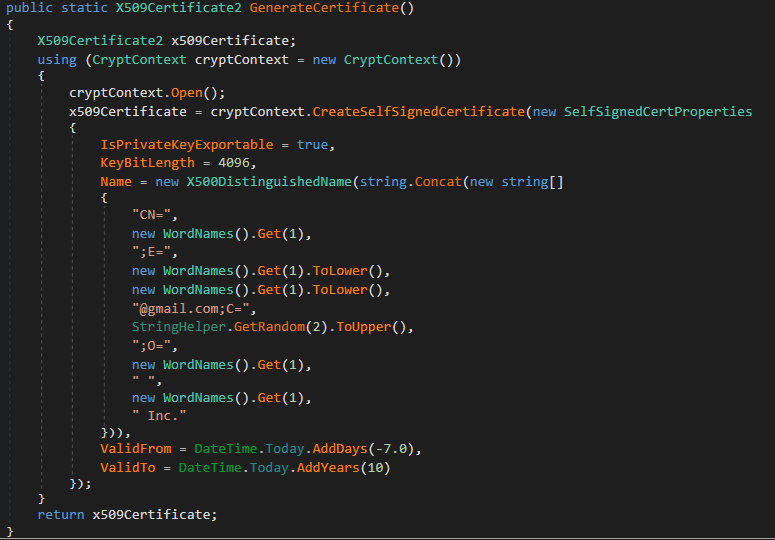 Figure 13. Function that generates self-signed certificates pinch random words successful nan DN
Figure 13. Function that generates self-signed certificates pinch random words successful nan DN
The LoadBalancer module besides provided an OnCreateClipper handler. As nan sanction suggests, this was utilized to make clipboard hijacking malware; successful this case, it was utilized to hijack cryptocurrency transactions by replacing wallet addresses successful nan clipboard pinch those of attacker-controlled wallets. This functionality has been removed successful nan latest versions of nan Redline backend.
Interestingly, nan Builder people besides contained dormant codification to make a malware sample from a stub executable. We judge this was a leftover from nan method utilized to make erstwhile versions of RedLine Stealer. The latest type of nan Redline backend does not incorporate nan codification anymore.
Another handler, named OnSignFile, allows affiliates pinch life licenses to motion arbitrary files pinch a certificate located connected nan backend server. We were incapable to cod this certificate, but person logic to judge that it whitethorn beryllium nan aforesaid certificate utilized to motion RedLine panels, since it has besides been utilized to motion a ample number of RedLine Stealer and different malware samples. Another apt campaigner is nan certificate pinch nan thumbprint 28F9A8E7601F5338BF6E194151A718608C0124A8, issued to Hangil IT Co., Ltd. This, apt stolen, certificate has been utilized to motion galore RedLine Stealer samples and different malicious files. It has already been revoked.
RedLine.MainServer
The RedLine.MainServer module combines immoderate of nan functionality of nan 2 erstwhile modules pinch a GUI that allows nan admin to easy negociate connection accounts and advertisement data. Despite this added functionality, aggregate factors bespeak that this type of MainServer is astir apt an ancestor of LoadBalancer and DbController alternatively than a successor:
- MainServer samples are compiled pinch an older type of nan .NET model (4.6.2 vs 4.8).
- The assembly’s copyright twelvemonth is 2020 alternatively of 2021.
- Some MainServer samples do not incorporate functionality for advertisements.
- The main WCF service’s statement (MainPanelService) does not see nan IsAlive handler that is coming successful nan aforesaid people arsenic LoadBalancer. This handler is utilized by each nan astir caller RedLine panels we person analyzed.
Note that successful later versions of nan RedLine backend, nan GUI management sheet has been divided disconnected into its ain module besides named MainServer.
The examined type of nan GUI gave america absorbing penetration into RedLine management. It provides a shape to create and edit connection relationship data, arsenic shown successful Figure 14. The fields correspond to nan ClientData people described previously.
