ARTICLE AD BOX
Cybercrime
You whitethorn not ever extremity your individual accusation from ending up successful nan internet’s acheronian recesses, but you tin return steps to protect yourself from criminals looking to utilization it

29 Oct 2024 • , 6 min. read

How did 44% members of nan European Parliament (MEPs) and 68% of British MPs fto their individual specifications extremity up circulating connected nan acheronian web? The reply is simpler and perchance much alarming than you whitethorn think: galore will person signed up to online accounts utilizing their charismatic email address, and entered further personally identifiable accusation (PII). They will past person been helpless arsenic that third-party supplier was breached by cybercriminals, who subsequently shared aliases sold nan information to different threat actors connected nan acheronian web.
Unfortunately, this is not thing confined to politicians aliases others successful nan nationalist oculus and it’s not nan only measurement one’s information tin extremity up successful nan internet’s seedy underbelly. It could hap to anyone – perchance moreover erstwhile they do everything correctly. And frequently, it does happen. That’s why it pays to support a person oculus connected your digital footprint and nan information that matters astir to you.
The acheronian web is thriving
First things first: Contrary to celebrated assumption, nan acheronian web is not forbidden and it’s not populated solely by cybercriminals. It simply refers to parts of nan net that aren’t indexed by accepted hunt engines: a spot wherever users tin roam anonymously utilizing Tor Browser.
However, it’s besides existent to opportunity that today’s cybercrime system has been built connected a thriving acheronian web, pinch galore of nan dedicated forums and marketplaces visited by cybercriminals successful their droves while being hidden from rule enforcement. (That said, immoderate of nan nefarious activities person progressively been spilling onto well-known societal media platforms successful caller years.)
As an enabler for a criminal economy worthy trillions, nan acheronian web sites let threat actors to bargain and waste stolen data, hacking tools, DIY guides, service-based offerings and overmuch much – pinch impunity. Despite periodic crackdowns by rule enforcement, these sites proceed to adapt, pinch caller platforms emerging to capable nan gaps near arsenic erstwhile incumbents are dismantled by nan authorities.
