ARTICLE AD BOX
ESET Research
Threat Reports
An overview of nan activities of selected APT groups investigated and analyzed by ESET Research successful Q2 2024 and Q3 2024

07 Nov 2024 • , 3 min. read

ESET APT Activity Report Q2 2024–Q3 2024 summarizes notable activities of selected precocious persistent threat (APT) groups that were documented by ESET researchers from April 2024 until nan extremity of September 2024. The highlighted operations are typical of nan broader scenery of threats we investigated during this period, illustrating nan cardinal trends and developments, and incorporate only a fraction of nan cybersecurity intelligence information provided to customers of ESET’s backstage APT reports.
During nan monitored period, we observed a notable description successful targeting by China-aligned MirrorFace. Typically focused connected Japanese entities, it extended its operations to see a negotiated statement successful nan European Union (EU) for nan first clip while continuing to prioritize its Japanese targets. Additionally, China-aligned APT groups person been relying progressively connected nan open-source and multiplatform SoftEther VPN to support entree to victims’ networks. We detected extended usage of SoftEther VPN by Flax Typhoon, observed Webworm switching from its full-featured backdoor to utilizing nan SoftEther VPN Bridge connected machines of governmental organizations successful nan EU, and noticed GALLIUM deploying SoftEther VPN servers astatine telecommunications operators successful Africa.
We besides observed indications that Iran-aligned groups mightiness beryllium leveraging their cybercapabilities to support negotiated espionage and, potentially, kinetic operations. These groups compromised respective financial services firms successful Africa – a continent geopolitically important to Iran; conducted cyberespionage against Iraq and Azerbaijan, neighboring countries pinch which Iran has analyzable relationships; and accrued their liking successful nan proscription assemblage successful Israel. Despite this seemingly constrictive geographical targeting, Iran-aligned groups maintained a world focus, besides pursuing negotiated envoys successful France and acquisition organizations successful nan United States.
North Korea-aligned threat actors persisted successful advancing nan goals of their regime, which has been accused by nan United Nations and South Korea of stealing costs – some accepted currencies and cryptocurrencies – to support its weapons of wide demolition programs. These groups continued their attacks connected defense and aerospace companies successful Europe and nan US, arsenic good arsenic targeting cryptocurrency developers, deliberation tanks, and NGOs. One specified group, Kimsuky, began abusing Microsoft Management Console files, which are typically utilized by strategy administrators but tin execute immoderate Windows command. Additionally, respective North Korea-aligned groups often misused celebrated cloud-based services, including Google Drive, Microsoft OneDrive, Dropbox, Yandex Disk, pCloud, GitHub, and Bitbucket. For nan first time, we saw an APT group – specifically ScarCruft – abusing Zoho unreality services.
We detected Russia-aligned cyberespionage groups often targeting webmail servers specified arsenic Roundcube and Zimbra, usually pinch spearphishing emails that trigger known XSS vulnerabilities. Besides Sednit targeting governmental, academic, and defense-related entities worldwide, we identified different Russia-aligned group, which we named GreenCube, stealing email messages via XSS vulnerabilities successful Roundcube. Other Russia-aligned groups continued to attraction connected Ukraine, pinch Gamaredon deploying ample spearphishing campaigns while reworking its devices utilizing and abusing nan Telegram and Signal messaging apps. Sandworm utilized its caller Windows backdoor, which we named WrongSens, and its precocious Linux malware: LOADGRIP and BIASBOAT. Additionally, we detected Operation Texonto, a disinformation and psychological cognition chiefly aimed astatine demoralizing Ukrainians, besides targeting Russian dissidents. We besides analyzed nan nationalist hack-and-leak of nan Polish Anti-Doping Agency, which we judge was compromised by an first entree agent who past shared entree pinch nan Belarus-aligned FrostyNeighbor APT group, nan entity down cyber-enabled disinformation campaigns captious of nan North Atlantic Alliance. Finally, from analyzing an utilization recovered successful nan wild, we discovered a distant codification execution vulnerability successful WPS Office for Windows. We property nan onslaught leveraging nan utilization to nan South Korea-aligned APT-C-60 group.
Malicious activities described successful ESET APT Activity Report Q2 2024–Q3 2024 are detected by ESET products; shared intelligence is based mostly connected proprietary ESET telemetry information and has been verified by ESET researchers.