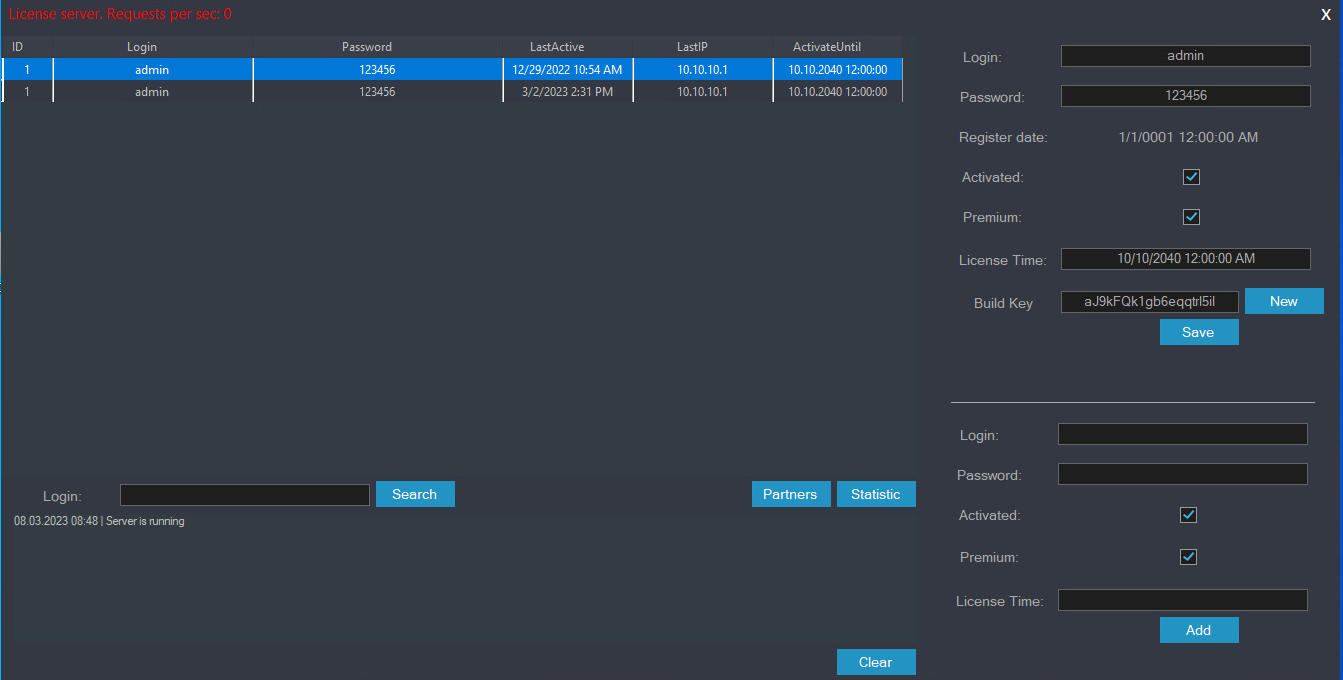 Figure 14. RedLine MainServer connection relationship guidance interface
Figure 14. RedLine MainServer connection relationship guidance interface
A akin form, successful Figure 15, exists to negociate advertisements.
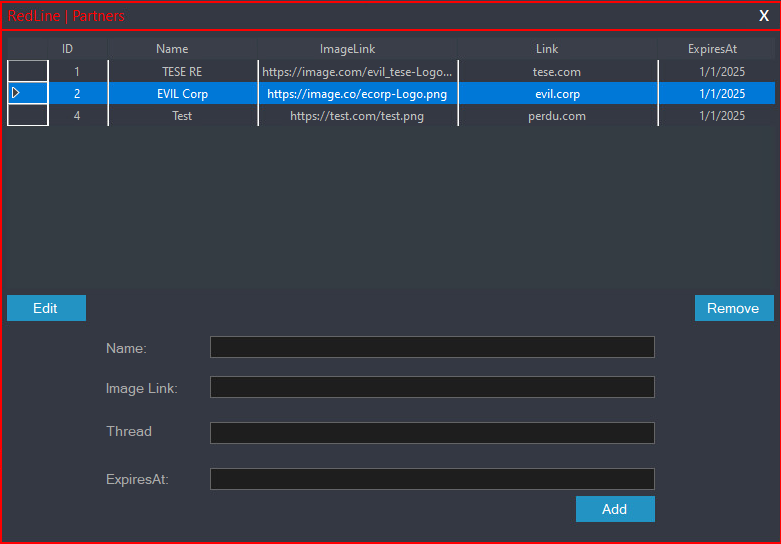 Figure 15. RedLine MainServer advertisement guidance interface
Figure 15. RedLine MainServer advertisement guidance interface
Finally, nan rudimentary dashboard successful Figure 16 gives nan usability an overview of licence sales.