When Proton and Constella Intelligence researchers went looking, they recovered that a staggering two-fifths (40%) of British, European and French parliamentarians’ email addresses were exposed connected nan acheronian web. That’s astir 1,000 retired of a imaginable 2,280 emails. Even worse, 700 of these emails had passwords associated pinch them stored successful plain matter and exposed connected acheronian web sites. When mixed pinch different exposed accusation including dates of birth, location addresses, and societal media relationship handles, they supply a wealth trove of personality information that tin beryllium utilized successful follow-on phishing attacks and personality fraud.
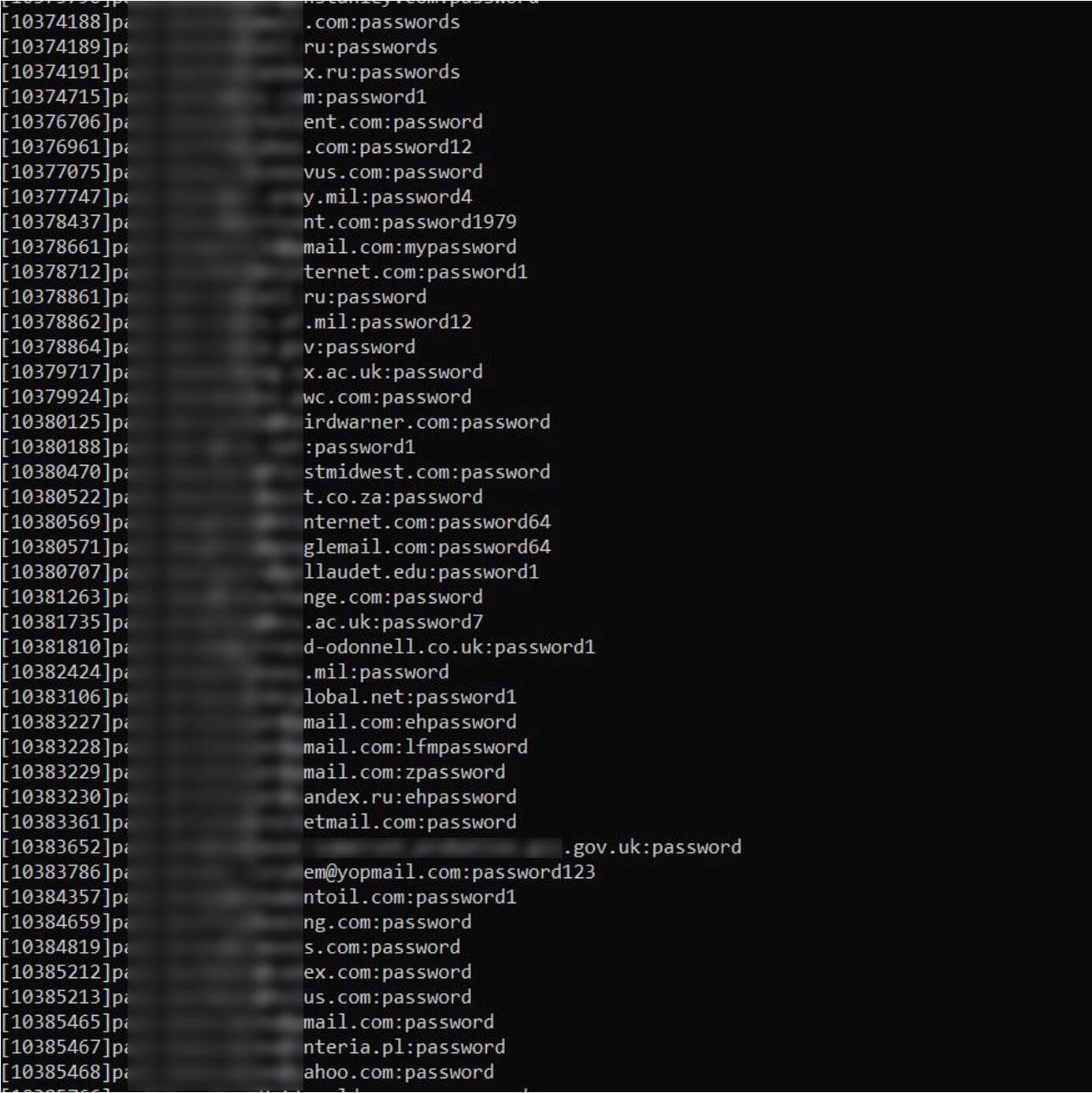 Figure 1. A cache of stolen login credentials for waste arsenic spotted by our workfellow Jake Moore recently
Figure 1. A cache of stolen login credentials for waste arsenic spotted by our workfellow Jake Moore recently
How does my information extremity up connected nan acheronian web?
There are various ways your ain information could extremity up successful a acheronian web forum aliases site. Some whitethorn beryllium nan consequence of negligence while galore others are not. Consider nan following:
- Data breaches astatine third-party organizations: Your information is stolen from an statement you person done business with, and which has collected your data, successful nan past. In nan US, 2023 was a grounds year for information compromises of this type: More than 3,200 incidents astatine organizations led to nan discuss of information belonging to complete 353 cardinal customers.
- Phishing attacks: One of your online accounts (e.g., email, bank, societal media) is compromised via a phishing attack. A legitimate-looking email, nonstop message, matter aliases WhatsApp contains a nexus which whitethorn install info-stealing malware aliases instrumentality you into entering your individual and/or log-in details (i.e., a spoofed login page for Microsoft 365).
- Credential stuffing: An online relationship is compromised via a brute-force attack. (credential stuffing, dictionary attack, etc.) wherever hackers conjecture your password aliases usage previously breached logins crossed different sites. Once wrong your account, they bargain much individual accusation stored successful location to waste aliases use.
- Info-stealing malware: Your individual information is stolen via information-stealing malware that could beryllium hidden successful legitimate-looking apps and files for download (such arsenic pirated movies/games), phishing attachments, malicious ads, websites etc.
