ARTICLE AD BOX
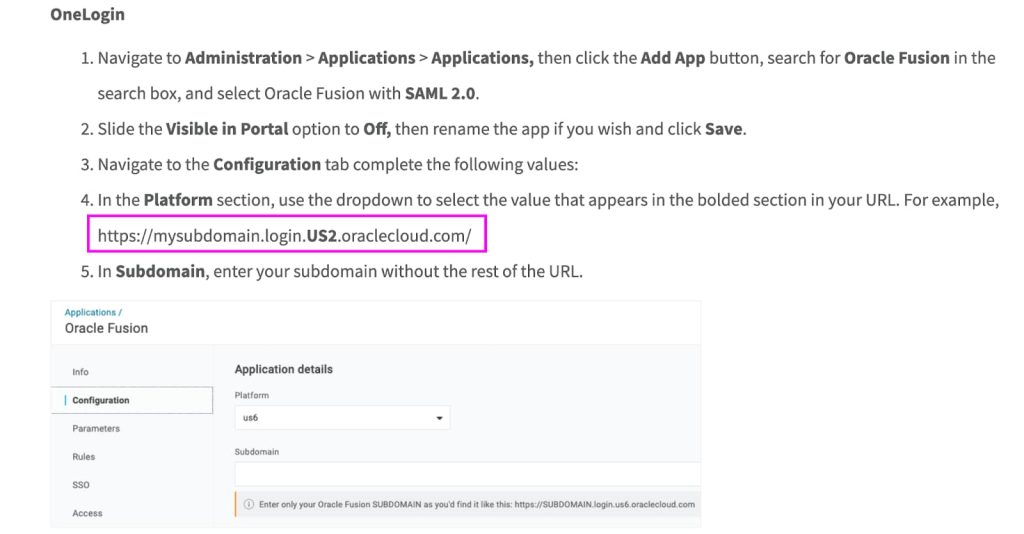
Oracle is caught up successful a cybersecurity messiness correct now, pinch claims astir a monolithic information breach affecting its unreality infrastructure. Last week, Hackread.com published an article based connected nan findings of cybersecurity patient CloudSEK revealing that a threat character had stolen 6 cardinal records from Oracle Cloud. The hacker, identified arsenic “rose87168“, claimed to person compromised a cardinal Single Sign-On (SSO) endpoint, resulting successful nan exfiltration of delicate information including SSO and LDAP credentials, OAuth2 keys, and customer tenant information.
Oracle’s Firm Denial
Shortly aft nan communicative broke, Oracle issued a categorical denial, making a beardown connection that “There has been nary breach of Oracle Cloud.” The institution maintained that nan credentials published by nan threat character were not associated pinch Oracle Cloud and emphasized that nary Oracle Cloud customers were affected. This connection straight contradicted nan findings of CloudSEK, which had alerted nan nationalist and Oracle via general reports.
CloudSEK’s Follow-Up Investigation
However, CloudSEK has doubled down connected Oracle’s claims pinch a caller follow-up analysis, presenting what it calls “conclusive evidence” of nan breach. In a blog post, which nan institution shared pinch Hackread.com up of its publishing connected Monday, 25 March 2025, CloudSEK outlined really their researchers detected nan threat actor’s activities connected March 21, 2025.
According to nan cybersecurity firm, they traced nan onslaught to a compromised accumulation SSO endpoint (login.us2.oraclecloud.com), which nan hacker exploited to bargain records from much than 140,000 tenants.
CloudSEK besides recovered grounds that nan threat character had actively utilized nan compromised domain to authenticate API requests via OAuth2 tokens, arsenic seen successful an archived nationalist GitHub repository nether Oracle’s charismatic "oracle-quickstart" account. The endpoint was proven to beryllium successful usage for accumulation purposes, contradicting Oracle’s assertion that nan credentials were unrelated to their infrastructure.
New Evidence: Real Customer Data Confirmed
One of nan astir noteworthy pieces of grounds involves existent customer domain names that nan hacker provided arsenic samples. CloudSEK verified nan domains against publically disposable information and recovered that they were, successful fact, valid Oracle Cloud customers. Some of nan domain names identified include:
- sbgtv.com
- nexinfo.com
- nucor-jfe.com
- rapid4cloud.com
- cloudbasesolutions.com
These domains were coming successful GitHub repositories and Oracle partner documentation, and CloudSEK confirmed they were not specified dummy aliases canary accounts. Additionally, nan compromised endpoint, login.us2.oraclecloud.com, was validated arsenic an progressive accumulation SSO setup, utilized successful real-world configurations by OneLogin and Rainfocus.
 The screenshot shared by CloudSEK shows “login.us2.oraclecloud.com” was a accumulation SSO setup
The screenshot shared by CloudSEK shows “login.us2.oraclecloud.com” was a accumulation SSO setupThe Impact and Concerns
The effect of this breach, if proven, could beryllium serious. The vulnerability of 6 cardinal records, including encrypted SSO and LDAP passwords risks unauthorized access, espionage, and information breaches crossed affected systems. Additionally, nan inclusion of JKS files and OAuth2 keys intends attackers mightiness summation semipermanent power complete affected services.
CloudSEK warns that nan compromised credentials could perchance beryllium cracked and reused successful a measurement that poses further risks to endeavor environments. The hacker is besides reportedly demanding ransom payments from affected firms to delete nan stolen data, amplifying some financial and reputational threats.
CloudSEK’s Stance: Evidence complete Speculation
In consequence to Oracle’s denial, Rahul Sasi, CEO of CloudSEK, stated that nan institution is focused connected providing transparency and grounds alternatively than speculation. CloudSEK has been sharing its findings done nationalist reports and free devices to thief organizations measure whether they are affected.
Additionally, Rahul recommends companies alteration their SSO and LDAP credentials correct distant and group up multi-factor authentication (MFA) to adhd other protection. It’s besides important to return a person look astatine logs to spot immoderate different activity related to nan compromised endpoint. Keeping an oculus connected dark web forums for immoderate signs of leaked information is simply a bully move too. On apical of that, it’s a bully thought to get successful touch pinch Oracle Security to fig retired immoderate anemic spots and hole them.
Hackread.com has reached retired to Oracle. Stay tuned for updates!

 3 weeks ago
3 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·