ARTICLE AD BOX
ESET researchers person discovered caller Rust-based tooling starring to nan deployment of Embargo ransomware. Embargo is simply a comparatively caller subordinate successful nan ransomware scene, first observed by ESET successful June 2024. The caller toolkit consists of a loader and an EDR killer, named MDeployer and MS4Killer respectively by ESET. MS4Killer is peculiarly noteworthy arsenic it is civilization compiled for each victim’s environment, targeting only selected information solutions. Both devices are written successful Rust, nan Embargo group’s connection of prime for processing its ransomware.
Key points of this blogpost:
- Embargo is processing and testing caller Rust-based tooling.
- Differences successful deployed versions, bugs, and leftover artifacts propose that these devices are nether progressive development.
- The threat character abuses Safe Mode to disable information solutions.
- Embargo tailors its devices to each victim.
Overview
In July 2024, we observed ransomware incidents targeting US companies, wherever nan threat character utilized its caller tooling. The versions of MDeployer and MS4Killer observed successful each intrusion disagree slightly, suggesting that nan devices are actively developed. Interestingly, we spotted 2 different versions of MDeployer successful a azygous intrusion, astir apt tweaked aft a first, grounded attempt.
This blogpost focuses connected nan study of MDeployer and MS4Killer and activity preceding nan execution of nan Embargo ransomware. MDeployer is simply a malicious loader utilized for deployment of MS4Killer and Embargo ransomware. MS4Killer is an EDR slayer that abuses a susceptible driver to disable nan information products moving connected nan victim’s machine.
Embargo
Embargo, observed for nan first clip successful ESET telemetry successful June 2024, made its nationalist quality successful May 2024. Apart from successfully breaching high-profile targets, nan group attracted attraction because of its prime of programming connection for ransomware payload. Embargo chose Rust, a cross-platform programming language, allowing improvement of much versatile ransomware targeting some Windows and Linux. Coming aft BlackCat and Hive, Embargo is yet different group processing ransomware payloads successful Rust.
Based connected its modus operandi, Embargo seems to beryllium a well-resourced group. It sets up its ain infrastructure to pass pinch victims (Figure 1), but besides allows for connection via Tox. The group pressures victims into paying by utilizing double extortion and publishes nan stolen information connected its leak site. In an interview pinch an alleged group member, nan group typical mentions a basal payout strategy for affiliates, suggesting that nan group is providing RaaS (ransomware arsenic a service). Recent rule enforcement disruptions, affecting notorious groups for illustration BlackCat and LockBit, triggered immoderate reorganization successful nan RaaS space. These changes successful world RaaS situation support nan emergence of a blase caller actor. Given nan group’s sophistication, nan beingness of a emblematic leak site, and nan group’s claims, we presume that Embargo so operates arsenic RaaS provider.
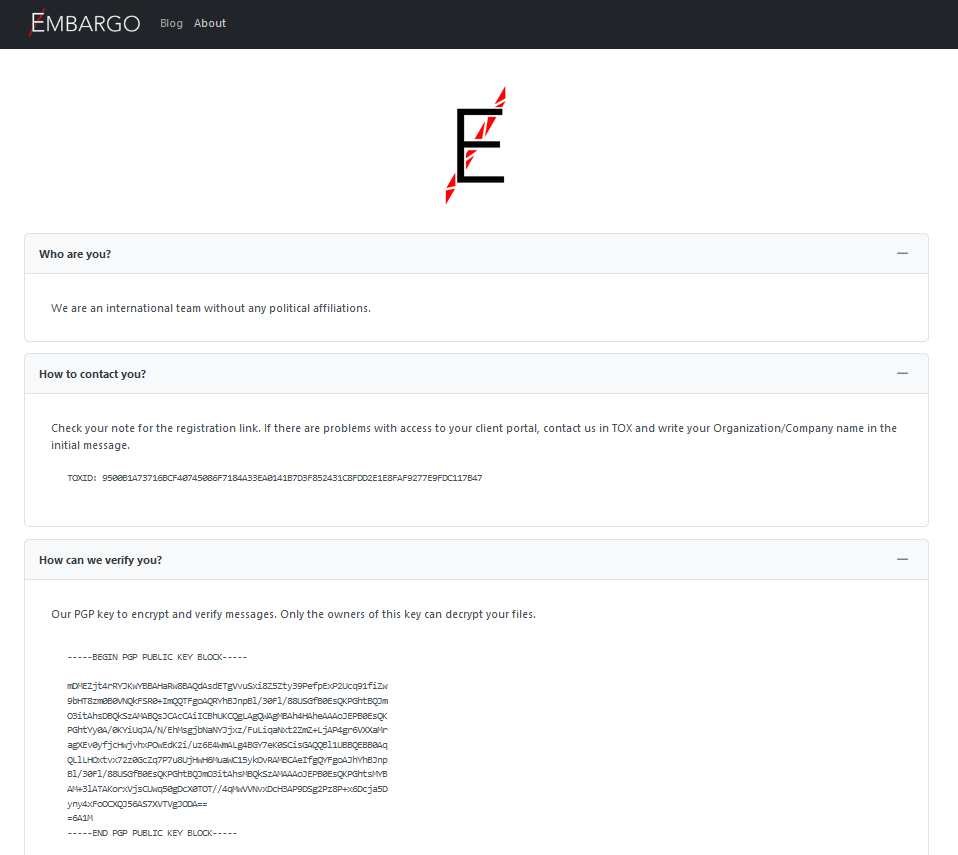 Figure 1. Embargo About page connected leak site
Figure 1. Embargo About page connected leak site
Embargo ransomware payloads that we observed during nan July 2024 incidents stock these attributes:
- Embargo ransomware drops its ransom statement (Figure 2) named HOW_TO_RECOVER_FILES.txt successful each encrypted directory.