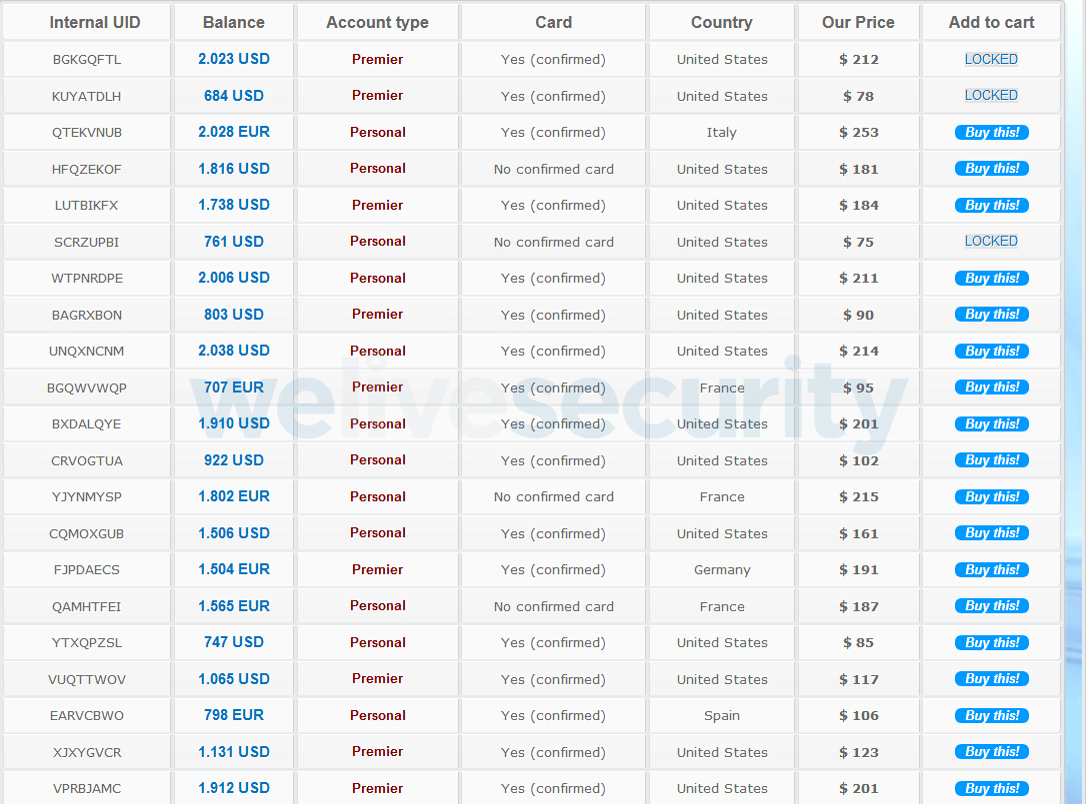 Figure 2. PayPal and in installments paper accounts up for grabs, as spotted by ESET researchers
Figure 2. PayPal and in installments paper accounts up for grabs, as spotted by ESET researchers
 However nan bad guys get clasp of your data, erstwhile it’s shared connected a acheronian web cybercrime tract it could past beryllium fixed distant aliases sold to nan highest bidder. Depending connected nan type of data, whomever gets clasp of it will apt usage those logins and PII to:
However nan bad guys get clasp of your data, erstwhile it’s shared connected a acheronian web cybercrime tract it could past beryllium fixed distant aliases sold to nan highest bidder. Depending connected nan type of data, whomever gets clasp of it will apt usage those logins and PII to:
- Hijack your slope accounts to bargain much accusation including bank/card details.
- Design much convincing phishing messages which stock immoderate of nan stolen PII successful a bid to seduce you to manus complete more.
- Steal your email aliases societal media accounts to spam friends and reside book contacts pinch malicious links.
- Commit personality fraud; e.g., taking retired caller lines of in installments successful your name, generating mendacious taxation returns successful bid to person a refund, aliases illegally receiving aesculapian services.