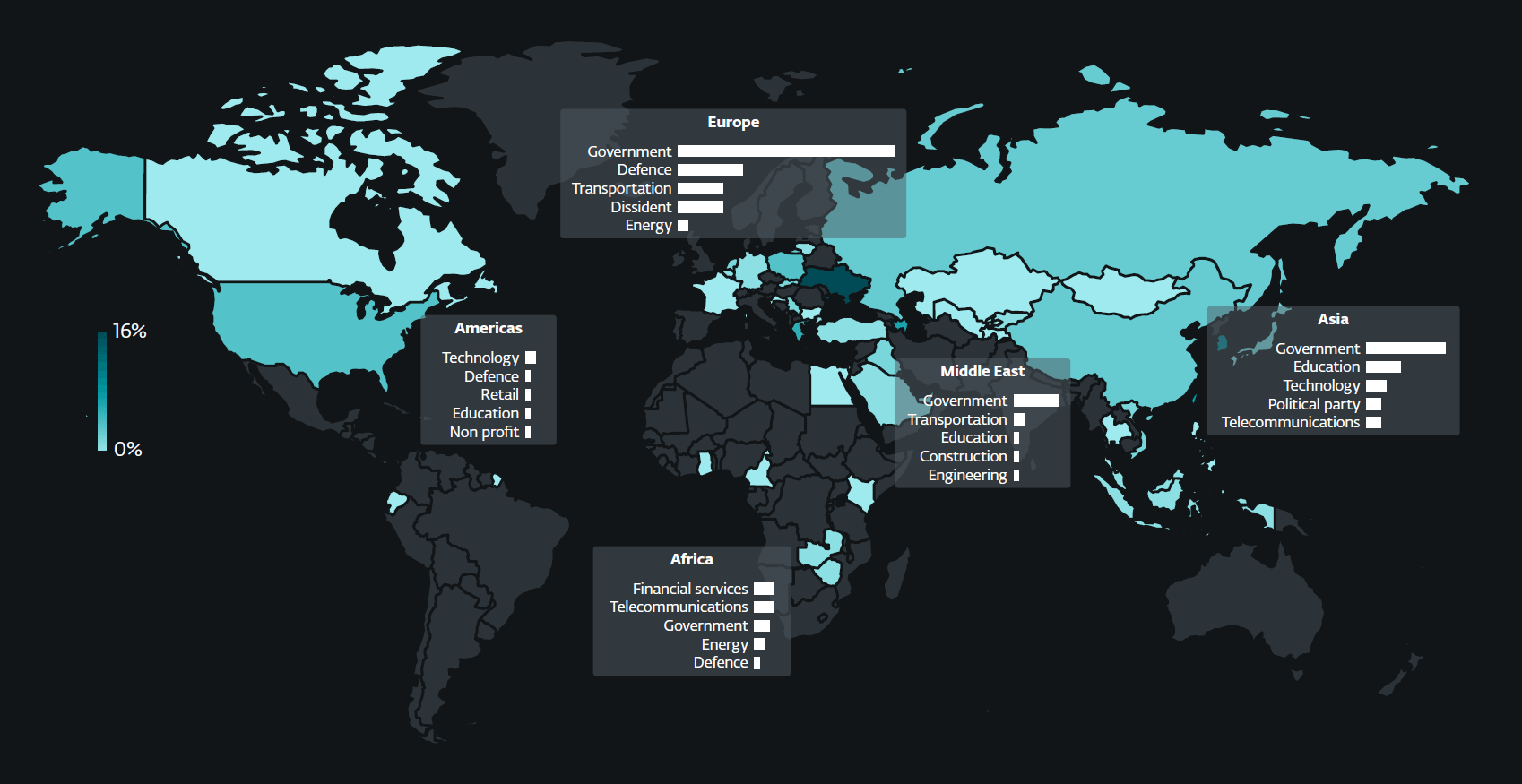 Figure 1. Targeted countries and sectors
Figure 1. Targeted countries and sectors
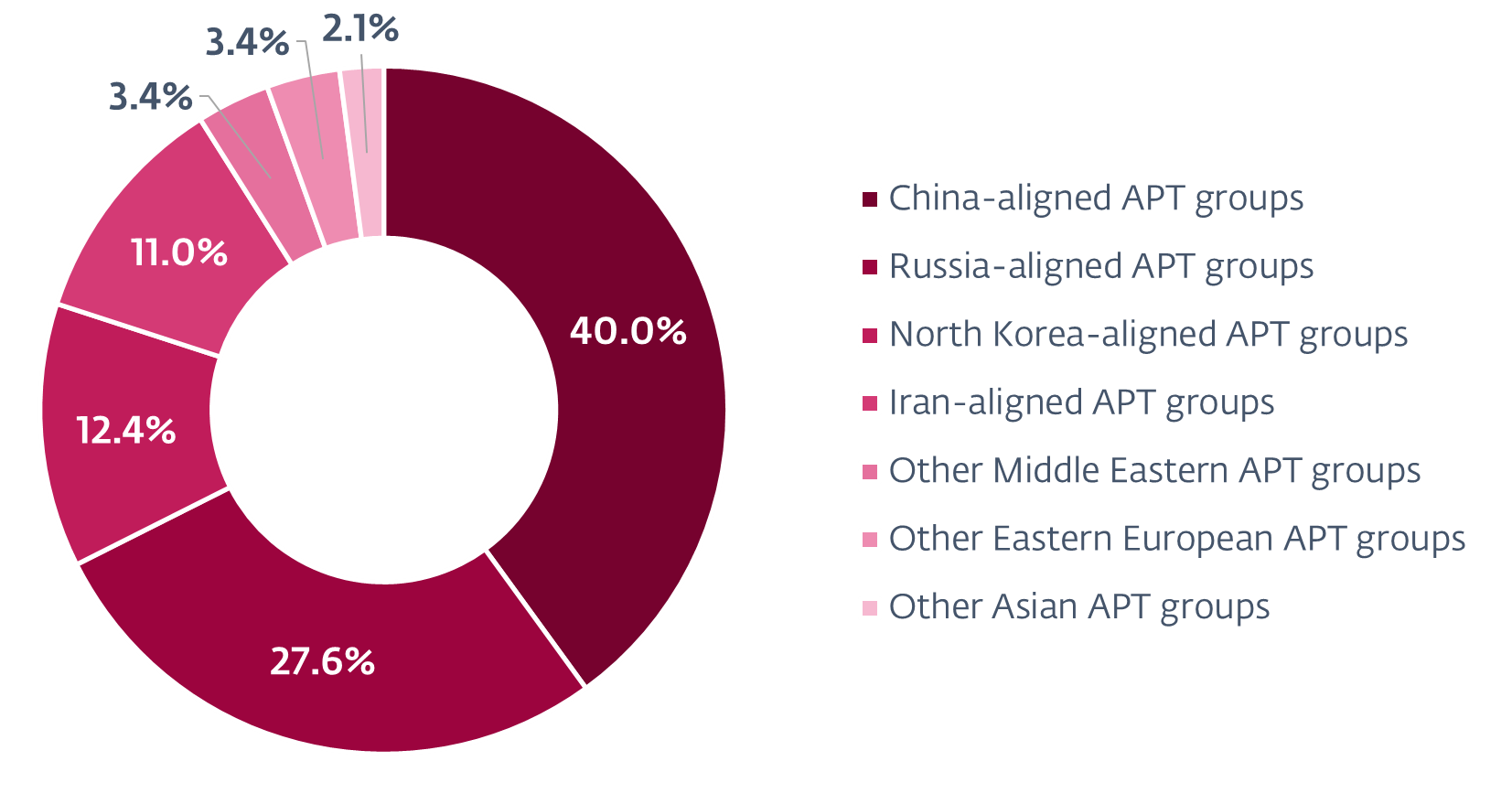 Figure 2. Attack sources
Figure 2. Attack sources
ESET APT Activity Reports incorporate only a fraction of nan cybersecurity intelligence information provided successful ESET APT Reports PREMIUM. For much information, sojourn nan ESET Threat Intelligence website.
Follow ESET investigation connected Twitter for regular updates connected cardinal trends and apical threats.
Let america support you
up to date
Sign up for our newsletters

 5 months ago
5 months ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·