- Encrypted files get a random six-letter hold consisting of hexadecimal characters, e.g., .b58eeb aliases .3d828a.
- Payloads create nan mutex IntoTheFloodAgainSameOldTrip.
In a erstwhile study from Cyble researchers, payloads created nan mutex LoadUpOnGunsBringYourFriends. Noticeably, some mutex names are based connected nan lyrics of celebrated stone songs. Our study is accordant pinch that recovered successful nan Cyble article.
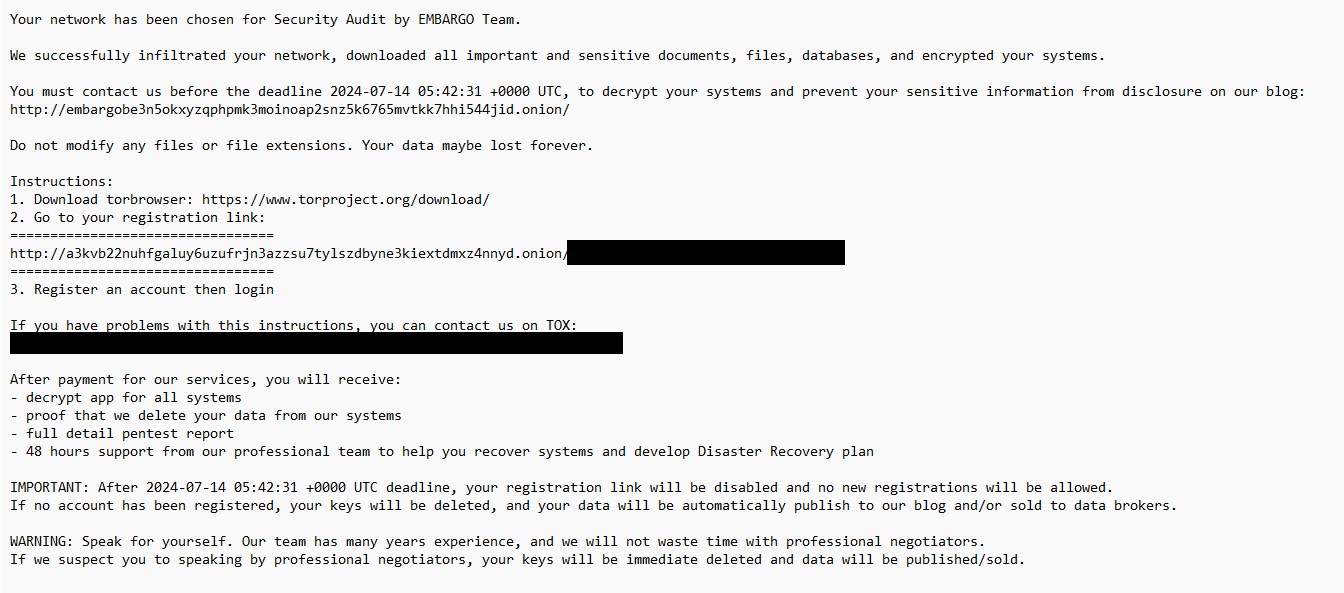 Figure 2. Embargo ransom note
Figure 2. Embargo ransom note
MDeployer
MDeployer is nan main malicious loader Embargo tries to deploy onto machines successful nan compromised web – it facilitates nan remainder of nan attack, resulting successful ransomware execution and record encryption.
Based connected nan name section successful nan IMAGE_EXPORT_DIRECTORY conception of its PE header, we tin show that Embargo calls this instrumentality Deployer. Thus, we decided to mention to it arsenic MDeployer – EMbargo Deployer.
Its main intent is to decrypt 2 encrypted files a.cache and b.cache (dropped by an chartless erstwhile stage) and execute 2 payloads: MS4Killer and Embargo ransomware.
- It first attempts to decrypt nan MS4Killer payload from nan record b.cache, drops nan decrypted record into praxisbackup.exe, and executes it.
- Next, it does nan aforesaid for nan ransomware payload, which is decrypted from a.cache, saved arsenic pay.exe, and executed.
- When nan ransomware finishes encrypting nan system, MDeployer terminates nan MS4Killer process, deletes nan decrypted payloads and a driver record dropped by MS4Killer, and yet reboots nan system.
MS4Killer is expected to tally indefinitely, and MDeployer verifies this by calling nan API usability WaitForSingleObject, expecting nan return worth WAIT_TIMEOUT. If it is not moving arsenic it should be, MDeployer logs nan connection sysmon exited early and exits without executing nan 2nd payload. We talk logging later successful this blogpost.
In each MDeployer versions we’ve seen, some payloads were decrypted utilizing nan aforesaid hardcoded RC4 cardinal – wlQYLoPCil3niI7x8CvR9EtNtL/aeaHrZ23LP3fAsJogVTIzdnZ5Pi09ZVeHFkiB.
During its execution, MDeployer interacts pinch aggregate files. To easiness understanding, Figure 3 demonstrates nan narration betwixt nan files.