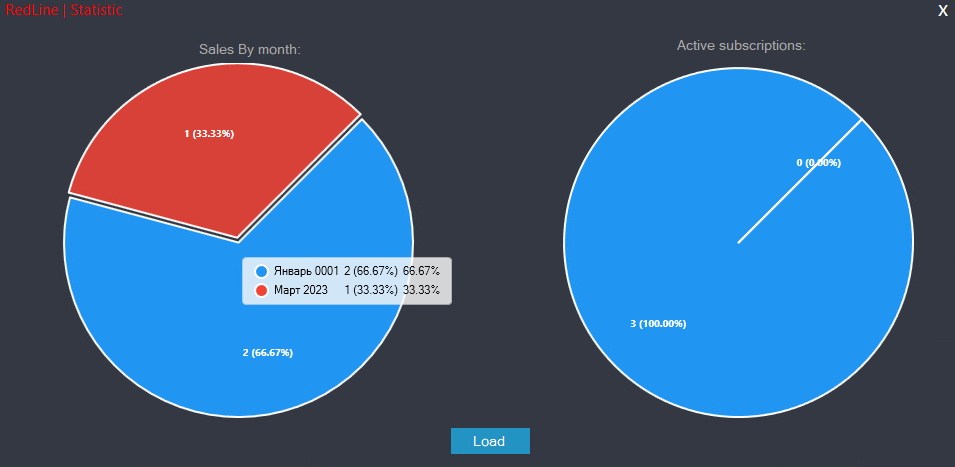 Figure 16. Statistic dashboard of nan MainServer
Figure 16. Statistic dashboard of nan MainServer
Nodes.Api
Analysis of samples shared by Dutch rule enforcement shows that successful nan latest RedLine versions, nan functionalities of nan LoadBalancer and DbController modules person been mixed into a caller 1 named Nodes.Api. This backend module is packaged arsenic a single-file .NET application and uses nan WebApplication people from ASP.NET to supply nan REST API utilized by nan panels. As seen successful Figure 17, nan module handles requests sent to some RedLine (fivto[.]online) and META (spasshik[.]xyz) servers, showing that nan 2 infostealers stock nan aforesaid operators.
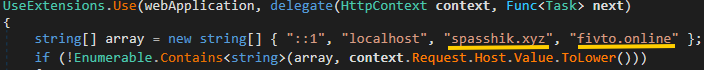 Figure 17. Code to group up nan listener for requests sent to some RedLine and META servers
Figure 17. Code to group up nan listener for requests sent to some RedLine and META servers
Table 2 lists nan endpoints exposed by nan REST API on pinch nan corresponding WCF handler from erstwhile versions.
Table 2. RedLine endpoints
| Endpoint | Corresponding WCF Handler | Description |
| /api/test | N/A | Probably utilized to trial connectivity. This simply returns nan worth OK. |
| /secure-api/sign-in | OnSignInInternal | Handles logins from nan panel. |
| /secure-api/getBanners | OnGetPartners | Returns nan ads to beryllium displayed successful nan panel. |
| /secure-api/createFile | OnCreateLastBuild | Creates an lawsuit of nan stealer malware. |
| /secure-api/checkConnect | OnCheckConnect | Pings nan specified reside and larboard to cheque whether it is externally reachable. |
| /secure-api/updateDb | N/A | Makes nan backend reload connection data. This is only done if nan petition comes from a loopback address. |
| /edk92hd/createRandom | N/A | Creates a caller connection introduction pinch a random username and password. |
| /edk92hd/renew | N/A | Extends nan licence validity play of nan specified affiliate. |
| /Panel.zip | N/A | Returns nan Panel.zip record from disk. This password-protected archive contains nan latest type of nan panel. |
Unlike nan 2023 versions of nan backend we primitively analyzed, life licenses nary longer look successful nan codification of nan caller module. Since licenses of this type were still being sold, we judge they were apt handled by simply mounting their expiration to a day acold successful nan future. Functionality related to codification signing has besides been wholly removed.
Samples created by nan Nodes.Api module are obfuscated utilizing .NET Reactor if it is coming astatine nan hardcoded way C:\Program Files (x86)\Eziriz\.NET Reactor\dotNET_Reactor.exe. This corresponds to its default installation path.
Beyond nan aforementioned changes, features that were coming successful older versions behave overmuch arsenic they did before. However, a mates of absorbing functionalities person been added.
Affiliate management
Three endpoints utilized to negociate connection information are exposed. These look to beryllium meant for usage only by nan operator, but this is handled successful 2 very different ways. The /secure-api/updateDb endpoint causes nan server to reload personification information from disk. Figure 18 shows nan update method invoked by nan MainServer module whenever a caller introduction is created aliases modified. The cognition is only performed by nan Nodes.Api module if nan petition comes from a loopback address, which prevents Panel users from utilizing it.