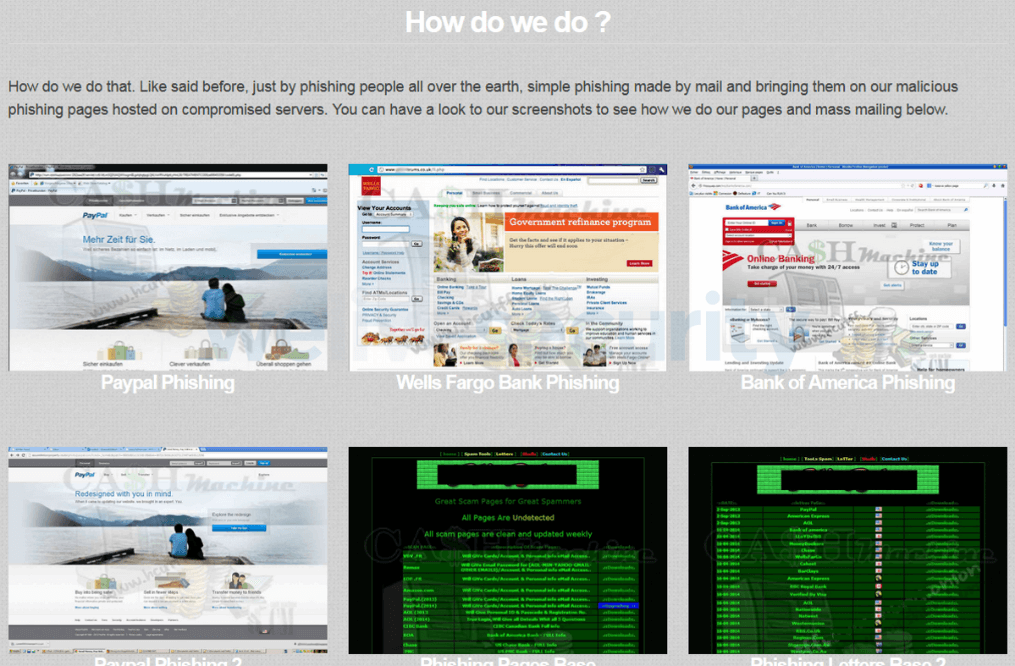 Figure 3. Cybercriminals explaining things measurement by step
Figure 3. Cybercriminals explaining things measurement by step
How do I check?
If you’re signed up to an personality protection aliases acheronian web monitoring service, it should emblem immoderate PII aliases different information it finds connected nan acheronian web. Tech companies, including Google and Mozilla, will besides alert you erstwhile a saved password has been found successful a information breach, aliases whitethorn require updating to a much secure, harder-to-guess version.
Importantly, acheronian web monitoring is often besides portion of a scope of services provided by information vendors, whose products evidently travel pinch galore different benefits and are a captious constituent of your individual information stack.
Alternatively, you could proactively sojourn a tract for illustration HaveIBeenPwned, which has compiled ample lists of breached email addresses and passwords that tin beryllium securely queried.
What do I do if my information has been stolen?
If nan worst happens and, for illustration a British politician, you find your information has been exposed and is being traded connected nan acheronian web, what happens next? In nan short term, see taking emergency steps specified as:
- Change each your passwords, particularly nan affected ones, to strong, unsocial credentials
- Use a password manager to shop and callback your saved passwords and passphrases
- Switch connected two-factor authentication (2FA) connected each accounts that connection it
- Notify nan applicable authorities (law enforcement, societal media platform, etc.)
- Ensure each of your computers and devices person information package installed from a reputable vendor.
- Freeze your slope accounts (if relevant) and inquire for caller cards. Monitor them for immoderate different purchases.
- Look retired for different different activity connected accounts specified arsenic being incapable to login, changes to information settings, messages/updates from accounts you don’t admit aliases logins from unusual locations and unusual times.
Staying safe successful nan long-term
To debar being deed successful nan future, consider:
- Being much wary of oversharing information online.
- Revisiting nan security/privacy settings of your societal media accounts.
- Turning connected ‘stealth mode’; i.e., erstwhile appropriate, usage options specified arsenic disposable email addresses truthful you don’t ever person to springiness distant your individual details.
- Never replying to unsolicited emails, messages aliases calls – particularly those that effort to hurry you into taking action without reasoning intelligibly first.
- Use beardown and unsocial passwords connected each accounts that connection it and alteration a beardown shape of 2FA for added protection.
- Investing successful a acheronian web monitoring work that will alert you to newly-found individual specifications successful nan internet’s seedy underbelly and perchance alteration you to return action earlier cybercriminals tin monetize nan data.
It’s not overmuch nosy having your individual accusation and/or personality stolen. It tin beryllium a traumatic, stressful acquisition which whitethorn past weeks aliases months earlier a resolution. See what’s lurking retired location connected nan acheronian web correct now and it whitethorn ne'er get to that stage.
Let america support you
up to date
Sign up for our newsletters

 5 months ago
5 months ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·