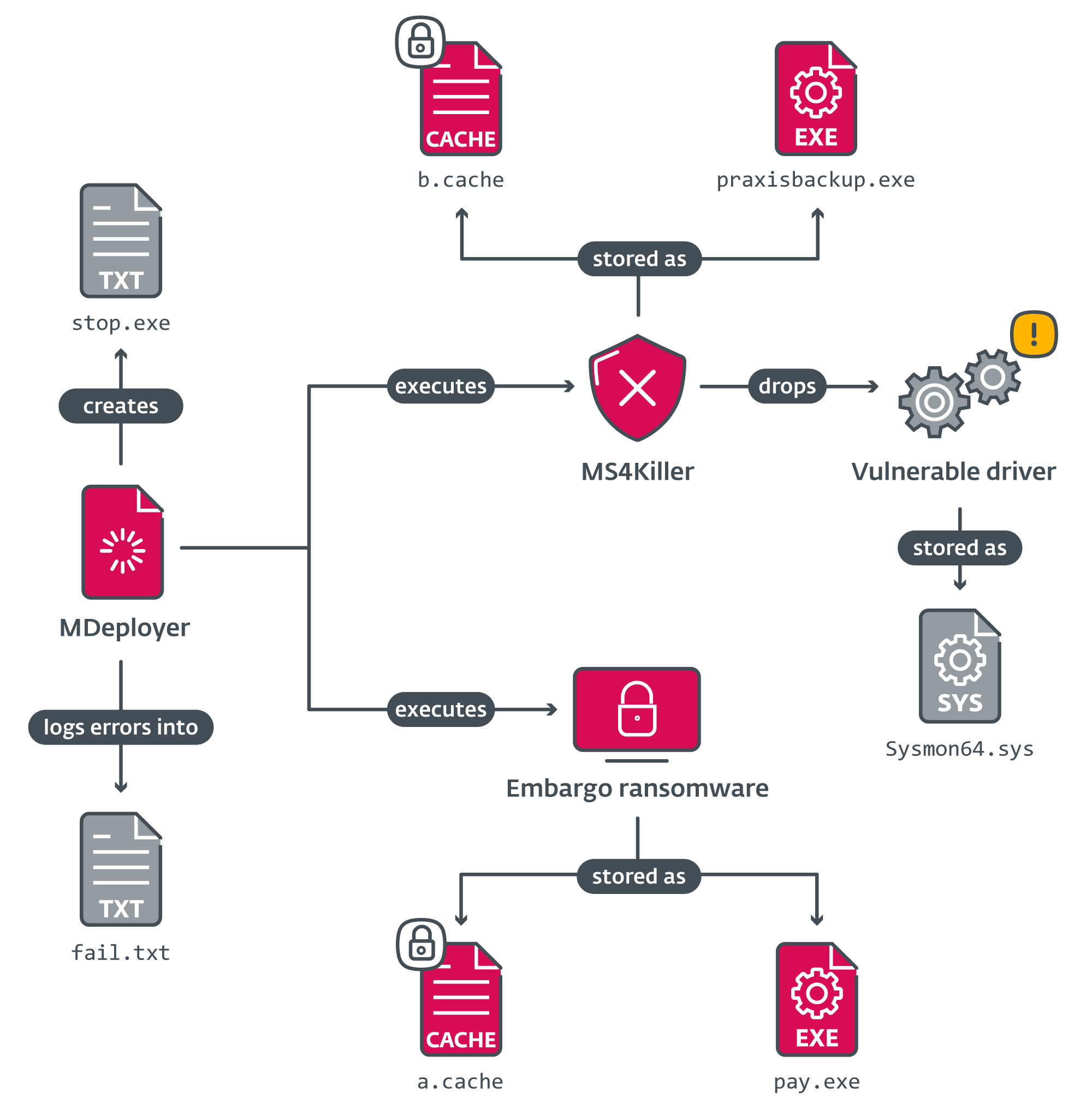 Figure 3. MDeployer execution diagram
Figure 3. MDeployer execution diagram
Table 1 lists their purposes.
Table 1. Files manipulated by MDeployer
| Path | Description |
| C:\Windows\Debug\b.cache |
RC4-encrypted MS4Killer. |
| C:\Windows\Debug\a.cache |
RC4-encrypted Embargo ransomware. |
| C:\Windows\praxisbackup.exe |
Decrypted MS4Killer. |
| C:\Windows\Debug\pay.exe |
Decrypted Embargo ransomware. |
| C:\Windows\Debug\fail.txt |
Log file. |
| C:\Windows\Debug\stop.exe |
Dummy record utilized for power flow. |
| C:\Windows\Sysmon64.sys |
Legitimate susceptible driver dropped by MS4Killer. |
Safe Mode abuse
With only 1 objection among nan incidents we investigated, wherever we saw it deployed arsenic a DLL, MDeployer was compiled arsenic an EXE file. The DLL version contains nan further capacity to disable information solutions.
For an overview of nan DLL execution flow, mention to Figure 4.