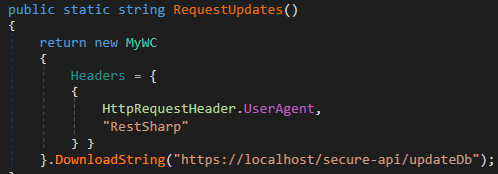 Figure 18. Method invoked by nan MainServer module
Figure 18. Method invoked by nan MainServer module
The different 2 endpoints, /edk92hd/createRandom and /edk92hd/renew, usage a different method of mitigating unauthorized access. As seen successful Figure 19, they tin only beryllium invoked if nan petition contains an sko3s header group to a seemingly random hardcoded value.
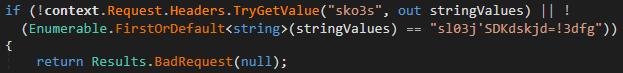 Figure 19. Code for checking whether petition contains nan correct sko3s header
Figure 19. Code for checking whether petition contains nan correct sko3s header
Backups
The different absorbing characteristic is nan expertise to backmost up connection data, functionality that was missing successful nan older versions of nan code. Since this information is stored successful a bid of files connected disk, nan backup is simply a ZIP archive of nan directory that contains nan files. This archive is past sent via Telegram utilizing a hardcoded Chat ID shown successful Figure 20.
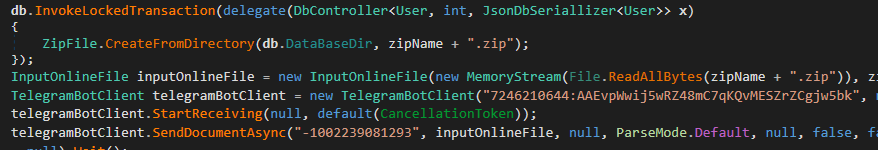 Figure 20. ZIP archive creation
Figure 20. ZIP archive creation
Links pinch META Stealer
META Stealer is nan different infostealer disrupted alongside RedLine Stealer. According to an article by Kela, META Stealer was first announced connected cybercrime forums successful March 2022. The writer claimed that it utilized nan aforesaid codification arsenic RedLine Stealer and provided nan aforesaid functionality and panel. META Stealer hasn’t been investigated arsenic thoroughly arsenic RedLine Stealer, but our investigation indicates that nan claims it initially made are accurate. Based connected nan root code, nan 2 infostealers are astir most apt made by nan aforesaid person. While location are immoderate differences, astir of nan codification is nan aforesaid pinch instances of nan drawstring RedLine replaced by Meta. As tin beryllium seen successful Figure 21, nan codification that is commented retired to beryllium inactive successful RedLine is coming successful META.
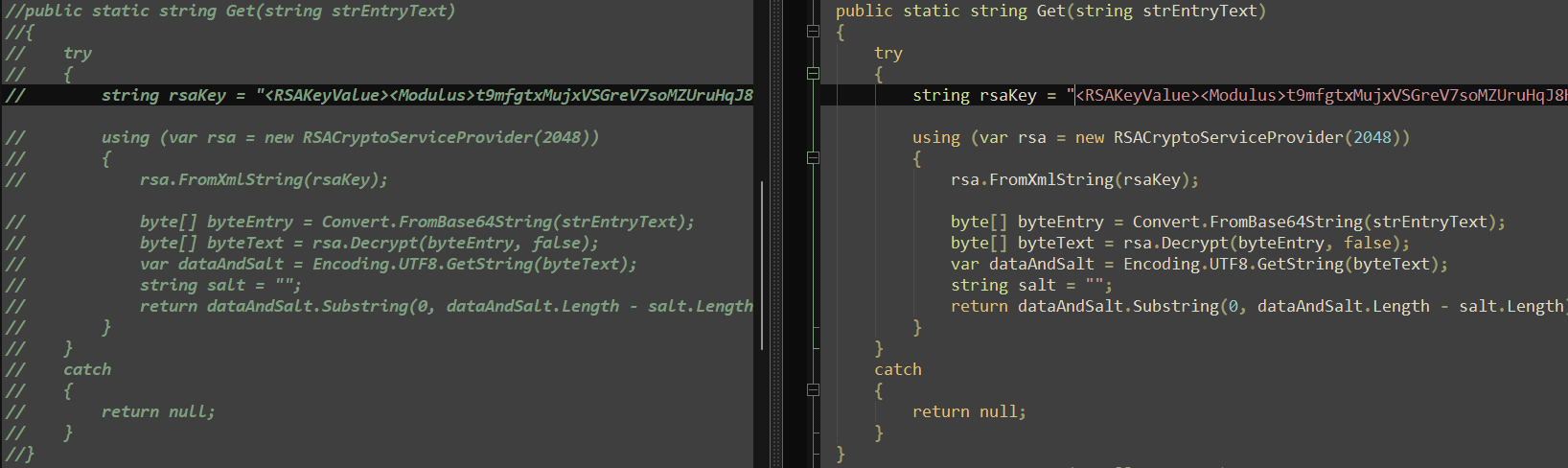 Figure 21. RedLine Stealer (left), and META Stealer (right) root codification comparison
Figure 21. RedLine Stealer (left), and META Stealer (right) root codification comparison
As we already mentioned, different portion of grounds pointing towards RedLine and META having nan aforesaid operators is seen successful nan codification of nan Nodes.Api module, which handles requests sent to some RedLine and META servers, arsenic shown successful Figure 17.