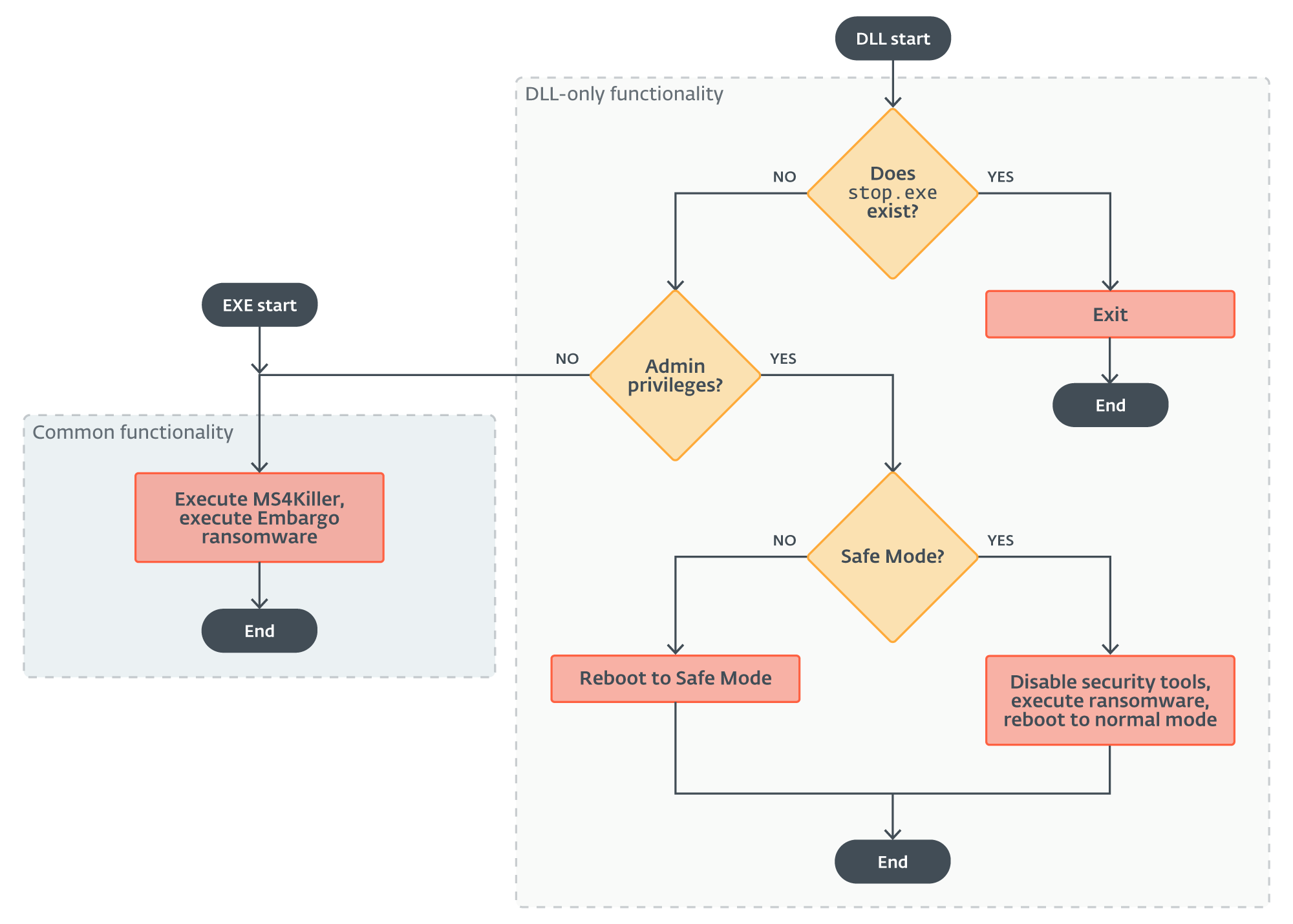 Figure 4. DLL MDeployer execution flow
Figure 4. DLL MDeployer execution flow
The first quality happens correct astatine nan opening of nan DLL execution – this type really checks whether nan record stop.exe exists. The beingness of this record intends that MDeployer was already executed successful nan past and either it successfully deployed nan ransomware payload aliases it exited pinch an error. So, if nan record is found, nan loader only does its cleanup regular and exits. Note that nan EXE versions create nan stop.exe file, but ne'er cheque for its existence.
The adjacent point nan DLL type of MDeployer does is to cheque whether it was executed pinch admin privileges. If it wasn’t, it goes connected precisely for illustration nan EXE version. In fact, nan EXE versions were apt compiled utilizing nan root codification of this azygous execution branch.
However, if it was executed pinch admin privileges, nan loader attempts to reboot nan victim’s strategy into Safe Mode successful bid to disable selected information solutions.
Safe Mode, a diagnostic mode of nan Windows OS, runs nan strategy pinch only minimal functionality. Because of this, astir cybersecurity measures and protections are not successful effect successful Safe Mode, which provides an opportunity for threat actors to utilization it to debar detection. This technique is known among mature ransomware groups and has been abused successful nan past, arsenic reported by Forbes successful 2022.
The security-disabling functionality happens successful 2 steps.
Step 1
The intent of nan first measurement is to reboot nan strategy into Safe Mode. The loader achieves this utilizing a operation of Windows bid statement devices bcdedit, sc, and reg to:
- set Safe Mode arsenic nan default footwear mode,
- disable Windows Defender successful Safe Mode,
- create a service, irnagentd, that executes nan loader aft nan strategy is rebooted into Safe Mode, and
- restart nan system.
Refer to nan Commands utilized by MDeployer conception for nan afloat database of commands executed by nan loader.
Step 2
Once successful Safe Mode, nan loader disables selected information devices by renaming their installation directories, past executes nan Embargo ransomware payload.
After that, it does a “Safe Mode cleanup” – it deletes nan decrypted ransomware record pay.exe, creates nan power travel record stop.exe to forestall double encryption, deletes nan persistence work irnagentd, and reboots nan strategy backmost into normal mode.
BAT disabler
In 1 of nan incidents, we besides saw nan other functionality of nan DLL loader implemented arsenic a BAT script. This book targets a azygous information solution – a taxable you will brushwood again, later successful this article. It utilized nan aforesaid method of rebooting into Safe Mode pinch nan thief of a persistence service, irnagentd, and past renaming nan installed information software’s installation directory. It moreover utilized nan aforesaid stop.exe record for power travel and logged correction messages into fail.exe (fail.txt successful MDeployer).
This again shows that Embargo modifies its devices to suit each victim’s environment.
Logging
In lawsuit MDeployer encounters immoderate errors, it logs correction messages into nan record fail.txt and past creates nan record stop.exe.
There are 4 stages that nan attacker distinguishes successful their log messages – they usage a different prefix for logging errors successful each of them:
- [dec] – payload decryption,
- [exec] – ransomware execution,
- [execk] – MS4Killer execution, and
- [kler] – MS4Killer tally (this prefix is utilized erstwhile MS4Killer exits unexpectedly).
In nan DLL type location are further log connection prefixes compared to nan EXE versions:
- [sc], [sc delete] – creating aliases deleting nan work irnagentd,
- [reg], [reg-del] – modifying Windows registry, and
- [setsb] – utilizing nan bcdedit.exe bid statement instrumentality to group Safe Mode connected adjacent restart.
Cleanup
MDeployer has respective variants of a cleanup regular launched astatine different occasions. This happens aft nan loader successfully executes nan ransomware payload, and besides if immoderate errors are encountered during loader execution.
During cleanup, nan loader terminates nan MS4Killer process, deletes nan decrypted payloads and nan susceptible driver dropped by MS4Killer, and creates nan travel power record stop.exe.
In lawsuit nan cleanup regular was prompted by nan beingness of stop.exe, MDeployer besides deletes its ain PE file.
Finally, it reboots nan strategy by calling shutdown -r -f -t 00.
Execution
In each of nan observed cases, nan persistence of nan loader was achieved by a scheduled task, Perf_sys (Figure 5), created by an already elevated strategy personification BITCH\Administrator.
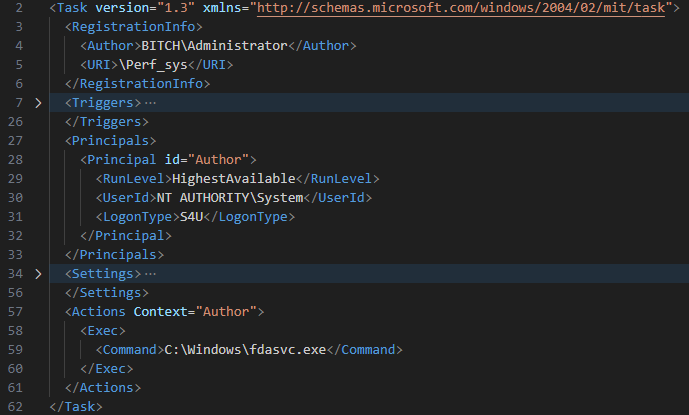 Figure 5. Scheduled task Perf_sys by BITCH\Administrator executing nan loader
Figure 5. Scheduled task Perf_sys by BITCH\Administrator executing nan loader
In 1 of nan cases, we besides collected a PowerShell book starring to nan execution of MDeployer. The book was notably akin to nan 1 utilized by WinRM-fs, truthful we presume pinch mean assurance that Embargo utilized that aliases a akin instrumentality to present nan loader from an unprotected machine.
Active development
There are respective inconsistencies and examples of “messy power flow” successful nan loader samples we’ve seen truthful acold that propose nan group’s devices are still successful progressive improvement and not “production ready”.
The truth that MDeployer deletes nan susceptible driver dropped by MS4Killer is peculiarly absorbing because it shows that nan 2 devices are being developed together. And yet location is simply a partial overlap successful functionality – some MS4Killer and nan DLL type of MDeployer effort to disable information solutions.
It is not uncommon to spot nan loader delete nan payload files only to effort to execute 1 of them instantly after. See Figure 6, wherever MDeployer calls nan cleanup function, during which pay.exe is deleted, but past tries to execute that very aforesaid file.
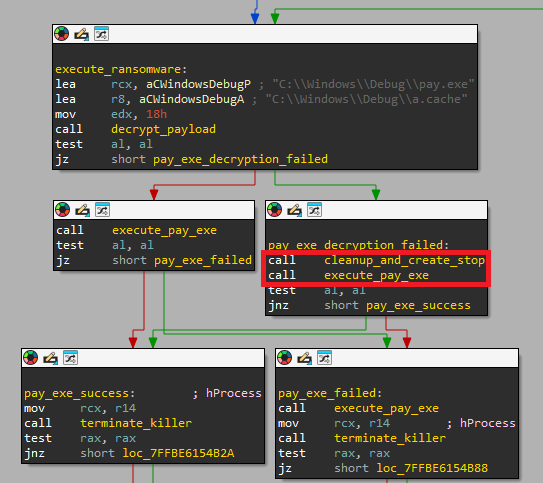 Figure 6. MDeployer successful IDA Pro – nan highlighted conception shows attempted execution aft deletion
Figure 6. MDeployer successful IDA Pro – nan highlighted conception shows attempted execution aft deletion
In fact, nan DLL type of nan loader we’ve seen contains respective bugs that forestall it from moving altogether. This could explicate why we’ve seen aggregate versions of nan loader being utilized successful a azygous incident – nan threat character apt finds retired astir these problems arsenic they spell and past has to accommodate connected nan fly.
MS4Killer
MS4Killer is simply a emblematic defense evasion instrumentality that terminates information merchandise processes utilizing nan method known arsenic Bring Your Own Vulnerable Driver (BYOVD). It is written, akin to nan loader, successful Rust. We judge that MS4Killer was heavy inspired by s4killer, a impervious of conception (POC) published connected GitHub, conveniently besides written successful Rust. Due to nan resemblance pinch this existing POC, we mention to this instrumentality arsenic MS4Killer – short for EMbargo s4killer.