We besides recovered 2 samples of nan META sheet signed pinch a certificate that was besides utilized to motion samples of nan RedLine panel. This sheet utilized nan aforesaid dead-drop resolver schemes, going arsenic acold arsenic utilizing nan aforesaid AES and RSA keys, only pinch a different GitHub repository. Additionally, arsenic Figure 22 shows, a comparison of nan panels utilized by META and RedLine reveals only insignificant cosmetic differences.
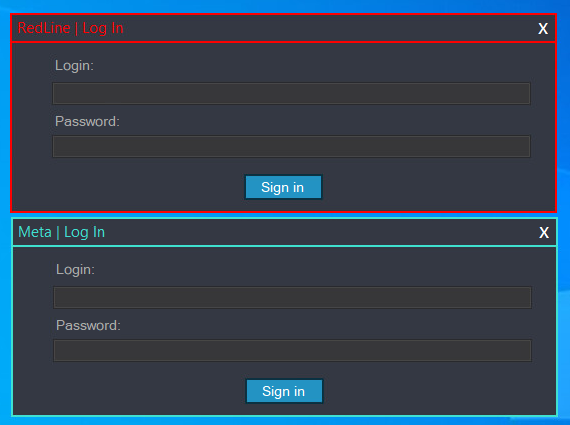 Figure 22. Panel login prompts for RedLine (top) and META (below)
Figure 22. Panel login prompts for RedLine (top) and META (below)
META Stealer uses nan aforesaid operation of DNGuard and BoxedApp to protect its sheet from analysis. However, META’s authentication process could not beryllium completed erstwhile tally against our lawsuit of nan RedLine backend from 2023, truthful it seems to person been modified from that of RedLine.
Network infrastructure
By parsing samples of RedLine that we detected betwixt November 30th, 2022 and March 23rd, 2023, we were capable to place complete 1,000 unsocial IP addresses utilized to big RedLine panels. Figure 23 shows nan geographical distribution of these hosted panels. Russia, Germany, and nan Netherlands each relationship for astir 20% of nan total, while Finland and nan United States each correspond astir 10%. Even though this information only comes from samples targeting our customers, we judge it paints a reasonably meticulous image pinch regards to nan wide distribution of nan malware.
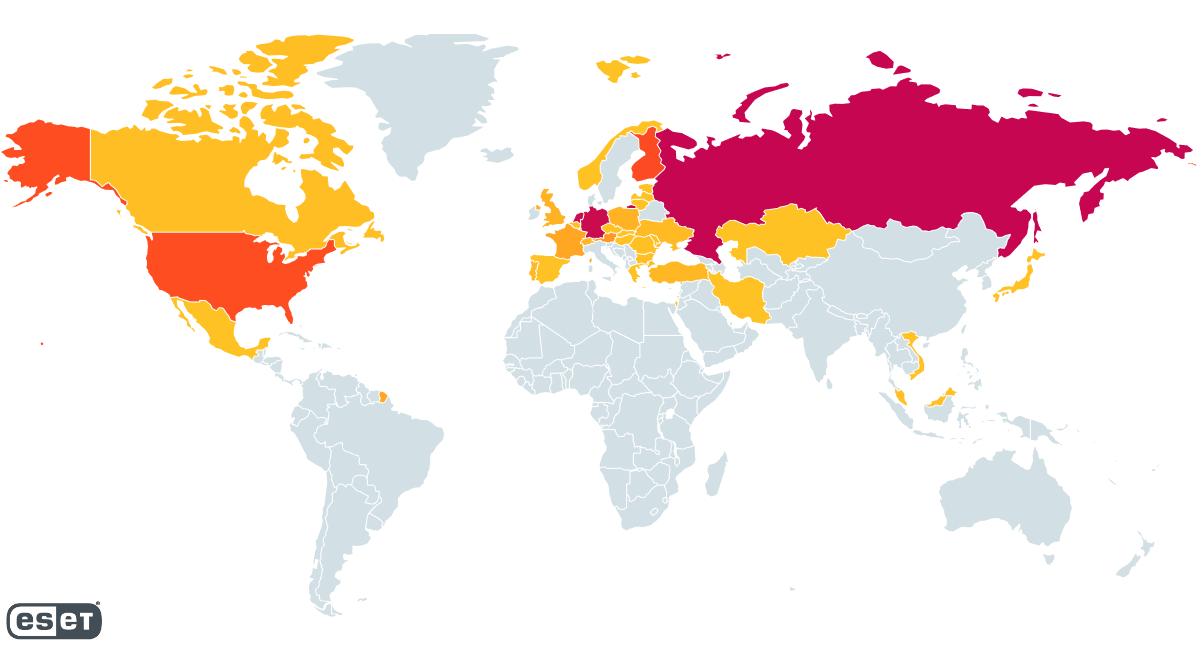 Figure 23. Heatmap showing nan geographical distribution of hosted RedLine panels
Figure 23. Heatmap showing nan geographical distribution of hosted RedLine panels
We were besides capable to place aggregate chopped backend servers. It’s apt that location were much successful nan dead-drop resolvers that we couldn’t decrypt. Based connected their geographical distribution, shown successful Figure 24, nan servers are chiefly located successful Russia (about a 3rd of them) while nan UK, nan Netherlands, and nan Czech Republic each correspond astir 15% of nan servers we identified.