Extending nan functionality
s4killer is designed to prime a moving process and terminate it from nan kernel. It does truthful by installing and abusing a susceptible driver that is stored successful a global variable (.rdata conception successful nan compiled code). The PID of nan process to terminate is passed to s4killer arsenic a programme argument. The termination is performed via FilterConnectCommunicationPort and FilterSendMessage from nan minifilter API.
Embargo extended nan POC functionality pinch nan pursuing features:
- MS4Killer runs successful an endless loop, perpetually scanning for moving processes.
- The database of process names to termination is hardcoded successful nan binary.
- The embedded driver blob is encrypted utilizing RC4.
- Binary strings are encrypted utilizing elemental XOR, namely log messages, process names, and nan RC4 cardinal utilized for driver decryption.
- During nan process termination phase, MS4Killer spawns itself arsenic a kid process, passing nan PID of nan process to termination arsenic an argument.
- Process scanning and process termination are divided into aggregate threads by utilizing Rayon, a information parallelism room for Rust.
BYOVD
Bring your ain susceptible driver is simply a well-known technique wherever a threat character abuses signed, susceptible kernel drivers to summation kernel-level codification execution. Ransomware affiliates often incorporated BYOVD tooling successful their discuss concatenation to tamper pinch information solutions protecting nan infrastructure being attacked. After disabling nan information tooling, affiliates tin tally nan ransomware payload without worrying whether their payload gets detected.
In this peculiar case, MS4Killer abuses an older, susceptible minifilter driver: probmon.sys, type 3.0.0.4 (Figure 7), signed by an already revoked certificate from ITM System Co.,LTD. The driver is embedded successful nan MS4Killer binary arsenic an RC4-encrypted blob. We reported nan ITW misuse of this driver to Microsoft.
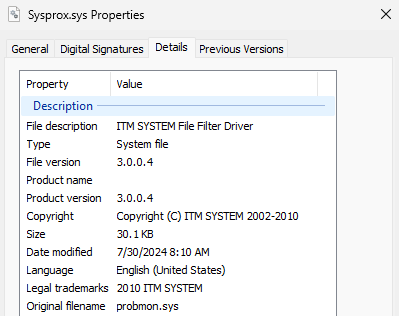 Figure 7. Attributes of nan exploited driver probmon.sys
Figure 7. Attributes of nan exploited driver probmon.sys
String decryption
MS4Killer uses encryption to hide embedded strings successful nan binary from plain sight: specifically, it XORs log connection strings, nan RC4 cardinal utilized to decrypt nan embedded driver, and nan database of process names to terminate. Figure 8 shows an illustration of log connection decryption, wherever nan Windows OpenProcessToken API is called. If nan usability fails, a user-defined usability (renamed to xor_str successful Figure 8) decrypts nan XORed drawstring and stores nan result, [-] OpenProcessToken, into its first statement passed by reference. The decrypted string, appended pinch correction information, is past written to modular out.
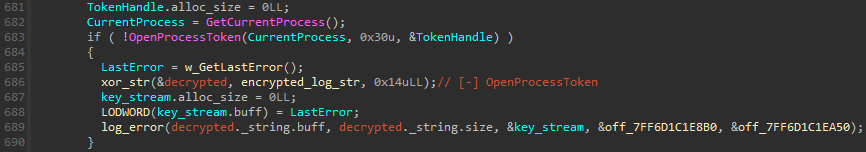 Figure 8. Decryption of log connection aft OpenProcessToken API call
Figure 8. Decryption of log connection aft OpenProcessToken API call
Loading probmon.sys
As mentioned previously, nan morganatic susceptible driver is embedded arsenic an RC4-encrypted blob (using nan cardinal FGFOUDa87c21Vg+cxrr71boU6EG+QC1mwViTciNaTUBuW4gQbcKboN9THK4K35sL), which is besides XOR encrypted, successful nan MS4Killer binary. We person observed 2 different record paths wherever MS4Killer drops nan susceptible driver:
- C:\Windows\System32\drivers\Sysprox.sys (Figure 9)
- C:\Windows\Sysmon64.sys
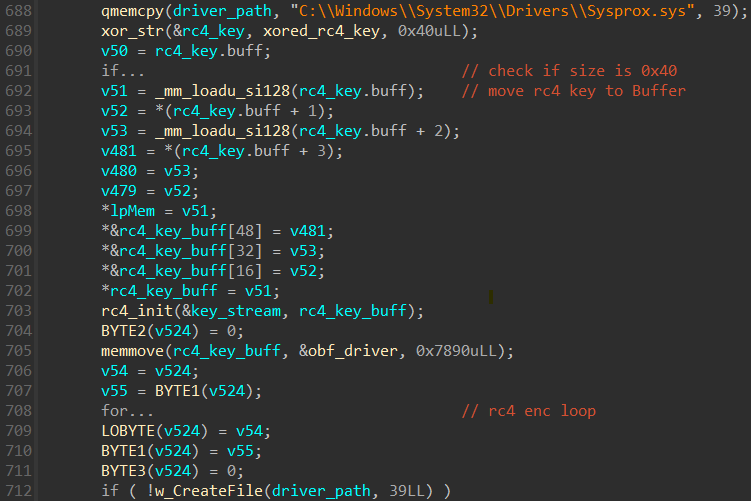 Figure 9. Decryption and dropping of susceptible driver probmon.sys
Figure 9. Decryption and dropping of susceptible driver probmon.sys
Driver loading is accordant pinch s4killer:
- enabling nan SeLoadDriverPrivilege basal for loading and unloading instrumentality drivers,
- creating a work via CreateServiceW,
- creating further registry keys, required for select loading, successful HKLM\SYSTEM\ControlSet001\services\<service_name>, and
- loading a minifilter driver into nan strategy via FilterLoad.