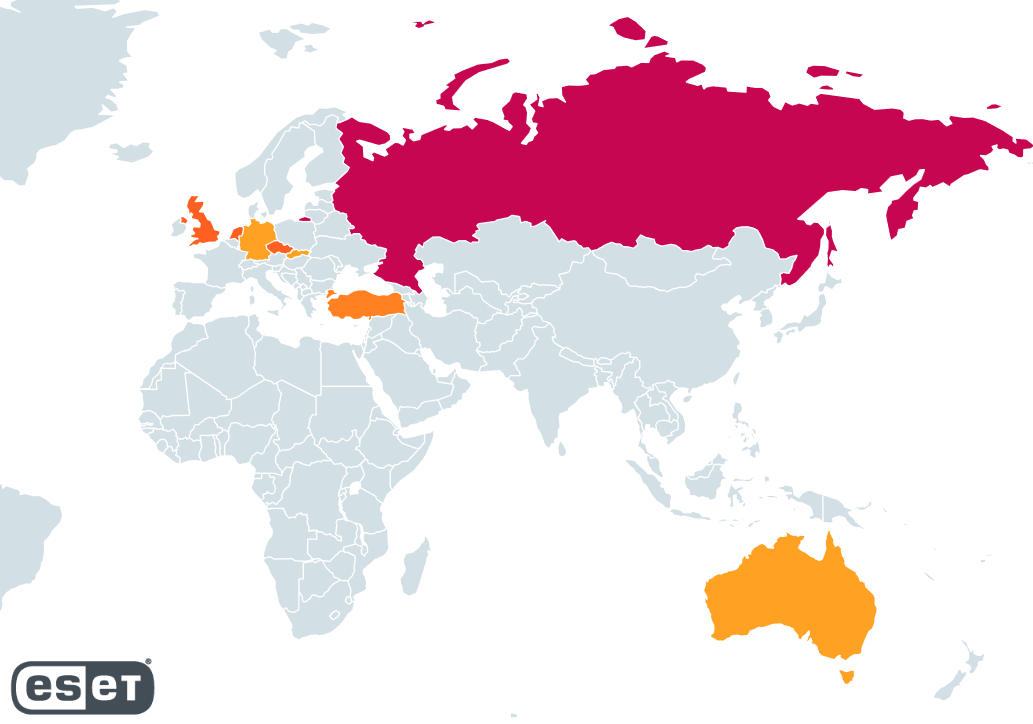 Figure 24. Heatmap showing nan geographical distribution of RedLine backend servers
Figure 24. Heatmap showing nan geographical distribution of RedLine backend servers
Dead-drop resolvers
As we already mentioned, nan 2023 versions of nan RedLine sheet utilized GitHub repositories arsenic dead-drop resolvers for its authentication servers. These repositories each contained a record pinch an encrypted database of server addresses. The record was encrypted utilizing a civilization module simply named RSA. In 1 type of this module, shown successful Figure 25, nan database was encrypted utilizing AES-CBC pinch a hardcoded cardinal and IV, and saved to a record named nodesUpdate.config.
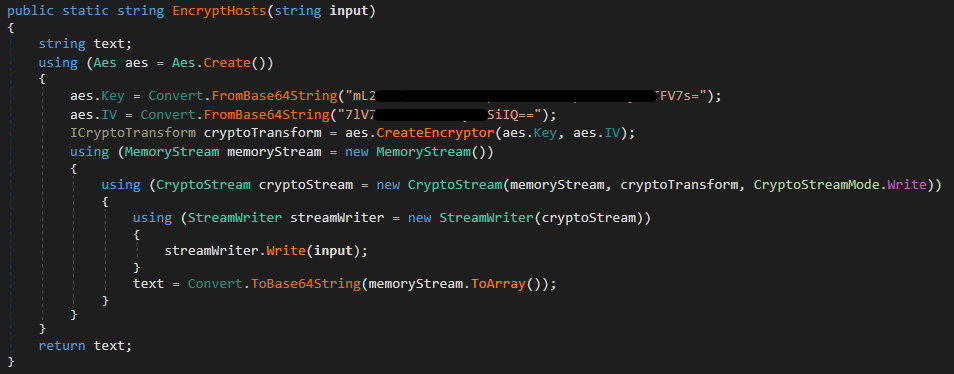 Figure 25. EncryptHosts usability pinch hardcoded AES cardinal and IV
Figure 25. EncryptHosts usability pinch hardcoded AES cardinal and IV
More caller versions, which were successful usage astatine slightest until mid 2024, employment RSA encryption alternatively (see Figure 26), pinch nan output written to a record named nodes.config. In this case, nan cardinal is publication from a record alternatively than being hardcoded successful nan executable. However, nan people utilized to execute RSA encryption is besides coming successful nan LoadBalancer module, pinch hardcoded default values for nan nationalist and backstage keys. Note nan usage of “nodes” again to mention to nan backend servers.
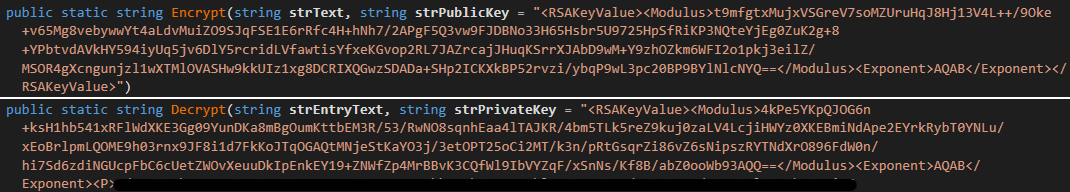 Figure 26. RSA encryption and decryption functions pinch hardcoded default keys
Figure 26. RSA encryption and decryption functions pinch hardcoded default keys
We person observed GitHub repositories that incorporate astatine slightest 1 specified encrypted file. Along pinch nan keys shown above, we were capable to extract an RSA backstage cardinal from a sample of nan panel. This allowed america to get lists of authentication servers, which we shared pinch rule enforcement agencies.
Conclusion
Before Operation Magnus, RedLine was among nan astir wide of infostealer malware pinch a very ample number of affiliates utilizing its power panel. However, nan malware-as-a-service endeavor seems to beryllium orchestrated by only a fistful of people, immoderate of whom person been identified by rule enforcement.
META Stealer, RedLine Stealer’s clone and astir most apt created by nan aforesaid threat actors, made its introduction into nan section successful 2022. It does not look to beryllium a successor to RedLine, since nan improvement of some families has continued successful parallel. It was taken down alongside RedLine Stealer.