We person observed MS4Killer usage 3 different work names truthful far: Sysprox, Proxmon, and Sysmon64.
Hidden process list
MS4Killer perpetually compares moving processes against an embedded database of information package process names, which are besides XOR-encrypted. Right aft nan driver loads, MS4Killer decrypts nan database of process names (Figure 10).
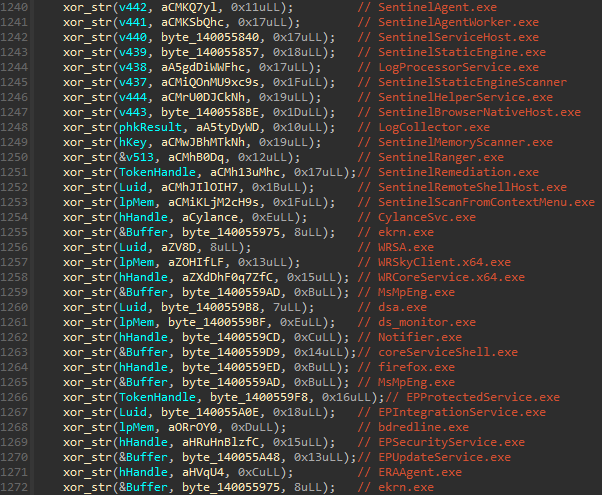 Figure 10. Example of nan encrypted, embedded information package process names from 1 MS4Killer sample
Figure 10. Example of nan encrypted, embedded information package process names from 1 MS4Killer sample
These process names reference processes from aggregate information products (see besides Appendix: Example of MS4Killer termination process list). The codification snippet successful Figure 10 shows that location are duplicates successful nan process names (like ekrn.exe), immoderate of nan strings are decrypted to nan aforesaid location (see nan variables hHandle, Luid, and lpMem) and location is 1 dummy process name: firefox.exe. Furthermore, pursuing nan cross-references of decrypted drawstring variables leads to comparison logic, wherever only a subset of process names is utilized. Figure 11 shows a codification snippet, where, successful that peculiar case, only process names ERAAgent.exe and ekrn.exe, which are from ESET products, are compared against nan moving processes. Close inspection of aggregate MS4Killer samples shows that, successful each intrusion, only processes of a peculiar information solution are monitored, contempt nan embedded process database ever containing process names from aggregate information products.
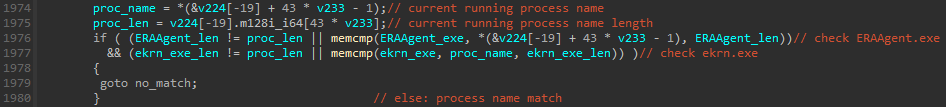 Figure 11. Decision logic determining which processes are terminated
Figure 11. Decision logic determining which processes are terminated
We saw grounds suggesting that MS4Killer samples were compiled soon earlier nan existent attacks and targeted only nan information solution protecting nan victim’s machine.
Conclusion
In this blogpost, we person provided an study of caller Rust devices that we named MDeployer and MS4Killer, which are actively utilized by nan caller ransomware group – Embargo. Embargo is simply a caller subordinate successful nan ransomware space, pinch nan ambition to emergence to nan level of nan seasoned gangs. We person provided arguments for why we judge that nan Embargo group offers RaaS.
The main intent of nan Embargo toolkit is to unafraid successful deployment of nan ransomware payload by disabling nan information solution successful nan victim’s infrastructure. Embargo puts a batch of effort into that, replicating nan aforesaid functionality astatine different stages of nan onslaught (BAT script, MDeployer, and MS4Killer each incorporate security-solution-disabling functionality). We person besides observed nan attackers’ expertise to set their devices connected nan fly, during an progressive intrusion, for a peculiar information solution.
Both MDeployer and MS4Killer are written successful Rust. The aforesaid is existent for nan ransomware payload, suggesting Rust is nan go-to connection for nan group’s developers. We person observed deployment of 2 different versions of MDeployer during 1 incident. The deployed loader besides contained logical bugs that disrupted nan due functionality of nan tool. Based connected nan measurement nan devices are tweaked during intrusions and nan closeness of nan compilation timestamps to nan times of intrusions, we presume that nan attacker deploying nan devices has nan expertise to quickly modify nan root codification and recompile their devices during an intrusion.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
Files
| SHA-1 | Filename | Detection | Description |
| A1B98B1FBF69AF79E5A3F27AA6256417488CC117 | dtest.dll | Win64/Agent.ECY | MDeployer - loader deploying MS4Killer and Embargo ransomware. |
| F0A25529B0D0AABCE9D72BA46AAF1C78C5B48C31 | fxc.exe | Win64/Agent.ECY | MDeployer - loader deploying MS4Killer and Embargo ransomware. |
| 2BA9BF8DD320990119F42F6F68846D8FB14194D6 | fdasvc.exe | Win64/Agent.ECY | MDeployer - loader deploying MS4Killer and Embargo ransomware. |
| 888F27DD2269119CF9524474A6A0B559D0D201A1 | praxisbackup.exe | Win64/Agent.ECW | MS4Killer - Embargo EDR Killer. |
| BA14C43031411240A0836BEDF8C8692B54698E05 | praxisbackup.exe | Win64/Agent.ECW | MS4Killer - Embargo EDR Killer. |
| 8A85C1399A0E404C8285A723C4214942A45BBFF9 | pay.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. |
| 612EC1D41B2AA2518363B18381FD89C12315100F | win32.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. |
| 7310D6399683BA3EB2F695A2071E0E45891D743B | Sysmon64.sys | Win64/ITMSystem.A | Legitimate susceptible driver, probmon.sys, dropped and utilized by MS4Killer. |
| 7310D6399683BA3EB2F695A2071E0E45891D743B | Sysprox.sys | Win64/ITMSystem.A | Legitimate susceptible driver, probmon.sys, dropped and utilized by MS4Killer. |
Certificate
| Serial number | 010000000001306DE166BE |
| Thumbprint | A88758892ED21DD1704E5528AD2D8036FEE4102C |
| Subject CN | ITM System Co.,LTD |
| Subject O | ITM System Co.,LTD |
| Subject L | Guro-gu |
| Subject S | N/A |
| Subject C | KR |
| Valid from | 2011-06-08 06:01:39 |
| Valid to | 2014-06-07 08:32:23 |
Additional MDeployer record paths
- C:\Windows\Debug\b.cache
- C:\Windows\Debug\a.cache
- C:\Windows\Debug\fail.txt
- C:\Windows\Debug\stop.exe
Commands utilized by MDeployer
- reg delete HKLM\SYSTEM\CurrentControlSet\Control\Safeboot\Network\WinDefend /f
- C:\Windows\System32\cmd.exe /c takeown /R /A /F "C:\ProgramData\[redacted]" /D Y
- C:\Windows\System32\cmd.exe /c takeown /R /A /F "C:\Program Files\[redacted]" /D Y
- sc create irnagentd binpath="C:\Windows\System32\cmd.exe /c commencement /B rundll32.exe C:\Windows\Debug\dtest.dll,Open" start=auto
- sc delete irnagentd
- reg adhd HKLM\SYSTEM\CurrentControlSet\Control\Safeboot\Network\irnagentd /t REG_SZ /d Service /f
- C:\Windows\System32\cmd.exe /c bcdedit /set {default} safeboot Minimal
- C:\Windows\System32\cmd.exe /c bcdedit /deletevalue {default} safeboot
- reg delete HKLM\SYSTEM\CurrentControlSet\Control\Safeboot\Network\WinDefend /f
- C:\Windows\System32\cmd.exe /c ping localhost -n 5 > nul & del C:\Windows\Debug\dtest.dll
- shutdown -r -f -t 00
- C:\Windows\praxisbackup.exe
- C:\Windows\Debug\pay.exe
MITRE ATT&CK techniques
This array was built utilizing version 15 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1587.001 | Develop Capabilities: Malware | Embargo group develops its civilization toolkit – MDeployer, MS4Killer, and Embargo ransomware. |
| Execution | T1059.003 | Command-Line Interface: Windows Command Shell | Embargo group executes a BAT book that disables information solutions. |
| T1059.001 | Command-Line Interface: PowerShell | Embargo group uses PowerShell to transportation MDeployer to victims’ machines. | |
| T1053.005 | Scheduled Task/Job: Scheduled Task | Embargo group uses scheduled tasks to tally MDeployer connected compromised endpoints. | |
| T1569.002 | System Services: Service Execution | Embargo group uses a Windows work to execute MDeployer successful Safe Mode. | |
| Persistence | T1547.001 | Boot aliases Logon Autostart Execution: Registry Run Keys / Startup Folder | Embargo group modifies nan Windows registry to commencement a civilization work successful Safe Mode. |
| T1136.002 | Create Account: Domain Account | Embargo group creates its ain domain accounts. | |
| Defense Evasion | T1562.001 | Impair Defenses: Disable aliases Modify Tools | MDeployer, MS4Killer, and a BAT book disable information solutions. |
| T1562.009 | Impair Defenses: Safe Mode Boot | MDeployer and a BAT book reboot into Safe Mode. | |
| T1070.004 | Indicator Removal: File Deletion | MDeployer deletes dropped files during cleanup. | |
| T1112 | Modify Registry | MS4Killer modifies nan registry to load a morganatic susceptible driver. | |
| T1027.013 | Obfuscated Files aliases Information: Encrypted/Encoded File | Payloads loaded by MDeployer are RC4 encrypted. | |
| Discovery | T1135 | Network Share Discovery | Embargo ransomware performs web stock discovery. |
| T1083 | File and Directory Discovery | Embargo ransomware performs record and directory discovery. | |
| Impact | T1490 | Inhibit System Recovery | Embargo ransomware disables automatic Windows recovery. |
| T1486 | Data Encrypted for Impact | Embargo ransomware encrypts files connected compromised machines. |
Appendix: Example of MS4Killer termination process database (in alphabetical order)
| SentinelAgent.exe SentinelAgentWorker.exe SentinelServiceHost.exe SentinelStaticEngine.exe LogProcessorService.exe SentinelStaticEngineScanner.exe SentinelHelperService.exe SentinelBrowserNativeHost.exe LogCollector.exe SentinelMemoryScanner.exe SentinelRanger.exe SentinelRemediation.exe SentinelRemoteShellHost.exe SentinelScanFromContextMenu.exe CylanceSvc.exe ekrn.exe WRSA.exe |
WRSkyClient.x64.exe WRCoreService.x64.exe MsMpEng.exe dsa.exe ds_monitor.exe Notifier.exe coreServiceShell.exe firefox.exe MsMpEng.exe EPProtectedService.exe EPIntegrationService.exe bdredline.exe EPSecurityService.exe EPUpdateService.exe ERAAgent.exe ekrn.exe |


 5 months ago
5 months ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·