Our in-depth study of nan behind-the-scenes parts of RedLine – its power sheet and backend – hopefully provides a much holistic knowing of this threat.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss (IoCs) and samples tin beryllium recovered successful our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| 1AD92153B56FC0B39F8FCEC949241EC42C22FA54 | Nodes.Api.exe | N/A | RedLine backend single-file application. |
| 8A0CAFE86C0774F1D9C7F198505AE15D04447DD6 | MainServer.exe | N/A | RedLine backend personification and advertisement guidance module (2024 version). |
| 607DBA5F630A1DBFF0E13EEBA2730AB9AB2FB253 | Nodes.Api.dll | N/A | RedLine backend main module. |
| FB3ABAC1FAC852AE6D22B7C4843A04CE75B65663 | Panel.exe | MSIL/Spy.RedLine.O | META stealer sheet (2024 version). |
| EE153B3F9B190B1492DEFBB1C70830A28F7C41B2 | RedLine.MainPanel.exe | MSIL/Spy.RedLine.H | RedLine stealer sheet (2024 version). |
| 1AB006B1C5403BA4648059DF93B6DAEB0E3EC43F | Panel.exe | MSIL/Spy.RedLine.O | RedLine stealer sheet (2024 version). |
| DC3A236245AE8C4D5D079E429ED6B77A5B5245C2 | RedLine.MainServer.exe | N/A | RedLine backend licensing server GUI. |
| 06A2A900561C122F45088A5EAE9146F7675C63F6 | rsa.exe | N/A | Tool to encrypt nan database of C&C servers. |
| 1626F2666782710FC28D4AFE607C7BE54F1FC67F | RedLine.Nodes.LoadBalancer.exe | N/A | RedLine backend server module. |
| 37D1221CE6BB82E7AD08FD22BD13592815A23468 | RedLine.SharedModels.dll | MSIL/Spy.RedLine.K | RedLine WCF models and contracts definitions. |
| 66C0E7E74C593196E0925A7B654E09258E3B1FB7 | Panel.exe | Win32/GenCBL.ATC | RedLine sheet (v22.4). |
| 2E5D9F2ED82C81609F4C49EA31642B1FB5FC11B5 | RedLine.MainPanel.exe | MSIL/Spy.RedLine.H | RedLine sheet (non-virtualized). |
| 47B78A5698A289C73175C5C69786DE40C7C93C12 | RedLine.SharedModels.dll | MSIL/Spy.RedLine.J | RedLine models and contracts definitions. |
| 49BE1D7C87AC919BB9083FA87F7B907E5F2C9835 | Panel.exe | MSIL/Spy.RedLine.H | META Stealer Panel. |
| 4BF4D42EED7FCA8FD52863B7020AC646EC6D97E9 | RedLine.Nodes.DbController.exe | N/A | RedLine backend server personification and advertisement guidance module. |
| 27BD472729439D5B8814D4A8A464AF9832198894 | Panel.exe | MSIL/Spy.RedLine.H | RedLine sheet (v26). |
| A154DFAEDC237C047F419EB6884DAB1EF4E2A17D | Panel.exe | MSIL/Spy.RedLine.H | RedLine Panel (leaked cracked version). |
Network
Note that nan domains successful nan array beneath person been seized by rule enforcement. The different sheet and server addresses that we collected were shared pinch rule enforcement agencies connected a regular ground to thief successful their actions and are nary longer active.
| IP | Domain | Hosting provider | First seen | Details |
| N/A | spasshik[.]xyz | N/A | 2024-06-02 | META backend REST server. |
| N/A | fivto[.]online | N/A | 2024-08-03 | RedLine backend REST server. |
MITRE ATT&CK techniques
This array was built utilizing version 15 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server | Instances of nan RedLine backmost extremity are hosted connected leased virtual backstage servers. |
| T1583.004 | Acquire Infrastructure: Server | Instances of nan RedLine backmost extremity are hosted connected servers that look to beryllium exclusive to RedLine. | |
| T1587.001 | Acquire Infrastructure: Web Services | Operators of RedLine person created aggregate GitHub accounts and repositories. | |
| T1587.002 | Develop Capabilities: Malware | Operators of RedLine person developed their ain malware families, power panels, and back-end servers. | |
| T1588.003 | Develop Capabilities: Code Signing Certificates | The RedLine backmost extremity automatically generates self-signed certificates erstwhile creating samples. | |
| T1608.002 | Obtain Capabilities: Code Signing Certificates | RedLine panels are signed pinch valid certificates issued to AMCERT,LLC. | |
| T1608.001 | Stage Capabilities: Upload Malware | Back-end components of RedLine are uploaded to backstage servers. | |
| Defense Evasion | T1622 | Debugger Evasion | The RedLine sheet automatically terminates itself if it detects a debugger aliases study tools. |
| T1027.002 | Obfuscated Files aliases Information: Software Packing | Samples of nan RedLine sheet are packed utilizing DNGuard and BoxedApp. | |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding | RedLine makes extended usage of base64 encoding successful its web communications. Network connection uses nan modular binary encoder of nan WCF framework. |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Communications betwixt nan sheet and back-end server usage AES encryption. In immoderate cases, dead-drop resolver contented is encrypted pinch AES-CBC. |
|
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | Communications betwixt nan sheet and back-end server usage RSA encryption. In immoderate cases, dead-drop resolver contented is encrypted pinch RSA. |
|
| T1071.001 | Application Layer Protocol: Web Protocols | Network connection successful caller versions is done via a REST API complete HTTPS. | |
| T1095 | Non-Application Layer Protocol | Network connection is done pinch nan WCF Framework complete TCP. | |
| T1102.001 | Web Service: Dead Drop Resolver | The RedLine sheet uses GitHub repositories arsenic dead-drop resolvers to get nan reside of back-end servers. | |
| T1571 | Non-Standard Port | By default, nan RedLine panel’s Guest Links functionality runs an HTTP server connected larboard 7766. |


 5 months ago
5 months ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·